Difference between revisions of "Requirements"
| (13 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | < | + | <table border="3"> |
| − | + | <tr><td> | |
| + | <table> | ||
| + | <tr> | ||
| + | <td width="60%"><font color="#246196">'''Welcome to the initial version of the EITBOK wiki. Like all wikis, it is a work in progress and may contain errors. We welcome feedback, edits, and real-world examples. [[Main_Page#How to Make Comments and Suggestions|Click here]] for instructions about how to send us feedback.''' </font></td> | ||
| + | <td width="20%">[[File:Ieee logo 1.png|100px|center]]</td> | ||
| + | <td width="20%"> [[File:Acm_logo_3.png|175px|center]]</td> | ||
| + | </tr></table> | ||
| + | </td></tr></table> | ||
| + | <p> </p> | ||
<h2>Introduction</h2> | <h2>Introduction</h2> | ||
| − | <p>Requirements development and design uses a variety of elicitation techniques to gather a set of actionable, | + | <p>Requirements development and design uses a variety of elicitation techniques to gather a set of actionable, measurable, and traceable criteria (''requirements''). Some of these criteria are artifacts from previous work done, as described in the chapters on [http://eitbokwiki.org/Strategy_and_Governance Strategy and Governance] and [http://eitbokwiki.org/Change_Initiatives Change Initiatives]. The rest of the criteria are gathered by the requirements team to prepare for the construction (solution implementation) phase, described in the [http://eitbokwiki.org/Construction Construction chapter]. </p> |
| − | <p>The requirements are said to belong to a particular ''[http://eitbokwiki.org/Glossary#domain domain]'' | + | <p>The requirements are said to belong to a particular ''[http://eitbokwiki.org/Glossary#domain domain]''—a specific sphere of activity or knowledge. A domain can correspond to the boundaries of an organization, a job function, or even a particular task. </p> |
<p>These criteria/requirements are collected, analyzed, categorized, and documented in a series of artifacts, such as use cases, [http://eitbokwiki.org/Glossary#acceptance_criteria acceptance criteria], mockups, and market requirements. Finally, the criteria are morphed into a design for a product (good or service) or a set of product capabilities that meet the identified customer or organizational needs. </p> | <p>These criteria/requirements are collected, analyzed, categorized, and documented in a series of artifacts, such as use cases, [http://eitbokwiki.org/Glossary#acceptance_criteria acceptance criteria], mockups, and market requirements. Finally, the criteria are morphed into a design for a product (good or service) or a set of product capabilities that meet the identified customer or organizational needs. </p> | ||
| − | <p>A design is a proposed ''[http://eitbokwiki.org/Glossary#solution solution]'', as described by a set of documents (and potentially, prototypes) that meets currently understood technical, | + | <p>A design is a proposed ''[http://eitbokwiki.org/Glossary#solution solution]'', as described by a set of documents (and potentially, prototypes) that meets currently understood technical, non-functional, and business requirements. In essence, a solution specifies a set of changes to the current state of an enterprise that enables the enterprise to meet a need, solve a problem, or take advantage of an opportunity. In the requirements analysis phase of the project, the conceptual and logical designs of the solution are developed. The detailed technical design is created during the construction phase (see the [http://eitbokwiki.org/Construction Construction chapter]).</p> |
| − | <p>Be aware that as the requirement analysis process is carried out, the requirements might change, both because of improved understanding of the domain and because of changing organizational conditions. This is especially | + | <p>Be aware that as the requirement analysis process is carried out, the requirements might change, both because of improved understanding of the domain and because of changing organizational conditions. This is especially true during projects that use iterative (agile) development approaches, where only part of the domain is worked on at one time. </p> |
<p>The ''scope'' of the solution defines the portion of the domain that is part of the implementation. It is typically narrower than the full scope of the domain within which it is implemented. </p> | <p>The ''scope'' of the solution defines the portion of the domain that is part of the implementation. It is typically narrower than the full scope of the domain within which it is implemented. </p> | ||
<p>This chapter covers both the process of collecting the criteria as well as creating and managing the artifacts that the result from the requirements process.</p> | <p>This chapter covers both the process of collecting the criteria as well as creating and managing the artifacts that the result from the requirements process.</p> | ||
| − | |||
<h2>Goals and Principles </h2> | <h2>Goals and Principles </h2> | ||
<p>The goal for the requirements analysis and design phase is to collect all the data information required to develop an effective solution for the problem domain. In general, there are several principles that need to be followed during this process, including:</p> | <p>The goal for the requirements analysis and design phase is to collect all the data information required to develop an effective solution for the problem domain. In general, there are several principles that need to be followed during this process, including:</p> | ||
<ul> | <ul> | ||
| − | <li>Align requirements to the enterprise's strategies and goals as well as [http://eitbokwiki.org/Glossary#eit] | + | <li>Align requirements to the enterprise's strategies and goals as well as [http://eitbokwiki.org/Glossary#eit] EIT strategies and goals, as defined in the [http://eitbokwiki.org/Strategy_and_Governance Strategy and Governance chapter]. </li> |
<li>Ensure that the proposed conceptual and logical solution designs meet the objectives of the requirements.</li> | <li>Ensure that the proposed conceptual and logical solution designs meet the objectives of the requirements.</li> | ||
<li>Develop requirements that are clear, unambiguous, usable, current, feasible, well-formed, and can be validated and traced.</li> | <li>Develop requirements that are clear, unambiguous, usable, current, feasible, well-formed, and can be validated and traced.</li> | ||
| Line 21: | Line 28: | ||
</ul> | </ul> | ||
<h2>Context Diagram</h2> | <h2>Context Diagram</h2> | ||
| − | [[File:10 Requirements CD.png|700px]] | + | <p>[[File:10 Requirements CD.png|700px]]<br />'''Figure 1. Context Diagram for Requirements Development and Design'''</p> |
| − | < | + | <p>Requirements development and design starts with a number of inputs. Many of these inputs are requirements defined by senior management. They indicate the enterprise's plans and goals. They specify the desired business and EIT architecture. Inputs usually include a use case or scenario that describes in general terms the [http://eitbokwiki.org/Glossary#solution solution] that management is looking for. Along with the enterprise requirements, there should be a list of individuals who can supply important pieces of information or authority for the project. </p> |
| − | <p>Requirements development and design starts with a number of inputs. Many of these inputs are requirements defined by senior management. They indicate the | + | <p>The requirements project team often consists of several people who have a variety of skills including business analysis, solutions architecture, data modeling, user interface design, and project management. This team collects both high-level and detailed information during the project, and then documents, analyzes, and ensures that the solution chosen meets the enterprise requirements given to them by management. The team's output should give the implementation project team enough information to create and deliver the solution. It should also give the [http://eitbokwiki.org/Glossary#stakeholder stakeholder] organizations the information that they need to prepare for the changes required to their business processes.</p> |
| − | <p>The requirements project team often consists of several people who have a variety of skills including business analysis, solutions architecture, data modeling, user interface design, and project management. This team collects both high-level and detailed information during the project, and then documents, analyzes, and ensures that the solution chosen meets the enterprise requirements given to them by management. The | + | |
<h2>Requirements Analysis and Design Process</h2> | <h2>Requirements Analysis and Design Process</h2> | ||
<p>The requirements process includes several different activities:</p> | <p>The requirements process includes several different activities:</p> | ||
| Line 36: | Line 42: | ||
<li>Reviewing and validating the requirements with stakeholders</li> | <li>Reviewing and validating the requirements with stakeholders</li> | ||
<li>Creating a sufficiently detailed conceptual and [http://eitbokwiki.org/Glossary#logical_design logical designs] for the solution that is consistent with the requirements</li> | <li>Creating a sufficiently detailed conceptual and [http://eitbokwiki.org/Glossary#logical_design logical designs] for the solution that is consistent with the requirements</li> | ||
| − | <li>Reviewing and validating the design with the implementation team </li> | + | <li>Reviewing and validating the design with the implementation team</li> |
</ul> | </ul> | ||
| − | <p>Although these activities seem to follow one another, it is often the case that in the middle of a project all these activities are going on | + | <p>Although these activities seem to follow one another, it is often the case that in the middle of a project all these activities are going on simultaneously—often on different parts of the domain.</p> |
<p>In some strategies, the requirements development team first lays out the high-level architecture of the conceptual design. The team then fills out the requirements feature by feature or function by function. This process is often used in iterative projects, so that parts of the system can be under construction while other parts of the domain are being specified.</p> | <p>In some strategies, the requirements development team first lays out the high-level architecture of the conceptual design. The team then fills out the requirements feature by feature or function by function. This process is often used in iterative projects, so that parts of the system can be under construction while other parts of the domain are being specified.</p> | ||
| − | <p>For each of these activities, there | + | <p>For each of these activities, there isn't just one technique to use or list of things to accomplish. The size, complexity, and type of the project influences how the team steps through the requirements phase, what techniques the team uses to collect the requirements, and what artifacts the team creates to represent (communicate) the domain information to the stakeholders.</p> |
<h3>Requirement Types</h3> | <h3>Requirement Types</h3> | ||
<p>Requirements fall into several categories. No one category is more important than another to define a successful solution.</p> | <p>Requirements fall into several categories. No one category is more important than another to define a successful solution.</p> | ||
| + | <p>[[File:Figure8.2_Bars.jpg|370px]]<br />'''Figure 2. Types of Requirements'''</p> | ||
<ul> | <ul> | ||
<li>'''Business requirements''' are the critical goals, objectives, and needs of an enterprise that must be met by the solution. They should indicate why the project was initiated and what metrics are used to measure the success of the solution.</li> | <li>'''Business requirements''' are the critical goals, objectives, and needs of an enterprise that must be met by the solution. They should indicate why the project was initiated and what metrics are used to measure the success of the solution.</li> | ||
<li>'''Stakeholder requirements''' are statements of the needs of a set of stakeholders associated with the project. They describe the needs of each stakeholder affected by the solution as well as how the stakeholder interacts with the solution. Often stakeholder requirements are a bridge between the business requirements and the detailed functional solution requirements.</li> | <li>'''Stakeholder requirements''' are statements of the needs of a set of stakeholders associated with the project. They describe the needs of each stakeholder affected by the solution as well as how the stakeholder interacts with the solution. Often stakeholder requirements are a bridge between the business requirements and the detailed functional solution requirements.</li> | ||
| − | <li>'''Solution requirements''' describe the specific characteristics of the solution (such as an application or an infrastructure build-out) that meet the requirements of both the enterprise and the stakeholders. The development of solution requirements constitutes the bulk of the requirements analysis process. <br />Solution requirements fall into two categories: functional and non-functional requirements. ''Functional requirements'' are those that describe specific behaviors or functions of the implemented solution (calculations, technical details, data manipulation and processing, and behavioral requirements). ''Non-functional requirements'' specify additional criteria often called qualities or just | + | <li>'''Solution requirements''' describe the specific characteristics of the solution (such as an application or an infrastructure build-out) that meet the requirements of both the enterprise and the stakeholders. The development of solution requirements constitutes the bulk of the requirements analysis process. <br />Solution requirements fall into two categories: functional and non-functional requirements. ''Functional requirements'' are those that describe specific behaviors or functions of the implemented solution (calculations, technical details, data manipulation and processing, and behavioral requirements). ''Non-functional requirements'' specify additional criteria often called qualities or just "-ilities" (execution performance, constraints, reliability goals, usability, security, testability, maintainability, extensibility, and scalability). The [http://eitbokwiki.org/Quality EIT Quality chapter] describes the -ilities. Both types of solution requirements are important to ascertain and document.</li> |
| − | <li>'''Transition requirements''' describe the capabilities that the solution must have to facilitate the transition from the current state of the enterprise to the desired state. Transition requirements are fulfilled when the transition to the new state is complete, and are associated with issues such as filling workforce skill gaps, creating new resources, and converting data to a new format. | + | <li>'''Transition requirements''' describe the capabilities that the solution must have to facilitate the transition from the current state of the enterprise to the desired state. Transition requirements are fulfilled when the transition to the new state is complete, and are associated with issues such as filling workforce skill gaps, creating new resources, and converting data to a new format. </li> |
</ul> | </ul> | ||
<h2>Enterprise Analysis and EIT Change Initiative Inputs</h2> | <h2>Enterprise Analysis and EIT Change Initiative Inputs</h2> | ||
| − | <p>Requirements analysis typically starts with a request from the group who is in charge of enterprise change initiatives. In the best of all possible worlds, that request is a clear definition of the project including a set of enterprise-level artifacts (such as business and use cases, strategic plans, customer need descriptions, results of a [http://eitbokwiki.org/Glossary#swot SWOT] analysis) that describe the problem and the end product or functionality desired, and guide the project to its fruition. </p> | + | <p>Requirements analysis typically starts with a request from the group who is in charge of enterprise change initiatives. In the best of all possible worlds, that request is a clear definition of the project including a set of enterprise-level artifacts (such as business and use cases, strategic plans, customer need descriptions, and results of a [http://eitbokwiki.org/Glossary#swot SWOT] analysis) that describe the problem and the end product or functionality desired, and guide the project to its fruition. </p> |
<p>Unfortunately, few projects start the requirements phase with all this information collected and documented. So the requirements team must first gather the existing information and then fill in the holes. Without the enterprise-level requirements, a project cannot be successful, because there is no target and no meaningful way to measure success.</p> | <p>Unfortunately, few projects start the requirements phase with all this information collected and documented. So the requirements team must first gather the existing information and then fill in the holes. Without the enterprise-level requirements, a project cannot be successful, because there is no target and no meaningful way to measure success.</p> | ||
<p>The requirements team needs the following information, which comes out of the enterprise strategy work (see the [http://eitbokwiki.org/Strategy_and_Governance Strategy and Governance chapter]) and the change initiative effort (see the [http://eitbokwiki.org/Change_Initiatives Change Initiatives chapter]):</p> | <p>The requirements team needs the following information, which comes out of the enterprise strategy work (see the [http://eitbokwiki.org/Strategy_and_Governance Strategy and Governance chapter]) and the change initiative effort (see the [http://eitbokwiki.org/Change_Initiatives Change Initiatives chapter]):</p> | ||
| Line 62: | Line 69: | ||
<p>There are a number of activities that can be extremely useful in collecting this information, including:</p> | <p>There are a number of activities that can be extremely useful in collecting this information, including:</p> | ||
<ul> | <ul> | ||
| − | <li>'''Gap analysis''' (or needs assessment) is a technique that explores and describes the gap between the current actual enterprise or group performance (the | + | <li>'''Gap analysis''' (or needs assessment) is a technique that explores and describes the gap between the current actual enterprise or group performance (the "as is" state) and the desired performance with the solution (the "to be" state). This analysis focuses on the use of resources such as time, money, and workforce to produce the organization's desired level of performance. Gap analysis is a good tool to help define the solutions approach and scope. </li> |
<li>A '''[http://eitbokwiki.org/Glossary#swot strengths, weaknesses, opportunities, and threads (SWOT)]''' analysis for the specific area of concern (often a specific objective) is an excellent tool to help focus the discussion on creating a solution that can have the optimum positive effect for the organization. It can guide requirements identification and analysis at all levels.</li> | <li>A '''[http://eitbokwiki.org/Glossary#swot strengths, weaknesses, opportunities, and threads (SWOT)]''' analysis for the specific area of concern (often a specific objective) is an excellent tool to help focus the discussion on creating a solution that can have the optimum positive effect for the organization. It can guide requirements identification and analysis at all levels.</li> | ||
<li>'''Determining solution approach''' is an activity that investigates the most viable approach for a solution. It examines the business needs, organizational processes, and required capabilities, and ends up with a description of the approach that should be taken to implement the new set of capabilities. It requires documenting assumptions and constraints; ranking approaches based upon performance improvement estimations and benchmarking; and collecting performance requirements such as availability, response time, accessibility, and maximum throughput.</li> | <li>'''Determining solution approach''' is an activity that investigates the most viable approach for a solution. It examines the business needs, organizational processes, and required capabilities, and ends up with a description of the approach that should be taken to implement the new set of capabilities. It requires documenting assumptions and constraints; ranking approaches based upon performance improvement estimations and benchmarking; and collecting performance requirements such as availability, response time, accessibility, and maximum throughput.</li> | ||
</ul> | </ul> | ||
<h2>Domain Elicitation</h2> | <h2>Domain Elicitation</h2> | ||
| − | <p>A large portion of the requirements development process is associated with simply collecting the right information, referred to as ''[http://eitbokwiki.org/Glossary#domain_elic domain elicitation]''. | + | <p>A large portion of the requirements development process is associated with simply collecting the right information, referred to as ''[http://eitbokwiki.org/Glossary#domain_elic domain elicitation]''. This activity is associated with gathering information from [http://eitbokwiki.org/Glossary#sme subject matter experts (SMEs)], stakeholders, or consumers about how the solution should function. Let's say that the solution is to provide expertise or guidance to a junior repair technician. The team must collect the repair expertise and guidance from an SME so that the solution can provide the correct repair guidance to the user.</p> |
<p>There are entire books written about domain elicitation or knowledge acquisition as it is referred to in some areas. [[#One|[1]]] Strong interviewing skills are a requirement for the team members. The interviewer develops an expertise over time for guiding the SME to deliver useful information in an efficient manner. In this section, we list a few basic approaches that can help.</p> | <p>There are entire books written about domain elicitation or knowledge acquisition as it is referred to in some areas. [[#One|[1]]] Strong interviewing skills are a requirement for the team members. The interviewer develops an expertise over time for guiding the SME to deliver useful information in an efficient manner. In this section, we list a few basic approaches that can help.</p> | ||
<h3>Plan Your Approach and Prepare for the Elicitation</h3> | <h3>Plan Your Approach and Prepare for the Elicitation</h3> | ||
| Line 82: | Line 89: | ||
<p>There are several tools that are extremely useful during the elicitation process:</p> | <p>There are several tools that are extremely useful during the elicitation process:</p> | ||
<ul> | <ul> | ||
| − | <li>'''Scenarios''' | + | <li>'''Scenarios'''—It can be very useful to go through a number of scenarios in detail. A scenario is an end-to-end walk through of a process, such as identifying a fault to repair, or maybe purchasing car insurance. It examines one path through the process and also includes rationale for any decisions or distinctions that are made during the process. The rationale can indicate why particular questions are asked of a user, why the solution takes a particular path, or why certain recommendations are made to a user. Document any paths that should not be used, as well.<br />The amount of detail that you need to collect in the scenario depends upon the scope of the solution. At times, scenarios can be the most critical tool in the elicitation toolbox, because they provide not only a means to collect the information to create the solution, but also provide a basis for creating test cases for testing the solution after it is implemented. <br />A domain might be small enough that only a couple scenarios are sufficient to guide the solution definition; however, some projects are large enough to require several hundred scenarios to cover the entire domain.<br />Scenarios can become use cases in the requirements document.</li> |
| − | <li>'''Observe people working or doing the activity''' | + | <li>'''Observe people working or doing the activity'''—Sometimes people cannot describe what they do. For example, try to tell someone how to tie their shoes without looking at your own shoes. Instead, the elicitation team can watch the stakeholder or SME perform the task in question. <br />This technique is just a special instance of a case study. Asking clarifying questions while the SME performs the task can provide the critical knowledge required to develop the solution. This technique also identifies data sources and job aids that people use to perform the task that could become an important part of the solution.</li> |
| − | <li>'''Stories''' | + | <li>'''Stories'''—SMEs often tell stories about what has happened in the past that provide useful information about both functional and non-function requirements. They might talk about an interaction with a customer or a problem that occurs frequently. The difficulty with stories is that people often ramble on without saying anything useful. The discussion is fun to listen to, but it doesn't provide information that is useful to the final solution. It is up to the interviewer to keep the discussion focused on useful information. A skillful interviewer gently guides the storyteller back to the topic.</li> |
</ul> | </ul> | ||
<h3>Document the Elicitation Results</h3> | <h3>Document the Elicitation Results</h3> | ||
| − | <p>Notes about | + | <p>Notes about elicitation sessions are very important. They need to be detailed, because it is often difficult to tell what information is important during or shortly after the interview. Sometimes, the team discovers that the SME dropped a true gem of information that is not recognized for several weeks. If the notes are detailed, you can go back and pick up the additional information at a later time. It may be useful to have the note taker be someone who is not asking questions, so that each person can maintain focus on their specific activity. </p> |
<p>The notes become input for the requirements analysis process and for documenting the requirements. At times, the scenarios discussed in the interviews only require polishing at those later stages. </p> | <p>The notes become input for the requirements analysis process and for documenting the requirements. At times, the scenarios discussed in the interviews only require polishing at those later stages. </p> | ||
<p>Beyond documenting what you heard or saw during the elicitation process, you should also make notes about:</p> | <p>Beyond documenting what you heard or saw during the elicitation process, you should also make notes about:</p> | ||
| Line 98: | Line 105: | ||
</ul> | </ul> | ||
<h2>Requirements Analysis</h2> | <h2>Requirements Analysis</h2> | ||
| − | <p>After the information has been collected through the elicitation process, it needs to be analyzed. This analysis process takes a careful look at all the information and puts it in context with the other information (requirements) that | + | <p>After the information has been collected through the elicitation process, it needs to be analyzed. This analysis process takes a careful look at all the information and puts it in context with the other information (requirements) that has been collected. </p> |
<h3>The Requirements Analysis Process</h3> | <h3>The Requirements Analysis Process</h3> | ||
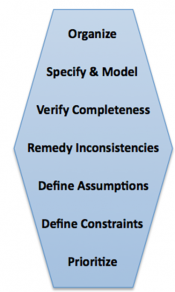
| − | <p>The analysis process can be described by a number of activities: organize, model, verify, remedy inconsistencies, define assumption, define constraints, prioritize, and ensure completeness. Although the type of project demands different amounts of time with each of these activities, all these activities are important for proper analysis of the information collected.</p> | + | <p>The analysis process can be described by a number of activities: organize, model, verify, remedy inconsistencies, define assumption, define constraints, prioritize, and ensure completeness. Although the type of project demands different amounts of time with each of these activities, all of these activities are important for the proper analysis of the information collected.</p> |
<h4>Organize</h4> | <h4>Organize</h4> | ||
| − | [[File:Figure8.3_Organize.png|right|175px|caption]] | + | <p>[[File:Figure8.3_Organize.png|right|175px|caption]]</p> |
<p>The most important activity is to organize the requirements (information) based upon type, level, and role. Typically, the information is organized into three groups:</p> | <p>The most important activity is to organize the requirements (information) based upon type, level, and role. Typically, the information is organized into three groups:</p> | ||
<ul> | <ul> | ||
| − | <li>'''Processes associated with the domain''' | + | <li>'''Processes associated with the domain'''—These are the steps in a flow of activities, whether high or low level. This information is modeled in flowcharts, Gantt charts, sequence diagrams, state diagrams, or other representations.</li> |
| − | <li>'''The data required for or produced by the processes or tasks in the domain''' | + | <li>'''The data required for or produced by the processes or tasks in the domain'''—Data can represent information at a number of levels. Low-level data consists of numbers, names, and other base-level information. High-level data consists of mathematical results or logical conclusions made based upon the base-level data. Data models are critical for designing databases and the solution's data structures.</li> |
| − | <li>'''The business rules that drive the solution''' | + | <li>'''The business rules that drive the solution'''—Business rules are statements that indicate whether an actor can or cannot do something. They also provide the conditions and criteria for making a decision. For example, "a user must have an account to make a purchase." In essence, a business rule is an implementation of a business requirement.</li> |
</ul> | </ul> | ||
<p>To describe all aspects of the information collected during elicitation, there are several different kinds of documents created, as described in the [[#ReqDoc|Requirements Documentation]] section. These documents need to be comprehensive, complete, consistent, and understood by all stakeholders. </p> | <p>To describe all aspects of the information collected during elicitation, there are several different kinds of documents created, as described in the [[#ReqDoc|Requirements Documentation]] section. These documents need to be comprehensive, complete, consistent, and understood by all stakeholders. </p> | ||
| Line 113: | Line 120: | ||
<p>Specifying and modeling the information takes the organization process to another level. The goal of this activity is to start formulating the details of the solution. Often this activity describes and models information, such as:</p> | <p>Specifying and modeling the information takes the organization process to another level. The goal of this activity is to start formulating the details of the solution. Often this activity describes and models information, such as:</p> | ||
<ul> | <ul> | ||
| − | <li>Current | + | <li>Current ("as is") state of the organization</li> |
| − | <li>Needs and desires of the stakeholders for the ( | + | <li>Needs and desires of the stakeholders for the ("to be") solution</li> |
<li>Models of the business logic currently being used</li> | <li>Models of the business logic currently being used</li> | ||
<li>Details about the data, and how it needs to be defined and organized</li> | <li>Details about the data, and how it needs to be defined and organized</li> | ||
<li>How the data flows through the processes</li> | <li>How the data flows through the processes</li> | ||
<li>How decisions are made and the contexts that they are made in</li> | <li>How decisions are made and the contexts that they are made in</li> | ||
| − | <li>How the processes flow and what | + | <li>How the processes flow and what intermediate states can be identified</li> |
| − | <li>Under what scope | + | <li>Under what scope each of the requirements, data, and processes applies</li> |
</ul> | </ul> | ||
<p>The result of the specification and modeling task are a host of analysis documents described in [[#ReqDoc|Requirements Documentation]], including state diagrams, data modeling diagrams, business rule documents, sequence diagrams, and use cases. [[#Seven|[7]]] [[#Eight|[8]]]</p> | <p>The result of the specification and modeling task are a host of analysis documents described in [[#ReqDoc|Requirements Documentation]], including state diagrams, data modeling diagrams, business rule documents, sequence diagrams, and use cases. [[#Seven|[7]]] [[#Eight|[8]]]</p> | ||
<h4>Verify Completeness</h4> | <h4>Verify Completeness</h4> | ||
| − | <p>One of the parts of the analysis process is verifying that you have collected all the information you need. It is often the case that the team discovers during analysis or documentation that they | + | <p>One of the parts of the analysis process is verifying that you have collected all the information you need. It is often the case that the team discovers during analysis or documentation that they don't have everything that they need to define a solution; there are holes in their information that can block the implementation team from finishing the solution. While the completion verification process is not easy, it is critical.</p> |
<h4>Identify and Remedy Inconsistencies</h4> | <h4>Identify and Remedy Inconsistencies</h4> | ||
| − | <p>Not only is data often incomplete, it is also often inconsistent or even contradictory. | + | <p>Not only is data often incomplete, it is also often inconsistent or even contradictory. The inconsistencies can be obvious; however, at times the inconsistencies are subtle, such as data being used as an integer in one context and a real number in another. Business rules might be contradictory in subtle ways, hiding the inconsistency until lower-level requirements based upon the inconsistent rules are identified as being inconsistent.</p> |
<p>It is the role of the analyst to identify inconsistencies in the process as soon as possible, and then to go back to the sources to get the inconsistencies resolved. There are several techniques, such as using quasi-classical logic to resolve the issues. [[#Two|[2]]] </p> | <p>It is the role of the analyst to identify inconsistencies in the process as soon as possible, and then to go back to the sources to get the inconsistencies resolved. There are several techniques, such as using quasi-classical logic to resolve the issues. [[#Two|[2]]] </p> | ||
<h4>Define Assumptions</h4> | <h4>Define Assumptions</h4> | ||
<p>Assumptions are factors upon which design decisions are made, which are believed to be true, but have not been or cannot be confirmed at the time of collecting the requirements. Assumptions can affect all aspects of a project, and their associated uncertainty adds a certain degree of [http://eitbokwiki.org/Glossary#risk risk] to the project. It is crucial to identify, document, and attempt to confirm all assumptions in order to manage their associated risks. Assumptions are one of the major factors associated with problem tracking and risk analysis. </p> | <p>Assumptions are factors upon which design decisions are made, which are believed to be true, but have not been or cannot be confirmed at the time of collecting the requirements. Assumptions can affect all aspects of a project, and their associated uncertainty adds a certain degree of [http://eitbokwiki.org/Glossary#risk risk] to the project. It is crucial to identify, document, and attempt to confirm all assumptions in order to manage their associated risks. Assumptions are one of the major factors associated with problem tracking and risk analysis. </p> | ||
| − | <p>Some assumptions are | + | <p>Some assumptions are high risk. For example, if you are running an app on a mobile device, you might have an assumption that Wi-Fi is available. Or maybe, your app depends on the user being able to hear the device. If either of these assumptions is incorrect, the application doesn't work or isn't useful as designed.</p> |
<p>Assumptions can also be low risk. These are assumptions that define boundary or likely conditions for the solution, such as how a user is likely to respond to a particular situation.</p> | <p>Assumptions can also be low risk. These are assumptions that define boundary or likely conditions for the solution, such as how a user is likely to respond to a particular situation.</p> | ||
<h4>Define Constraints</h4> | <h4>Define Constraints</h4> | ||
| − | <p>During the project, it is typical to identify constraints on the solution. [http://eitbokwiki.org/Glossary#constraint Constraints] are restrictions or limitations on solutions | + | <p>During the project, it is typical to identify constraints on the solution. [http://eitbokwiki.org/Glossary#constraint Constraints] are restrictions or limitations on solutions imposed by outside influences, whether by the EIT infrastructure, organizational policies and culture, legal requirements for safety, privacy, budget, available resources, or schedule. It is critical to identify, document, and publish constraints as part of the problem-tracking process. Constraints figure heavily in the prioritization process.</p> |
<h4>Prioritize</h4> | <h4>Prioritize</h4> | ||
| − | <p>More often than anyone would like to admit, requirements conflict with one another. You might | + | <p>More often than anyone would like to admit, requirements conflict with one another. You might need some functionality but have no budget to implement it. You might have a requirement for putting the application on a smart phone or tablet, but it requires significantly more horsepower and space than is available on the device. </p> |
| − | <p>One of the tasks is to determine (and document) the relative importance of requirements based upon the value to the enterprise, business risk, technical risk, the difficulty to implement, or likelihood of success. Regulatory or policy compliance (legal) can also be a critical aspect. Even a | + | <p>One of the tasks is to determine (and document) the relative importance of requirements based upon the value to the enterprise, business risk, technical risk, the difficulty to implement, or likelihood of success. Regulatory or policy compliance (legal) can also be a critical aspect. Even a requirement's relationship to other requirements, such as a critical dependence, needs to be considered. </p> |
| − | <p>The difficulty with this task is that it often requires stakeholder | + | <p>The difficulty with this task is that it often requires stakeholder approval—maybe approval from all the stakeholders. And, they often have differing opinions on the relative value and risk associated with requirements. Often there are "non-negotiable" demands and unrealistic tradeoffs that need to be addressed. </p> |
| − | <p>Several techniques are particularly helpful in this area, such as decision analysis, MoSCoW (acronym for Must have, Should have, Could have, and Would like but | + | <p>Several techniques are particularly helpful in this area, such as decision analysis, MoSCoW (acronym for Must have, Should have, Could have, and Would like but won't get) analysis, risk analysis, time boxing, and budgeting.</p> |
<h4>Ensure Completeness of the Analysis</h4> | <h4>Ensure Completeness of the Analysis</h4> | ||
<p>All of this analysis is useless if the analyst team does not make sure that each requirement is well-formed and completely specified, as described in [[#WellFormedReq|Qualities of Well-Formed Requirements]]. </p> | <p>All of this analysis is useless if the analyst team does not make sure that each requirement is well-formed and completely specified, as described in [[#WellFormedReq|Qualities of Well-Formed Requirements]]. </p> | ||
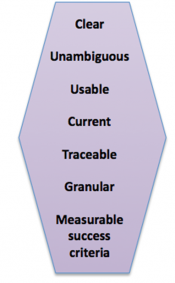
<div id="WellFormedReq"></div><h3>Qualities of Well-Formed Requirements</h3> | <div id="WellFormedReq"></div><h3>Qualities of Well-Formed Requirements</h3> | ||
| − | [[File:Figure8.4_Qualities.png|right|175px|caption]] | + | <p>[[File:Figure8.4_Qualities.png|right|175px|caption]]</p> |
| − | <p>There are a number of sources that define the properties of well-formed or | + | <p>There are a number of sources that define the properties of well-formed or "good" requirements. [[#Three|[3]]] [[#Four|[4]]] These beneficial characteristics help ensure that the requirements process is complete and that it results in a successful solution implementation. The more critical and more complex the project, the more important these qualities are.</p> |
<ul> | <ul> | ||
| − | <li>'''Clear and unambiguous''' | + | <li>'''Clear and unambiguous'''—Can all stakeholders and solution implementers understand the requirement? Is there any disagreement about what the requirement means? Each requirement needs to be specified (or modeled) in a way that is clear and unambiguous. </li> |
| − | <li>'''Usable''' | + | <li>'''Usable'''—Is the requirement useful in creating or defining the solution? Requirements that are not useful or usable confuse the situation and the solution definition process. </li> |
| − | <li>'''Current''' | + | <li>'''Current'''—Does the requirement reflect the current situation or where the solution must head? Requirements should not conduct history lessons and should not tell stories about the past. They need to reflect the current situation or where the organization needs to head.</li> |
| − | <li>'''Traceable''' | + | <li>'''Traceable'''—Do you know where the requirement came from? It is critical to know the source of each piece of information. Did it come from an interview with an SME? Is it from a particular manager or executive? If another requirement appears to be in conflict with it, do you know who to discuss the issue with?</li> |
| − | <li>'''Granular''' | + | <li>'''Granular'''—Is there only one criterion/data item in the requirement? It is critical to be able to distinguish between the pieces of information. This isn't as easy as it seems. It is hard to get individuals to disambiguate issues, so they often develop requirements/goals that address both issues, when they should split the issues and then develop new business rules.</li> |
| − | <li>'''Measurable success criteria''' | + | <li>'''Measurable success criteria'''—Is the requirement written in a way in which you can measure whether it has been satisfied? Can these measurements be incorporated in tests and in release criteria?</li> |
</ul> | </ul> | ||
<h3>Requirements Verification and Validation</h3> | <h3>Requirements Verification and Validation</h3> | ||
<p>Validation and verification happen frequently during the requirements, design, and construction processes. They ensure that the implemented solution truly fills the gap identified by the enterprise. Validation and verification during the requirements analysis phase has a particular slant:</p> | <p>Validation and verification happen frequently during the requirements, design, and construction processes. They ensure that the implemented solution truly fills the gap identified by the enterprise. Validation and verification during the requirements analysis phase has a particular slant:</p> | ||
<ul> | <ul> | ||
| − | <li>Requirements validation ensures that all requirements reflect the | + | <li>Requirements validation ensures that all requirements reflect the customer's real needs. Because there is no prototype available at this point, this means asking the stakeholders to validate that the requirements and resulting analysis support their needs. </li> |
<li>Requirements verification ensures that the results of the analysis process are consistent with previously collected requirements. This process verifies robustness, correctness, and consistency among all requirements and analysis results.</li> | <li>Requirements verification ensures that the results of the analysis process are consistent with previously collected requirements. This process verifies robustness, correctness, and consistency among all requirements and analysis results.</li> | ||
</ul> | </ul> | ||
| Line 162: | Line 169: | ||
<h3>Text-based Documentation</h3> | <h3>Text-based Documentation</h3> | ||
<ul> | <ul> | ||
| − | <li>'''Interview transcripts''' | + | <li>'''Interview transcripts''' can be relatively unstructured documents that follow the flow of the interview. There are a few characteristics that help them be effective documents. They should be dated and all participants should be listed. The purpose of the interview should be stated up front. The person making each statement should be clearly indicated. More advanced analysts also color code statements that indicate different kinds of information, or they add comments after the fact to shed light on the importance of a statement or action that needs to be performed because of the statement. It is also helpful to make notes about topics that should be covered in future sections.</li> |
| − | <li>'''Scenarios and use cases''' | + | <li>'''Scenarios and use cases''' are predominantly a list of steps that someone takes to perform a task. The steps often document an interaction with a system, such as a computer application, but they could be steps that a repairman takes to identify and fix a problem. Why use one versus the other?<br />As mentioned earlier, scenarios go through a single path of the process. They don't cover multiple possible outcomes or alternative flows. Scenarios are great elicitation tools and are often used by the [http://eitbokwiki.org/Glossary#qa QA] team to create tests for a single logical path through the domain. The QA team can use the scenario as a gold standard of the interaction between the solution and the user.<br />Use cases, however, cover multiple outcomes and alternate flows. Use cases are better at guiding the developer in building the solution. They describe all the options available for the user at a given point. They build a more complete picture of the current state and all the options that the user has. There are lots of templates available for use cases and they are often considered a critical tool in the solution-definition process. For a good how-to reference, refer to ''Writing Effective Use Cases''. [[#Five|[5]]] </li> |
| − | <li>'''Data dictionary''' | + | <li>'''Data dictionary''' is a dictionary of data items. This repository of information describes each item including its meaning, origin, use, data type, possible values, and relationship to other data. A data dictionary is a critical repository for any application that contains a significant number of data items.</li> |
| − | <li>'''Security, privacy, and data classification''' | + | <li>'''Security, privacy, and data classification'''—Enterprise solutions require a security plan. These plans are usually separate documents that cover all the security risks and the means for addressing them. The plan should list all the assets that need to be protected, the associated risks with each asset, the way to protect the assets, and the cost of protection. Basic questions include: How are users going to be authenticated? How is personal data going to be protected? What data needs to be protected? [[#Six|[6]]] </li> |
| − | <li>'''Business rules''' | + | <li>'''Business rules''' define how the enterprise operates. They are statements or conditions that indicate what actions individuals can perform or what decisions they can make. A business rule might be something like: ''An online store customer must have a valid email address.'' Business rules must be stated precisely. Slight changes in wording can make a huge difference in how the requirements are developed. Rules need to have owners and they need to be easily found and tracked.</li> |
| − | <li>'''Metrics for testing and release criteria''' | + | <li>'''Metrics for testing and release criteria'''—A key aspect of specifying requirements is identifying the criteria that are used to determine whether the requirement has been satisfied (the definition of ''Done''). When requirements are well formed, they contain the measures of success for the intended application or solution. These measures need to be captured as the evaluation and [http://eitbokwiki.org/Glossary#acceptance_criteria acceptance criteria] for the solution. In other words, how do you know when the solution is good enough? What conditions must the solution satisfy to be accepted by the stakeholders?<br />Typically there is a document that collects these necessary conditions and labels them as ''release criteria''. These criteria specify how the solution performs, as well as expectations of how the organization performs with the solution. These criteria are sometimes called the solution's ''[http://eitbokwiki.org/Glossary#kpi key performance indicators (KPIs)]''. They should be included in tests and can be things such as the response time during a session, accuracy/relevance of a recommendation to a user, uptime of the solution, or mean time between failure. The KPIs for the organization can be metrics such as the level of customer satisfaction, the number of defects per 1000 units, labor spent per month, burn-down rates, or the [http://eitbokwiki.org/Glossary#roi return on investment (ROI)]. </li> |
</ul> | </ul> | ||
<h3>Graphic-based Documentation </h3> | <h3>Graphic-based Documentation </h3> | ||
| − | <p>Diagrams are useful for illustrating what would take many paragraphs to explain. Diagrams do not stand alone as | + | <p>Diagrams are useful for illustrating what would take many paragraphs to explain. Diagrams do not stand alone as documentation—descriptions of the diagrams are also important. </p> |
<ul> | <ul> | ||
| − | <li>'''Sequence diagrams''' | + | <li>'''Sequence diagrams''' describe a process. They show how processes operate or interact with one another. They are often referred to as ''event diagrams'' or ''event scenarios''. There is a specific visual language used with these diagrams.</li> |
| − | <li>'''State diagrams''' | + | <li>'''State diagrams''' are used to model behavior. There are several different kinds of state diagrams, but most represent states of a system (e.g., on and off) using objects (such as circles) with lines from one circle to another that represent an event or action taken to get from one state to another. State diagrams are not flowcharts, which describe process flows. See example below.<br />[[File:Figure8.5_StateDiagram.png|650px]]</li> |
| − | <li>'''Data flow diagrams''' | + | <li>'''Data flow diagrams''' are graphic representations of the flow of data through an information system. They show the flow of inputs and outputs through the system and its components, and where the data is stored. These diagrams can be used at a number of levels to describe the system. See example below.<br />[[File:Figure8.6_DataFlow.png|750px]]</li> |
| − | <li>'''Decision tables, trees, and rules''' | + | <li>'''Decision tables, trees, and rules''' are tools used to model decisions and their consequences. They model algorithms. They often lead from observations to conclusions. There are several different ways to use these representations and they are closely related to influence diagrams. See example below.<br />[[File:Figure8.7_DecisionTable.png|650px]]</li> |
</ul> | </ul> | ||
| − | <h3>Image Creation | + | <h3>Image Creation Accepted Practices</h3> |
<p>When creating diagrams for requirements documentation, there are some guidelines that can help make your images more readable and understandable.</p> | <p>When creating diagrams for requirements documentation, there are some guidelines that can help make your images more readable and understandable.</p> | ||
<ol> | <ol> | ||
| Line 183: | Line 190: | ||
<li>'''Use a legend, and keep the legend in the same area of all images.''' Pick a corner or a side for the legend location. All legend elements should be in the same place on the diagram so the reader does not have to screen out multiple areas when reading the diagram.</li> | <li>'''Use a legend, and keep the legend in the same area of all images.''' Pick a corner or a side for the legend location. All legend elements should be in the same place on the diagram so the reader does not have to screen out multiple areas when reading the diagram.</li> | ||
<li>'''Use the same size icons for the same things.''' Different sizes of icons for similar objects makes it appear that the items are different somehow, and is distracting if there is no reason for dissimilar sizes.</li> | <li>'''Use the same size icons for the same things.''' Different sizes of icons for similar objects makes it appear that the items are different somehow, and is distracting if there is no reason for dissimilar sizes.</li> | ||
| − | <li> | + | <li>'''Create templates for common image types''' if possible, so that all diagrams use the same icons for the same thing, similar to the way flowchart elements have a standard icon list.</li> |
</ol> | </ol> | ||
<h3>Important Characteristics of the Documents</h3> | <h3>Important Characteristics of the Documents</h3> | ||
| − | <p>The documents themselves need to have many of the same characteristics | + | <p>The documents themselves need to have many of the same characteristics as the requirements:</p> |
<ul> | <ul> | ||
| − | <li>'''Understandable and usable''' | + | <li>'''Understandable and usable'''—The documents need to be understandable and usable, and not just by the person who wrote them. These documents are likely to be read and reviewed by many stakeholders including SMEs, users, management, and solution implementers. Each reader should find them usable and useful. For example, a tester should find information critical to designing tests; a writer composing a user manual needs to understand how the user's actions are responded to; customer support needs to know how the solution works, such as if there are known problems and known workarounds; and so on.</li> |
| − | <li>'''Consistent''' | + | <li>'''Consistent'''—The requirements documents cover the description of many requirements and it is critical that there is consistency of terminology, structure, and tone between the documents. For example, a characteristic of a situation that is used to make a logical conclusion in a case study should be included in the data dictionary. In addition, the name and the qualities of that item should be the same in both documents. Keeping the documents consistent takes considerable effort, but it is absolutely necessary to ensure a robust solution design.</li> |
| − | <li>'''Current''' | + | <li>'''Current'''—These documents need to be kept current. These documents are not useful if they are behind the elicitation and analysis activities by weeks or months. They should be updated within days of collecting new information.</li> |
| − | <li>'''Traceable''' | + | <li>'''Traceable'''—The information in each of the documents as well as the documents themselves need to be traceable. The owners of the documents should be clear. There should be a change-tracking system associated with these documents so that all stakeholders know when particular information was added or changed, and by whom.</li> |
| − | <li>'''Organized and modifiable''' | + | <li>'''Organized and modifiable'''—It is inevitable that some requirement previously gathered will change when analyzed. Organize and label the requirements to enable searching.</li> |
</ul> | </ul> | ||
<h2>Conceptual and Logical Design Development</h2> | <h2>Conceptual and Logical Design Development</h2> | ||
| − | <p>The requirements elicitation and analysis process is inextricably intertwined with the development of the | + | <p>The requirements elicitation and analysis process is inextricably intertwined with the development of the solution's conceptual and logical design. You can't have one team collect the requirements and data, and then have another team do the design, because having intimate knowledge of the requirements analysis results is critical. On the other hand, the solution design process requires skills beyond those needed for requirements gathering. Therefore, team members who are solution design experts, such as UI designers, system architects, and data engineers, need to become involved as the requirements evolve in specificity.</p> |
<p>At this point, it is important to make some distinctions about the design process. Most sources divide the design process into three phases:</p> | <p>At this point, it is important to make some distinctions about the design process. Most sources divide the design process into three phases:</p> | ||
<ol> | <ol> | ||
<li>The ''[http://eitbokwiki.org/Glossary#conceptual_design conceptual design]'' describes the proposed solution in a functional manner that could be easily understood by a future user. It describes how the solution looks and behaves.</li> | <li>The ''[http://eitbokwiki.org/Glossary#conceptual_design conceptual design]'' describes the proposed solution in a functional manner that could be easily understood by a future user. It describes how the solution looks and behaves.</li> | ||
<li>The ''[http://eitbokwiki.org/Glossary#logical_design logical design]'' defines objects, entities, their attributes, and their relationships. It also describes the business rules associated with these entities.</li> | <li>The ''[http://eitbokwiki.org/Glossary#logical_design logical design]'' defines objects, entities, their attributes, and their relationships. It also describes the business rules associated with these entities.</li> | ||
| − | <li>The ''[http://eitbokwiki.org/Glossary#physical_design physical design]'' is where the other two designs are converted to a definition of how the solution is implemented in hardware, software, and potentially other media. The physical (a.k.a. technical) design is developed by the construction team not by the requirements team (see the [http://eitbokwiki.org/Construction Construction chapter]).</li> | + | <li>The ''[http://eitbokwiki.org/Glossary#physical_design physical design]'' is where the other two designs are converted to a definition of how the solution is implemented in hardware, software, and potentially other media. The physical (a.k.a. technical) design is developed by the construction team, not by the requirements team (see the [http://eitbokwiki.org/Construction Construction chapter]).</li> |
</ol> | </ol> | ||
<h3>Solution Components</h3> | <h3>Solution Components</h3> | ||
| Line 216: | Line 223: | ||
<p>There are a number of techniques used during the design process that enable the team to develop an optimized solution for the set of requirements. A few of these are listed below.</p> | <p>There are a number of techniques used during the design process that enable the team to develop an optimized solution for the set of requirements. A few of these are listed below.</p> | ||
<ul> | <ul> | ||
| − | <li>'''Impact analysis''' | + | <li>'''Impact analysis'''—Understanding the impact of each component and function is critical to determine what functionality is implemented in the solution and when it is implemented. Impact analysis identifies the potential consequences of a change or estimates what needs to be modified to accomplish a change, as defined in ''A Guide to the Business Analysis Body of Knowledge''. [[#Eight|[8]]]<br />A good impact analysis report includes a detailed cost/benefit analysis. It outlines the risks, costs, and business requirements that are being met. It shows the links between requirements both in respect to dependency and traceability. The design team uses the impact analysis report to determine the scope and prioritization of the solution implementation. They may also find a need to refine the report as they work on the details of the scoping and prioritization.</li> |
| − | <li>'''Prioritization of development''' | + | <li>'''Prioritization of development'''—The design team works with stakeholders, the impact analysis, and the enterprise requirements to develop a priority order for the development of the requirements and components. Prioritization might also drive changes in project scope.</li> |
| − | <li>'''Scoping''' | + | <li>'''Scoping'''—This process determines what is and is not included in the solution. This might include functionality, requirements, cost, timing, and personnel. Scoping is often an effective technique for staging the development of a solution. For example, an organization can implement low-cost and easy-to-implement solutions first, and then add the more expensive and harder components later. <br />Iterative and incremental development approaches (such as scrum, agile, lean manufacturing, DSDM, and spiral) split the total scope of the project into smaller chunks. This allows stakeholders to adjust a project's requirements or goals after they see prototypes or demonstrations that have partial functionality. The stakeholders along with the development team determine the features to include at each iteration cycle. After each cycle, the next cycle's features are selected and the requirements analysis, design, and construction phases occur for the new cycle. At times, the results of a cycle provide information that prompts an adjustment to the full scope of the project.</li> |
| − | <li>'''Prototyping or proof of concept (POC)''' | + | <li>'''Prototyping or proof of concept (POC)'''—This technique creates a preliminary version or model of the final solution. We often think of creating a prototype for computer programs or machines; however, the technique is equally valid for job aids, job descriptions, training programs, and so on. The job of the prototype is to illustrate the qualities and functionality of the component. Prototypes are especially effective, because users can experience them and give detailed feedback on how well they meet their needs. Prototypes are also effective vehicles for identifying faulty assumptions and missing functionality.</li> |
| − | <li>'''Security design''' | + | <li>'''Security design'''—Security design has become increasing important over the last 30 years. The team must understand the security requirements and design the features necessary to meet them. The design needs to take into account authorization and authentication, data encryption, user and data privacy, data auditing, non-repudiation, and conformance to standards. See the [http://eitbokwiki.org/Security Security chapter] for more information.</li> |
</ul> | </ul> | ||
<h4>Alternatives Analysis: Functionality Reallocation</h4> | <h4>Alternatives Analysis: Functionality Reallocation</h4> | ||
<p>During solution design, it is often necessary to reallocate functionality between the different solution components. The reason for this is often the cost required to develop or maintain the solution. For example, it might cost too much to implement a computer application to provide some functionality, so simpler job aids are created instead. Or perhaps a desired new business rule requires too much manpower to implement to make it worth the benefit received. In general, when the design process is well underway and the cost to implement each component becomes evident, the team can determine which functionality allocations have the best cost/benefit ratio for the enterprise.</p> | <p>During solution design, it is often necessary to reallocate functionality between the different solution components. The reason for this is often the cost required to develop or maintain the solution. For example, it might cost too much to implement a computer application to provide some functionality, so simpler job aids are created instead. Or perhaps a desired new business rule requires too much manpower to implement to make it worth the benefit received. In general, when the design process is well underway and the cost to implement each component becomes evident, the team can determine which functionality allocations have the best cost/benefit ratio for the enterprise.</p> | ||
<h2>Solution Review, Verification, and Validation</h2> | <h2>Solution Review, Verification, and Validation</h2> | ||
| − | <p> | + | <p>Verification is one of the most important things to do after creating a conceptual and logical solution design. Stakeholders must assess proposed solutions to see if they meet all stakeholder and solution requirements. This verification process ensures that requirement specifications, models, and prototypes meet the necessary standard of quality for the solution to be correct and of acceptable quality. The process determines whether a solution design component is ready for formal review and signoff.</p> |
| − | <p>One of the activities during this process is to validate that requirements are met. This means that the requirements, ''as they are manifested in the solution design'', support the delivery of value to the business, fulfill the | + | <p>One of the activities during this process is to validate that requirements are met. This means that the requirements, ''as they are manifested in the solution design'', support the delivery of value to the business, fulfill the enterprise's goals and objectives, and meet the stakeholders' needs. To ensure that this is the case, it is often valuable to define detailed acceptance and evaluation criteria. Key metrics and key performance indicators for the solution are also often developed.</p> |
| − | <p>Sometimes a design appears to meet all the criteria, but when the stakeholders (especially future users) see the design through structured walkthroughs or interaction with a prototype, they point out issues with the design. Often these issues are associated with requirements that were never collected or ones that were not well understood. But often, the solution just | + | <p>Sometimes a design appears to meet all the criteria, but when the stakeholders (especially future users) see the design through structured walkthroughs or interaction with a prototype, they point out issues with the design. Often these issues are associated with requirements that were never collected or ones that were not well understood. But often, the solution just isn't mature enough. It is common for a design to be refined three or more times during the review and validation process.</p> |
| − | <p>A solution needs to be complete, correct, consistent, unambiguous, cohesive, testable, robust and feasible; if not, the solution should not be approved. Most of these qualities were covered with respect to requirements qualities (see [[#WellFormedReq|Qualities of Well-Formed Requirements]]). There are | + | <p>A solution needs to be complete, correct, consistent, unambiguous, cohesive, testable, robust, and feasible; if not, the solution should not be approved. Most of these qualities were covered with respect to requirements qualities (see [[#WellFormedReq|Qualities of Well-Formed Requirements]]). There are four qualities that are specific to the conceptual and logical solution design:</p> |
<ul> | <ul> | ||
| − | <li>'''Feasible''' | + | <li>'''Feasible'''—The design can be successfully implemented.</li> |
| − | <li>'''Cohesive''' | + | <li>'''Cohesive'''—All components of the solution are well integrated and unified. In addition, the components of the solution are created so that their role is clear, complete, and easily distinguished from the other components.</li> |
| − | <li>'''Testable''' | + | <li>'''Testable'''—A solution is testable when its functionality and its ability to address the goals of the project can be tested and measured.</li> |
| − | <li>'''Robust''' | + | <li>'''Robust'''—A solution design is robust when it covers not only the base-level functionality, but also the ability to cope with errors during use. That is, the solution can continue to operate in a reasonable way even if it receives abnormal inputs or encounters unforeseen situations.</li> |
</ul> | </ul> | ||
<p>The review with the stakeholders can take several forms. It can be a walkthrough of a paper solution component with the relevant stakeholders, users working with a prototype, or stakeholders determining which one of several competing solutions is the best. Each solution component has an associated method for review and validation. Each component should also have its own acceptance and performance criteria.</p> | <p>The review with the stakeholders can take several forms. It can be a walkthrough of a paper solution component with the relevant stakeholders, users working with a prototype, or stakeholders determining which one of several competing solutions is the best. Each solution component has an associated method for review and validation. Each component should also have its own acceptance and performance criteria.</p> | ||
| Line 243: | Line 250: | ||
<h2>Summary</h2> | <h2>Summary</h2> | ||
<p>The requirements analysis or requirements specification process is often the most complex stage of defining and building an EIT solution. It takes a number of skills and knowledge of many techniques to create a complete and verifiable set of requirements. Expertise in requirements analysis takes years of work; it is best to learn as an apprentice, where one can watch an expert analyst work through the process.</p> | <p>The requirements analysis or requirements specification process is often the most complex stage of defining and building an EIT solution. It takes a number of skills and knowledge of many techniques to create a complete and verifiable set of requirements. Expertise in requirements analysis takes years of work; it is best to learn as an apprentice, where one can watch an expert analyst work through the process.</p> | ||
| − | <p>The activities in this phase are not typically sequential. Many activities overlap and requirements analysis for one part of the domain may overlap with construction of another part of the solution. It is even necessary to | + | <p>The activities in this phase are not typically sequential. Many activities overlap and requirements analysis for one part of the domain may overlap with construction of another part of the solution. It is even necessary to take knowledge acquired during implementation and feed it back into the requirements process. </p> |
<p>This stage is a key to having a successful solution that meets the business criteria, stays within budget, and is easily maintained. For general books on the topics of software requirements and specifications, refer to [[#Eight|[8]]], [[#Nine|[9]]], [[#Ten|[10]]], [[#Eleven|[11]]], and [[#Twelve|[12]]]. </p> | <p>This stage is a key to having a successful solution that meets the business criteria, stays within budget, and is easily maintained. For general books on the topics of software requirements and specifications, refer to [[#Eight|[8]]], [[#Nine|[9]]], [[#Ten|[10]]], [[#Eleven|[11]]], and [[#Twelve|[12]]]. </p> | ||
| − | + | <h2>Key Maturity Frameworks</h2> | |
| + | <p>Capability maturity for EIT refers to its ability to reliably perform. Maturity is measured by an organization's readiness and capability expressed through its people, processes, data, technologies, and the consistent measurement practices that are in place. See [http://eitbokwiki.org/Enterprise_IT_Maturity_Assessments Appendix F] for additional information about maturity frameworks.</p> | ||
| + | <p>Many specialized frameworks have been developed since the original Capability Maturity Model (CMM) that was developed by the Software Engineering Institute in the late 1980s. This section describes how some of those apply to the activities described in this chapter. </p> | ||
| + | <h3>IT-Capability Maturity Framework (IT-CMF) </h3> | ||
| + | <p>The IT-CMF was developed by the Innovation Value Institute in Ireland. This framework helps organizations to measure, develop, and monitor their EIT capability maturity progression. It consists of 35 EIT management capabilities that are organized into four macro capabilities: </p> | ||
| + | <ul> | ||
| + | <li>Managing EIT like a business</li> | ||
| + | <li>Managing the EIT budget</li> | ||
| + | <li>Managing the EIT capability</li> | ||
| + | <li>Managing EIT for business value</li> | ||
| + | </ul> | ||
| + | <p>The three most relevant critical capabilities are user experience design (UED), solutions delivery (SD), and service provisioning (SRP). </p> | ||
| + | <h4>User Experience Design Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the user experience design (UED) capability at successive levels of maturity.</p> | ||
| + | <table> | ||
| + | <tr valign="top"><td width="10%">Level 1</td><td>There is no official recognition of user experience as a discipline within the organization. EIT services and solutions are not typically considered user-friendly. </td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>Defined user experience approaches are emerging in the design and development of a limited number of EIT services and solutions. The user experience of most EIT services and solutions is improving </td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>Standardized user experience approaches guide the design and development of most EIT services and solutions, which increasingly enable users to accomplish their tasks and goals easily, efficiently, and accurately. </td></tr> | ||
| + | <tr valign="top"><td>Level 4</td><td>Comprehensive user experience approaches are used during the design and development of all EIT services and solutions, so that they are generally suitable for their audiences, purposes, and contexts of use. </td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>User experience approaches are adopted, and are continually reviewed for improvement opportunities. EIT services and solutions offered/brokered by the EIT function consistently provide richer user experiences when compared to market alternatives. </td></tr> | ||
| + | </table> | ||
| + | <h4>Solutions Delivery Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the solutions delivery (SD) capability at successive levels of maturity.</p> | ||
| + | <table> | ||
| + | <tr valign="top"><td width="10%">Level 1</td><td>There is ad hoc use of solutions delivery methodologies. EIT solutions are typically delivered with wide variations in quality, schedule, and cost expectations.</td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>Basic solutions delivery methodologies are defined and applied to a limited number of EIT solution projects, which are beginning to meet expectations, but variations in quality, schedule, and cost still occur. </td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>Standardized solutions delivery methodologies are applied to most EIT solution projects, enabling many of them to regularly meet expectations for quality, schedule, and cost. </td></tr> | ||
| + | <tr valign="top"><td>Level 4</td> | ||
| + | <td>Comprehensive and flexible project delivery methodologies are applied to all projects, enabling most projects to meet expectations for quality, schedule, and cost.</td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>Solutions delivery methodologies are continually analyzed and refreshed. Solutions delivery expectations for quality, schedule, and cost are nearly always met. </td></tr> | ||
| + | </table> | ||
| + | <h4>Service Provisioning Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the service provisioning (SRP) capability at successive levels of maturity.</p> | ||
| + | <table> | ||
| + | <tr valign="top"><td width="10%">Level 1</td><td>The service provisioning processes are ad hoc, resulting in unpredictable EIT service quality. </td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>Service provisioning processes are increasingly defined and documented, but execution is dependent on individual interpretation of the documentation. Service level agreements (SLAs) are typically defined at the technical operational level only. </td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>Service provisioning is supported by standardized tools for most EIT services, but may not yet be adequately integrated. SLAs are typically defined at the business operational level. </td></tr> | ||
| + | <tr valign="top"><td>Level 4</td><td>Customers have access to services on demand. Management and troubleshooting of services are highly automated.</td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>Customers experience zero downtime or delays, and service provisioning is fully automated. </td></tr> | ||
| + | </table> | ||
<h2> Key Competence Frameworks</h2> | <h2> Key Competence Frameworks</h2> | ||
| − | <p>While many large companies have defined their own sets of skills for purposes of talent management | + | <p>While many large companies have defined their own sets of skills for purposes of talent management (to recruit, retain, and further develop the highest quality staff members that they can find, afford and hire), the advancement of EIT professionalism will require common definitions of EIT skills that can be used not just across enterprises, but also across countries. We have selected three major sources of skill definitions. While none of them is used universally, they provide a good cross-section of options. </p> |
| − | + | <p>Creating mappings between these frameworks and our chapters is challenging, because they come from different perspectives and have different goals. There is rarely a 100 percent correspondence between the frameworks and our chapters, and, despite careful consideration some subjectivity was used to create the mappings. Please take that in consideration as you review them.</p> | |
| − | <p>Creating mappings between these frameworks and our chapters is challenging, because they come from different perspectives and have different goals. There is rarely a 100 | + | |
| − | + | ||
<h3>Skills Framework for the Information Age</h3> | <h3>Skills Framework for the Information Age</h3> | ||
| − | <p> The Skills Framework for the Information Age (SFIA) has defined nearly 100 skills. SFIA describes | + | <p>The Skills Framework for the Information Age (SFIA) has defined nearly 100 skills. SFIA describes seven levels of competency that can be applied to each skill. However, not all skills cover all seven levels. Some reach only partially up the seven-step ladder. Others are based on mastering foundational skills, and start at the fourth or fifth level of competency. SFIA is used in nearly 200 countries, from Britain to South Africa, South America, to the Pacific Rim, to the United States. (http://www.sfia-online.org)</p> |
| − | + | <table cellpadding="5" border="1"> | |
| − | <table cellpadding="5" | + | <tr><th style="background-color: #58ACFA;"><font color="white">Skill</font></th><th style="background-color: #58ACFA;"><font color="white">Skill Description</font></th><th width="10%" style="background-color: #58ACFA;"><font color="white">Competency Levels</font></th></tr> |
| − | <tr> | + | <tr valign="top"><td>Availability management</td><td>The definition, analysis, planning, measurement, maintenance, and improvement of all aspects of the availability of services, including the availability of power. The overall control and management of service availability to ensure that the level of service delivered in all services is matched to or exceeds the current and future agreed needs of the business, in a cost-effective manner.</td><td valign="top">4-6</td></tr> |
| − | <th | + | <tr valign="top"><td>Business analysis</td><td>The methodical investigation, analysis, review, and documentation of all or part of a business in terms of business functions and processes, the information used, and the data on which the information is based. The definition of requirements for improving processes and systems, reducing their costs, enhancing their sustainability, and the quantification of potential business benefits. The collaborative creation and iteration of viable specifications and acceptance criteria in preparation for the deployment of information and communication systems.</td><td valign="top">3-6</td></tr> |
| − | <th>Skill Description</th> | + | <tr valign="top"><td>Business modeling</td><td>The production of abstract or distilled representations of real world, business, or gaming situations in traditional or trans-media applications, to aid the communication and understanding of existing, conceptual, or proposed scenarios. Predominantly focused around the representation of processes, roles, data, organization, and time. Models may be used to represent a subject at varying levels of detail and decomposition.</td><td valign="top">2-6</td></tr> |
| − | <th width="10%">Competency Levels</ | + | <tr valign="top"><td>Business process improvement</td><td>The identification of new and alternative approaches to performing business activities. The analysis of business processes, including recognition of the potential for automation of the processes, assessment of the costs and potential benefits of the new approaches considered, and, where appropriate, management of change, and assistance with implementation. May include the implementation of a process management capability/discipline at the enterprise level.</td><td valign="top">5-7</td></tr> |
| − | </ | + | <tr valign="top"><td>Continuity management</td><td>The provision of service continuity planning and support. This includes the identification of information systems that support critical business processes; the assessment of risks to those systems' availability, integrity, and confidentiality; and the co-ordination of planning, designing, testing, maintenance procedures, and contingency plans to address exposures and maintain agreed levels of continuity. This function should be performed as part of, or in close cooperation with, the function that plans business continuity for the whole organization.</td><td valign="top">4-5</td></tr> |
| − | + | <tr valign="top"><td>Data analysis</td><td>The investigation, evaluation, interpretation, and classification of data, in order to define and clarify information structures that describe the relationships between real world entities. Such structures facilitate the development of software systems, links between systems, or retrieval activities.</td><td valign="top">2-5</td></tr> | |
| − | <tr> | + | <tr valign="top"><td>Data management</td><td>The management of practices and processes to ensure the security, integrity, safety, and availability of all forms of data and data structures that make up the organization's information. The management of data and information in all its forms and the analysis of information structure (including logical analysis of taxonomies, data, and metadata). The development of innovative ways of managing the information assets of the organization.</td><td valign="top">2-6</td></tr> |
| − | < | + | <tr valign="top"><td>Emerging technology monitoring</td><td>The identification of new and emerging hardware, software and communication technologies and products, services, methods, and techniques and the assessment of their relevance and potential value as business enablers, improvements in cost/performance, or sustainability. The promotion of emerging technology awareness among staff and business management.</td><td valign="top">4-6</td></tr> |
| − | <td>The definition, analysis, planning, measurement, maintenance and improvement of all aspects of the availability of services, including the availability of power. The overall control and management of service availability to ensure that the level of service delivered in all services is matched to or exceeds the current and future agreed needs of the business, in a cost effective manner.</td> | + | <tr valign="top"><td>Enterprise and business architecture</td><td>The creation, iteration, and maintenance of structures such as enterprise and business architectures embodying the key principles, methods, and models that describe the organization's future state, and that enable its evolution. This typically involves the interpretation of business goals and drivers; the translation of business strategy and objectives into an "operating model"; the strategic assessment of current capabilities; the identification of required changes in capabilities; and the description of inter-relationships between people, organization, service, process, data, information, technology, and the external environment. |
| − | <td valign="top" >4 - 6</td> | + | <p>The architecture development process supports the formation of the constraints, standards, and guiding principles necessary to define, ensure, and govern the required evolution; this facilitates change in the organization's structure, business processes, systems, and infrastructure in order to achieve predictable transition to the intended state.</p></td><td valign="top">5-7</td></tr> |
| − | </tr> | + | <tr valign="top"><td>Information assurance</td><td>The protection of integrity, availability, authenticity, non-repudiation, and confidentiality of information and data in storage and in transit. The management of risk in a pragmatic and cost-effective manner to ensure stakeholder confidence.</td><td valign="top">5-7</td></tr> |
| − | <tr | + | <tr valign="top"><td>Information management</td><td>The overall governance of how all types of information, structured and unstructured, whether produced internally or externally, are used to support decision-making, business processes, and digital services. Encompasses development and promotion of the strategy and policies covering the design of information structures and taxonomies, the setting of policies for the sourcing and maintenance of the data content, and the development of policies, procedures, working practices, and training to promote compliance with legislation regulating all aspects of holding, use, and disclosure of data.</td><td valign="top">4-7</td></tr> |
| − | + | <tr valign="top"><td>Information security</td><td>The selection, design, justification, implementation, and operation of controls and management strategies to maintain the security, confidentiality, integrity, availability, accountability, and relevant compliance of information systems with legislation, regulation, and relevant standards.</td><td valign="top">3-7</td></tr> | |
| − | <td>The methodical investigation, analysis, review and documentation of all or part of a business in terms of business functions and processes, the information used and the data on which the information is based. The definition of requirements for improving processes and systems, reducing their costs, enhancing their sustainability, and the quantification of potential business benefits. The collaborative creation and iteration of viable specifications and acceptance criteria in preparation for the deployment of information and communication systems.</td> | + | <tr valign="top"><td>Information systems coordination</td><td>Typically within a large organization in which the information strategy function is devolved to autonomous units, or within a collaborative enterprise of otherwise independent organizations, the coordination of information strategy matters where the adoption of a common approach (such as shared services) would benefit the organization.</td><td valign="top">6-7</td></tr> |
| − | <td valign="top" >3 - 6</td> | + | <tr valign="top"><td>Innovation</td><td>The capability to recognize and exploit business opportunities provided by information and communication technology, accepted practices, methods, and standards, to ensure more efficient and effective performance of organizations, to explore possibilities for new ways of conducting business and organizational processes, and to establish new services or businesses.</td><td valign="top">5-6</td></tr> |
| − | </tr> | + | <tr valign="top"><td>EIT strategy and planning</td><td>The creation, iteration, and maintenance of a strategy to align EIT plans with business objectives and the development of plans to drive forward and execute that strategy. Working with stakeholders to communicate and embed strategic management via objectives, accountabilities, and monitoring of progress.</td><td valign="top">5-7</td></tr> |
| − | <tr | + | <tr valign="top"><td>Network planning</td><td>The creation and maintenance of overall network plans, encompassing the communication of data, voice, text, and image, in the support of an organization's business strategy. This includes participation in the creation of service level agreements and the planning of all aspects of infrastructure necessary to ensure provision of network services to meet such agreements. Physical implementation may include copper wire, fiber optic, wireless, or any other technology.</td><td valign="top">5-6</td></tr> |
| − | + | <tr valign="top"><td>Portfolio, program, and project support</td><td>The provision of support and guidance on portfolio, program, and project management processes, procedures, tools, and techniques. Support includes definition of portfolios, programs, and projects; advice on the development, production, and maintenance of business cases; time, resource, cost, and exception plans; and the use of related software tools. Tracking and reporting of program/project progress and performance are also covered, as is the capability to facilitate all aspects of portfolio/program/project meetings, workshops, and documentation.</td><td valign="top">2-6</td></tr> | |
| − | <td>The production of abstract or distilled representations of real world, business or gaming situations in traditional or trans-media applications, to aid the communication and understanding of existing, conceptual or proposed scenarios. Predominantly focused around the representation of processes, roles, data, | + | <tr valign="top"><td>Project management</td><td>The management of projects, typically (but not exclusively) involving the development and implementation of business processes to meet identified business needs, acquiring and utilizing the necessary resources and skills, within agreed parameters of cost, timescales, and quality.</td><td valign="top">4-7</td></tr> |
| − | <td valign="top" >2 - 6</td> | + | <tr valign="top"><td>Requirements definition and management</td><td>The definition and management of the business goals and scope of change initiatives. The specification of business requirements to a level that enables effective delivery of agreed changes.</td><td valign="top">2-6</td></tr> |
| − | </tr> | + | <tr valign="top"><td>Service level management</td><td>The planning, implementation, control, review, and audit of service provision, to meet customer business requirements. This includes negotiation, implementation, and monitoring of service level agreements (SLAs), and the ongoing management of operational facilities to provide the agreed levels of service, seeking continually and proactively to improve service delivery and sustainability targets.</td><td valign="top">2-7</td></tr> |
| − | <tr | + | <tr valign="top"><td>Solution architecture</td><td>The design and communication of high-level structures to enable and guide the design and development of integrated solutions that meet current and future business needs. In addition to technology components, solution architecture encompasses changes to service, process, organization, and operating models. Architecture definition must demonstrate how requirements (such as automation of business processes) are met, any requirements that are not fully met, and any options or considerations that require a business decision. The provision of comprehensive guidance on the development of, and modifications to, solution components to ensure that they take account of relevant architectures, strategies, policies, standards, and practices (including security) and that existing and planned solution components remain compatible.</td><td valign="top">5-6</td></tr> |
| − | + | <tr valign="top"><td>User experience analysis</td><td>The identification, analysis, clarification, and communication of the context of use in which applications will operate, and of the goals of products, systems, or services. Analysis and prioritization of stakeholders' "user experience" needs and definition of required system behavior and performance. Resolution of potential conflicts between user requirements and determination of usability objectives.</td><td valign="top">3-5</td></tr> | |
| − | <td>The identification of new and alternative approaches to performing business activities. The analysis of business processes, including recognition of the potential for automation of the processes, assessment of the costs and potential benefits of the new approaches considered and, where appropriate, management of change, and assistance with implementation. May include the implementation of a process management capability/discipline at the enterprise level.</td> | + | |
| − | <td valign="top" >5 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The provision of service continuity planning and support. This includes the identification of information systems | + | |
| − | <td valign="top" >4 - 5</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The investigation, evaluation, interpretation and classification of data, in order to define and clarify information structures | + | |
| − | <td valign="top" >2 - 5</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The management of practices and processes to ensure the security, integrity, safety and availability of all forms of data and data structures that make up the | + | |
| − | <td valign="top" >2 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The identification of new and emerging hardware, software and communication technologies and products, services, methods and techniques and the assessment of their relevance and potential value as business enablers, improvements in cost/performance or sustainability. The promotion of emerging technology awareness among staff and business management.</td> | + | |
| − | <td valign="top" >4 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The creation, iteration, and maintenance of structures such as enterprise and business architectures embodying the key principles, methods and models that describe the | + | |
| − | + | ||
| − | The architecture development process supports the formation of the constraints, standards and guiding principles necessary to define, | + | |
| − | <td valign="top" >5 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The protection of integrity, availability, authenticity, non-repudiation and confidentiality of information and data in storage and in transit. The management of risk in a pragmatic and cost effective manner to ensure stakeholder confidence.</td> | + | |
| − | <td valign="top" >5 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The overall governance of how all types of information, structured and unstructured, whether produced internally or externally, are used to support decision-making, business processes and digital services. Encompasses development and promotion of the strategy and policies covering the design of information structures and taxonomies, the setting of policies for the sourcing and maintenance of the data content, and the development of policies, procedures, working practices and training to promote compliance with legislation regulating all aspects of holding, use and disclosure of data.</td> | + | |
| − | <td valign="top" >4 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The selection, design, justification, implementation and operation of controls and management strategies to maintain the security, confidentiality, integrity, availability, accountability and relevant compliance of information systems with legislation, regulation and relevant standards.</td> | + | |
| − | <td valign="top" >3 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>Typically within a large | + | |
| − | <td valign="top" >6 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The capability to | + | |
| − | <td valign="top" >5 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The creation, iteration and maintenance of a strategy | + | |
| − | <td valign="top" >5 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The creation and maintenance of overall network plans, encompassing the communication of data, voice, text and image, in the support of an | + | |
| − | <td valign="top" >5 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The provision of support and guidance on portfolio, | + | |
| − | <td valign="top" >2 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The management of projects, typically (but not exclusively) involving the development and implementation of business processes to meet identified business needs, acquiring and | + | |
| − | <td valign="top" >4 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The definition and management of the business goals and scope of change initiatives. The specification of business requirements to a level that enables effective delivery of agreed changes.</td> | + | |
| − | <td valign="top" >2 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The planning, implementation, control, review and audit of service provision, to meet customer business requirements. This includes negotiation, implementation and monitoring of service level agreements, and the ongoing management of operational facilities to provide the agreed levels of service, seeking continually and proactively to improve service delivery and sustainability targets.</td> | + | |
| − | <td valign="top" >2 - 7</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The design and communication of high-level structures to enable and guide the design and development of integrated solutions that meet current and future business needs. In addition to technology components, solution architecture encompasses changes to service, process, | + | |
| − | <td valign="top" >5 - 6</td> | + | |
| − | </tr> | + | |
| − | <tr | + | |
| − | + | ||
| − | <td>The identification, analysis, clarification and communication of the context of use in which applications will operate, and of the goals of | + | |
| − | <td valign="top" >3 - 5</td> | + | |
| − | </tr> | + | |
| − | + | ||
</table> | </table> | ||
| − | |||
<h3>European Competency Framework</h3> | <h3>European Competency Framework</h3> | ||
| − | <p> The European | + | <p>The European Union's European e-Competence Framework (e-CF) has 40 competences and is used by a large number of companies, qualification providers, and others in public and private sectors across the EU. It uses five levels of competence proficiency (e-1 to e-5). No competence is subject to all five levels.</p> |
| − | <p>The e-CF is published and legally owned by CEN, the European Committee for Standardization, and its National Member Bodies (www.cen.eu). Its creation and maintenance has been co-financed and politically supported by the European Commission, in particular, DG (Directorate General) Enterprise and Industry, with contributions from the EU ICT multi-stakeholder community, to support competitiveness, innovation, and job creation in European industry. The Commission works on a number of initiatives to boost ICT skills in the workforce. | + | <p>The e-CF is published and legally owned by CEN, the European Committee for Standardization, and its National Member Bodies (www.cen.eu). Its creation and maintenance has been co-financed and politically supported by the European Commission, in particular, DG (Directorate General) Enterprise and Industry, with contributions from the EU ICT multi-stakeholder community, to support competitiveness, innovation, and job creation in European industry. The Commission works on a number of initiatives to boost ICT skills in the workforce. Version 1.0 to 3.0 were published as CEN Workshop Agreements (CWA). The e-CF 3.0 CWA 16234-1 was published as an official European Norm (EN), EN 16234-1. For complete information, see http://www.ecompetences.eu. </p> |
| − | + | <table cellpadding="5" border="1"> | |
| − | Version 1.0 to 3.0 were published as CEN Workshop Agreements (CWA). | + | <tr valign="top"><th width="85%" style="background-color: #58ACFA;"><font color="white">e-CF Dimension 2</font></th><th style="background-color: #58ACFA;"><font color="white">e-CF Dimension 3</font></th></tr> |
| − | The e-CF 3.0 CWA 16234-1 was published as an official European Norm (EN), EN 16234-1. | + | <tr><td valign="top"><strong>A.4. Product/Service Planning (PLAN)</strong><br />Analyzes and defines current and target status. Estimates cost effectiveness, points of risk, opportunities, strengths, and weaknesses, with a critical approach. Creates structured plans; establishes time scales and milestones, ensuring optimization of activities and resources. Manages change requests. Defines delivery quantity and provides an overview of additional documentation requirements. Specifies correct handling of products, including legal issues, in accordance with current regulations.</td><td valign="top">Level 2-4</td></tr> |
| − | For complete information, | + | <tr><td valign="top"><strong>A.5. Architectural Design (PLAN)</strong><br />Specifies, refines, updates, and makes available a formal approach to implement solutions necessary to develop and operate the IS architecture. Identifies change requirements and the components involved: hardware, software, applications, processes, information, and technology platform. Takes into account interoperability, scalability, usability, and security. Maintains alignment between business evolution and technology developments.</td><td valign="top">Level 3-5</td></tr> |
| − | + | <tr><td valign="top"><strong>A.6. Application Design (PLAN)</strong><br />Analyzes, specifies, updates, and makes available a model to implement applications in accordance with IS policy and user/customer needs. Selects appropriate technical options for application design, optimizing the balance between cost and quality. Designs data structures and builds system structure models according to analysis results through modeling languages. Ensures that all aspects take account of interoperability, usability and security. Identifies a common reference framework to validate the models with representative users, based upon development models (e.g., iterative approach).</td><td valign="top">Level 1-3</td></tr> | |
| − | <table cellpadding="5" | + | <tr><td valign="top"><strong>D.10. Information and Knowledge Management (ENABLE)</strong><br />Identifies and manages structured and unstructured information and considers information distribution policies. Creates information structure to enable exploitation and optimization of information. Understands appropriate tools to be deployed to create, extract, maintain, renew, and propagate business knowledge in order to capitalize from the information asset. </td><td valign="top">Level 3-5</td></tr> |
| − | <tr> | + | <tr><td valign="top"><strong>D.11. Needs Identification (ENABLE)</strong><br />Actively listens to internal/external customers, articulates and clarifies their needs. Manages the relationship with all stakeholders to ensure that the solution is in line with business requirements. Proposes different solutions (e.g., make-or-buy) by performing contextual analysis in support of user centered system design. Advises the customer on appropriate solution choices. Acts as an advocate engaging in the implementation or configuration process of the chosen solution. </td><td valign="top">Level 3-5</td></tr> |
| − | <th width="85%">e-CF Dimension 2</th><th | + | |
| − | </tr> | + | |
| − | + | ||
| − | <tr> | + | |
| − | <td valign="top"><strong>A.4. Product / Service Planning (PLAN)<br /> | + | |
| − | <td valign="top">Level 2-4</td> | + | |
| − | </tr> | + | |
| − | <tr> | + | |
| − | <td valign="top"><strong>A.5. | + | |
| − | <td valign="top">Level 3-5</td> | + | |
| − | </tr> | + | |
| − | <tr> | + | |
| − | <td valign="top"><strong>A.6. Application Design (PLAN)<br /> | + | |
| − | <td valign="top">Level 1-3</td> | + | |
| − | </tr> | + | |
| − | + | ||
| − | + | ||
| − | <tr> | + | |
| − | <td valign="top"><strong>D.10. Information and Knowledge Management (ENABLE)<br />Identifies and manages structured and unstructured information and considers information distribution policies. Creates information structure to enable exploitation and | + | |
| − | <td valign="top">Level 3-5</td> | + | |
| − | </tr> | + | |
| − | + | ||
| − | <tr> | + | |
| − | <td valign="top"><strong>D.11. Needs Identification (ENABLE)<br />Actively listens to internal / external customers, articulates and clarifies their needs. Manages the relationship with all stakeholders to ensure that the solution is in line with business requirements. Proposes different solutions (e.g. make-or-buy) | + | |
| − | <td valign="top">Level 3-5</td> | + | |
| − | </tr> | + | |
</table> | </table> | ||
| − | + | <h3>i Competency Dictionary </h3> | |
| − | <h3>i Competency Dictionary | + | <p>The Information Technology Promotion Agency (IPA) of Japan has developed the i Competency Dictionary (iCD) and translated it into English, and describes it at https://www.ipa.go.jp/english/humandev/icd.html. The iCD is an extensive skills and tasks database, used in Japan and southeast Asian countries. It establishes a taxonomy of tasks and the skills required to perform the tasks. The IPA is also responsible for the Information Technology Engineers Examination (ITEE), which has grown into one of the largest scale national examinations in Japan, with approximately 600,000 applicants each year.</p> |
| − | <p>The Information Technology Promotion Agency (IPA) of Japan has developed the i Competency Dictionary (iCD) | + | <p>The iCD consists of a Task Dictionary and a Skill Dictionary. Skills for a specific task are identified via a "Task x Skill" table. (See [http://eitbokwiki.org/Glossary Appendix A] for the task layer and skill layer structures.) EITBOK activities in each chapter require several tasks in the Task Dictionary. </p> |
| − | + | <p>The table below shows a sample task from iCD Task Dictionary Layer 2 (with Layer 1 in parentheses) that corresponds to activities in this chapter. It also shows the Layer 2 (Skill Classification), Layer 3 (Skill Item), and Layer 4 (knowledge item from the IPA Body of Knowledge) prerequisite skills associated with the sample task, as identified by the Task x Skill Table of the iCD Skill Dictionary. The complete iCD Task Dictionary (Layer 1-4) and Skill Dictionary (Layer 1-4) can be obtained by returning the request form provided at http://www.ipa.go.jp/english/humandev/icd.html. </p> | |
| − | <p>The iCD consists of a Task Dictionary and a Skill Dictionary. Skills for a specific task are identified via a | + | |
| − | + | ||
| − | <p>The table below shows a sample task from iCD Task Dictionary Layer 2 (with Layer 1 in parentheses) that | + | |
| − | + | ||
<table cellpadding="5" border="1"> | <table cellpadding="5" border="1"> | ||
<tr> | <tr> | ||
| − | <th font-size="14pt">Task Dictionary</th><th colspan="3">Skill Dictionary</th> | + | <th width="15%" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Task Dictionary</font></th><th colspan="3" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Skill Dictionary</font></th> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| − | <th width="30%" | + | <th width="30%" style="background-color: #58ACFA;"><font color="white">Task Layer 1 (Task Layer 2)</font></th><th width="15%" style="background-color: #58ACFA;"><font color="white">Skill Classification</font></th><th width="15%" style="background-color: #58ACFA;"><font color="white">Skill Item</font></th><th width="40%" style="background-color: #58ACFA;"><font color="white">Associated Knowledge Items</font></th> |
</tr> | </tr> | ||
| − | |||
<tr> | <tr> | ||
| − | <td valign="top"><em><strong>Computerization requirements definition <br />( | + | <td valign="top"><em><strong>Computerization requirements definition <br />(system requirements definition and architecture design)</strong></em></td> |
<td valign="top">Requirement analysis methods</td> | <td valign="top">Requirement analysis methods</td> | ||
<td valign="top">Requirement extraction methods</td> | <td valign="top">Requirement extraction methods</td> | ||
| − | |||
<td> <ul> | <td> <ul> | ||
<li>RACI matrix</li> | <li>RACI matrix</li> | ||
| Line 441: | Line 356: | ||
<li>Shadowing</li> | <li>Shadowing</li> | ||
<li>Scope modeling</li> | <li>Scope modeling</li> | ||
| − | <li>Stakeholder | + | <li>Stakeholder analysis</li> |
<li>Other techniques (questionnaires, special-purpose recording, activity sampling)</li> | <li>Other techniques (questionnaires, special-purpose recording, activity sampling)</li> | ||
<li>Checklist</li> | <li>Checklist</li> | ||
| Line 453: | Line 368: | ||
<li>Metrics and KPI</li> | <li>Metrics and KPI</li> | ||
<li>Modeling</li> | <li>Modeling</li> | ||
| − | <li>Gathering of users, tasks and technologies</li> | + | <li>Gathering of users, tasks, and technologies</li> |
<li>User stories</li> | <li>User stories</li> | ||
<li>Understanding of user needs</li> | <li>Understanding of user needs</li> | ||
| Line 464: | Line 379: | ||
<li>Decision analysis</li> | <li>Decision analysis</li> | ||
<li>Structured walk-through</li> | <li>Structured walk-through</li> | ||
| − | <li>Root | + | <li>Root cause analysis</li> |
<li>Gap analysis</li> | <li>Gap analysis</li> | ||
<li>Definition of acceptance criteria and evaluation criteria</li> | <li>Definition of acceptance criteria and evaluation criteria</li> | ||
| − | <li>Understanding of participant's requests, needs and wants</li> | + | <li>Understanding of participant's requests, needs, and wants</li> |
<li>Advanced requirement capturing techniques (ethnographical techniques, knowledge acquisition, etc.)</li> | <li>Advanced requirement capturing techniques (ethnographical techniques, knowledge acquisition, etc.)</li> | ||
<li>Meeting with facilitator</li> | <li>Meeting with facilitator</li> | ||
| Line 479: | Line 394: | ||
</tr> | </tr> | ||
</table> | </table> | ||
| − | |||
| − | |||
| − | |||
<h2>Key Roles</h2> | <h2>Key Roles</h2> | ||
<p>These roles are common to ITSM:</p> | <p>These roles are common to ITSM:</p> | ||
<ul> | <ul> | ||
| + | <li>Application Developer</li> | ||
| + | <li>Applications Analyst</li> | ||
| + | <li>Business Relationship Manager</li> | ||
| + | <li>Configuration Manager</li> | ||
| + | <li>Knowledge Manager</li> | ||
<li>Process Architect</li> | <li>Process Architect</li> | ||
<li>Process Owner</li> | <li>Process Owner</li> | ||
| − | |||
| − | |||
<li>Project Manager</li> | <li>Project Manager</li> | ||
<li>Release Manager </li> | <li>Release Manager </li> | ||
| − | <li> | + | <li>Service Design Manager</li> |
<li>Supplier Manager</li> | <li>Supplier Manager</li> | ||
<li>Technical Analyst</li> | <li>Technical Analyst</li> | ||
| − | <li> | + | <li>Test Manager</li> |
| − | <li>Business | + | </ul> |
| − | <li> | + | <p>Other key roles are:</p> |
| − | <li> | + | <ul> |
| + | <li>Business Architect</li> | ||
| + | <li>Compliance Manager</li> | ||
| + | <li>Data Architect</li> | ||
| + | <li>Executive Sponsor</li> | ||
| + | <li>Governance Body</li> | ||
| + | <li>Operations Manager </li> | ||
| + | <li>Security Manager</li> | ||
| + | <li>User Experience Sponsor</li> | ||
</ul> | </ul> | ||
| − | |||
<h2>Standards</h2> | <h2>Standards</h2> | ||
| − | <p>ISO/IEC/IEEE 15288:2015, Systems and software engineering—Systems | + | <p>ISO/IEC/IEEE 15288:2015, Systems and software engineering—Systems lifecycle processes </p> |
| − | <p> ISO/IEC/IEEE 29148:2011, Systems and software | + | <p>ISO/IEC/IEEE 29148:2011, Systems and software engineering—Lifecycle processes—Requirements engineering</p> |
| − | + | ||
<h2>References</h2> | <h2>References</h2> | ||
<div id="One"></div><p>[1] A. C. Scott, J. Clayton, & E. Gibson, ''A Practical Guide to Knowledge Acquisition'', Addison-Wesley Publishing Company, 1991. </p> | <div id="One"></div><p>[1] A. C. Scott, J. Clayton, & E. Gibson, ''A Practical Guide to Knowledge Acquisition'', Addison-Wesley Publishing Company, 1991. </p> | ||
| Line 516: | Line 437: | ||
<div id="Ten"></div><p>[10] K. Wiegers, ''Requirements Analysis 3 (Developers Best Practices)'', Microsoft Press, 2003. </p> | <div id="Ten"></div><p>[10] K. Wiegers, ''Requirements Analysis 3 (Developers Best Practices)'', Microsoft Press, 2003. </p> | ||
<div id="Eleven"></div><p>[11] D. Leffingwell, ''Software Requirements: Lean Requirements Practices for Teams, Programs, and the Enterprise'', Agile Software Development Series, Addison-Wesley Professional, 2011.</p> | <div id="Eleven"></div><p>[11] D. Leffingwell, ''Software Requirements: Lean Requirements Practices for Teams, Programs, and the Enterprise'', Agile Software Development Series, Addison-Wesley Professional, 2011.</p> | ||
| − | <div id="Twelve"></div><p>[12] H. Podeswa, ''The Business | + | <div id="Twelve"></div><p>[12] H. Podeswa, ''The Business Analyst's Handbook'', Cengage Learning PTR, 2008.</p> |
Latest revision as of 02:08, 23 December 2017
|
Contents
- 1 Introduction
- 2 Goals and Principles
- 3 Context Diagram
- 4 Requirements Analysis and Design Process
- 5 Enterprise Analysis and EIT Change Initiative Inputs
- 6 Domain Elicitation
- 7 Requirements Analysis
- 8 Requirements Documentation
- 9 Conceptual and Logical Design Development
- 10 Solution Review, Verification, and Validation
- 11 Requirements Management and Communication
- 12 Summary
- 13 Key Maturity Frameworks
- 14 Key Competence Frameworks
- 15 Key Roles
- 16 Standards
- 17 References
1 Introduction
Requirements development and design uses a variety of elicitation techniques to gather a set of actionable, measurable, and traceable criteria (requirements). Some of these criteria are artifacts from previous work done, as described in the chapters on Strategy and Governance and Change Initiatives. The rest of the criteria are gathered by the requirements team to prepare for the construction (solution implementation) phase, described in the Construction chapter.
The requirements are said to belong to a particular domain—a specific sphere of activity or knowledge. A domain can correspond to the boundaries of an organization, a job function, or even a particular task.
These criteria/requirements are collected, analyzed, categorized, and documented in a series of artifacts, such as use cases, acceptance criteria, mockups, and market requirements. Finally, the criteria are morphed into a design for a product (good or service) or a set of product capabilities that meet the identified customer or organizational needs.
A design is a proposed solution, as described by a set of documents (and potentially, prototypes) that meets currently understood technical, non-functional, and business requirements. In essence, a solution specifies a set of changes to the current state of an enterprise that enables the enterprise to meet a need, solve a problem, or take advantage of an opportunity. In the requirements analysis phase of the project, the conceptual and logical designs of the solution are developed. The detailed technical design is created during the construction phase (see the Construction chapter).
Be aware that as the requirement analysis process is carried out, the requirements might change, both because of improved understanding of the domain and because of changing organizational conditions. This is especially true during projects that use iterative (agile) development approaches, where only part of the domain is worked on at one time.
The scope of the solution defines the portion of the domain that is part of the implementation. It is typically narrower than the full scope of the domain within which it is implemented.
This chapter covers both the process of collecting the criteria as well as creating and managing the artifacts that the result from the requirements process.
2 Goals and Principles
The goal for the requirements analysis and design phase is to collect all the data information required to develop an effective solution for the problem domain. In general, there are several principles that need to be followed during this process, including:
- Align requirements to the enterprise's strategies and goals as well as [1] EIT strategies and goals, as defined in the Strategy and Governance chapter.
- Ensure that the proposed conceptual and logical solution designs meet the objectives of the requirements.
- Develop requirements that are clear, unambiguous, usable, current, feasible, well-formed, and can be validated and traced.
- Provide the level of detail needed to understand and deliver the business capabilities and related features required to meet identified customer and organizational needs.
- Provide the level of detail needed to test and validate that the solution delivered meets the requirements.
- Provide the level of detail needed for customers or recipients to be ready to receive and use the delivered solutions.
3 Context Diagram
Figure 1. Context Diagram for Requirements Development and Design
Requirements development and design starts with a number of inputs. Many of these inputs are requirements defined by senior management. They indicate the enterprise's plans and goals. They specify the desired business and EIT architecture. Inputs usually include a use case or scenario that describes in general terms the solution that management is looking for. Along with the enterprise requirements, there should be a list of individuals who can supply important pieces of information or authority for the project.
The requirements project team often consists of several people who have a variety of skills including business analysis, solutions architecture, data modeling, user interface design, and project management. This team collects both high-level and detailed information during the project, and then documents, analyzes, and ensures that the solution chosen meets the enterprise requirements given to them by management. The team's output should give the implementation project team enough information to create and deliver the solution. It should also give the stakeholder organizations the information that they need to prepare for the changes required to their business processes.
4 Requirements Analysis and Design Process
The requirements process includes several different activities:
- Reviewing the requirements that have already been established
- Figuring out what information needs to be collected
- Collecting the requirements
- Analyzing the requirements (such as decomposing, modeling, and resolving inconsistencies)
- Documenting the requirements in a form suitable to those who use them
- Comparing the requirements with existing standards to evaluate for exceptions
- Reviewing and validating the requirements with stakeholders
- Creating a sufficiently detailed conceptual and logical designs for the solution that is consistent with the requirements
- Reviewing and validating the design with the implementation team
Although these activities seem to follow one another, it is often the case that in the middle of a project all these activities are going on simultaneously—often on different parts of the domain.
In some strategies, the requirements development team first lays out the high-level architecture of the conceptual design. The team then fills out the requirements feature by feature or function by function. This process is often used in iterative projects, so that parts of the system can be under construction while other parts of the domain are being specified.
For each of these activities, there isn't just one technique to use or list of things to accomplish. The size, complexity, and type of the project influences how the team steps through the requirements phase, what techniques the team uses to collect the requirements, and what artifacts the team creates to represent (communicate) the domain information to the stakeholders.
4.1 Requirement Types
Requirements fall into several categories. No one category is more important than another to define a successful solution.
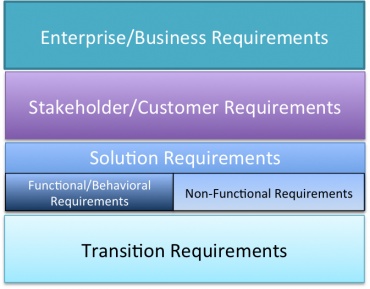
Figure 2. Types of Requirements
- Business requirements are the critical goals, objectives, and needs of an enterprise that must be met by the solution. They should indicate why the project was initiated and what metrics are used to measure the success of the solution.
- Stakeholder requirements are statements of the needs of a set of stakeholders associated with the project. They describe the needs of each stakeholder affected by the solution as well as how the stakeholder interacts with the solution. Often stakeholder requirements are a bridge between the business requirements and the detailed functional solution requirements.
- Solution requirements describe the specific characteristics of the solution (such as an application or an infrastructure build-out) that meet the requirements of both the enterprise and the stakeholders. The development of solution requirements constitutes the bulk of the requirements analysis process.
Solution requirements fall into two categories: functional and non-functional requirements. Functional requirements are those that describe specific behaviors or functions of the implemented solution (calculations, technical details, data manipulation and processing, and behavioral requirements). Non-functional requirements specify additional criteria often called qualities or just "-ilities" (execution performance, constraints, reliability goals, usability, security, testability, maintainability, extensibility, and scalability). The EIT Quality chapter describes the -ilities. Both types of solution requirements are important to ascertain and document. - Transition requirements describe the capabilities that the solution must have to facilitate the transition from the current state of the enterprise to the desired state. Transition requirements are fulfilled when the transition to the new state is complete, and are associated with issues such as filling workforce skill gaps, creating new resources, and converting data to a new format.
5 Enterprise Analysis and EIT Change Initiative Inputs
Requirements analysis typically starts with a request from the group who is in charge of enterprise change initiatives. In the best of all possible worlds, that request is a clear definition of the project including a set of enterprise-level artifacts (such as business and use cases, strategic plans, customer need descriptions, and results of a SWOT analysis) that describe the problem and the end product or functionality desired, and guide the project to its fruition.
Unfortunately, few projects start the requirements phase with all this information collected and documented. So the requirements team must first gather the existing information and then fill in the holes. Without the enterprise-level requirements, a project cannot be successful, because there is no target and no meaningful way to measure success.
The requirements team needs the following information, which comes out of the enterprise strategy work (see the Strategy and Governance chapter) and the change initiative effort (see the Change Initiatives chapter):
- Associated enterprise goals and requirements
- Associated enterprise strategies and governance
- The business case for the project
- A specific definition of the solution and its scope
- A list of stakeholders associated with the solution
There are a number of activities that can be extremely useful in collecting this information, including:
- Gap analysis (or needs assessment) is a technique that explores and describes the gap between the current actual enterprise or group performance (the "as is" state) and the desired performance with the solution (the "to be" state). This analysis focuses on the use of resources such as time, money, and workforce to produce the organization's desired level of performance. Gap analysis is a good tool to help define the solutions approach and scope.
- A strengths, weaknesses, opportunities, and threads (SWOT) analysis for the specific area of concern (often a specific objective) is an excellent tool to help focus the discussion on creating a solution that can have the optimum positive effect for the organization. It can guide requirements identification and analysis at all levels.
- Determining solution approach is an activity that investigates the most viable approach for a solution. It examines the business needs, organizational processes, and required capabilities, and ends up with a description of the approach that should be taken to implement the new set of capabilities. It requires documenting assumptions and constraints; ranking approaches based upon performance improvement estimations and benchmarking; and collecting performance requirements such as availability, response time, accessibility, and maximum throughput.
6 Domain Elicitation
A large portion of the requirements development process is associated with simply collecting the right information, referred to as domain elicitation. This activity is associated with gathering information from subject matter experts (SMEs), stakeholders, or consumers about how the solution should function. Let's say that the solution is to provide expertise or guidance to a junior repair technician. The team must collect the repair expertise and guidance from an SME so that the solution can provide the correct repair guidance to the user.
There are entire books written about domain elicitation or knowledge acquisition as it is referred to in some areas. [1] Strong interviewing skills are a requirement for the team members. The interviewer develops an expertise over time for guiding the SME to deliver useful information in an efficient manner. In this section, we list a few basic approaches that can help.
6.1 Plan Your Approach and Prepare for the Elicitation
Planning for elicitation sessions is critical. There should be a plan for both the project as a whole, as well as a plan for each elicitation session. The overall plan should include the different sessions required, what needs to be collected, and the associated stakeholders. This is a high-level plan and evolves during the project.
The plan for each session should have significantly more detail. Among other things there should be:
- A well-defined goal
- An agenda
- A list of supporting materials needed at the session
- The stakeholders that must attend along with their role
Why all this structure? Staying focused on the task at hand is necessary for success in an elicitation session. Usually it is difficult to get stakeholders to attend meetings in the first place. It is critical to use their time wisely by collecting as much information from them as possible. In addition, collecting all (or most) of the information about one small topic is much more efficient that collecting pieces of the puzzle in multiple sessions. Having all (or most) of the information leads to better analysis results.
6.2 Conduct the Elicitation Activity
There are several tools that are extremely useful during the elicitation process:
- Scenarios—It can be very useful to go through a number of scenarios in detail. A scenario is an end-to-end walk through of a process, such as identifying a fault to repair, or maybe purchasing car insurance. It examines one path through the process and also includes rationale for any decisions or distinctions that are made during the process. The rationale can indicate why particular questions are asked of a user, why the solution takes a particular path, or why certain recommendations are made to a user. Document any paths that should not be used, as well.
The amount of detail that you need to collect in the scenario depends upon the scope of the solution. At times, scenarios can be the most critical tool in the elicitation toolbox, because they provide not only a means to collect the information to create the solution, but also provide a basis for creating test cases for testing the solution after it is implemented.
A domain might be small enough that only a couple scenarios are sufficient to guide the solution definition; however, some projects are large enough to require several hundred scenarios to cover the entire domain.
Scenarios can become use cases in the requirements document. - Observe people working or doing the activity—Sometimes people cannot describe what they do. For example, try to tell someone how to tie their shoes without looking at your own shoes. Instead, the elicitation team can watch the stakeholder or SME perform the task in question.
This technique is just a special instance of a case study. Asking clarifying questions while the SME performs the task can provide the critical knowledge required to develop the solution. This technique also identifies data sources and job aids that people use to perform the task that could become an important part of the solution. - Stories—SMEs often tell stories about what has happened in the past that provide useful information about both functional and non-function requirements. They might talk about an interaction with a customer or a problem that occurs frequently. The difficulty with stories is that people often ramble on without saying anything useful. The discussion is fun to listen to, but it doesn't provide information that is useful to the final solution. It is up to the interviewer to keep the discussion focused on useful information. A skillful interviewer gently guides the storyteller back to the topic.
6.3 Document the Elicitation Results
Notes about elicitation sessions are very important. They need to be detailed, because it is often difficult to tell what information is important during or shortly after the interview. Sometimes, the team discovers that the SME dropped a true gem of information that is not recognized for several weeks. If the notes are detailed, you can go back and pick up the additional information at a later time. It may be useful to have the note taker be someone who is not asking questions, so that each person can maintain focus on their specific activity.
The notes become input for the requirements analysis process and for documenting the requirements. At times, the scenarios discussed in the interviews only require polishing at those later stages.
Beyond documenting what you heard or saw during the elicitation process, you should also make notes about:
- Information collected that might indicate business requirements or transition requirements that have not been identified yet
- Areas of the domain that had not been identified yet
- Issues that are beyond the scope of that interview that need to be discussed
- Information that might contradict requirements that have been previously collected
- Other sources of information (maybe other SMEs)
7 Requirements Analysis
After the information has been collected through the elicitation process, it needs to be analyzed. This analysis process takes a careful look at all the information and puts it in context with the other information (requirements) that has been collected.
7.1 The Requirements Analysis Process
The analysis process can be described by a number of activities: organize, model, verify, remedy inconsistencies, define assumption, define constraints, prioritize, and ensure completeness. Although the type of project demands different amounts of time with each of these activities, all of these activities are important for the proper analysis of the information collected.
7.1.1 Organize
The most important activity is to organize the requirements (information) based upon type, level, and role. Typically, the information is organized into three groups:
- Processes associated with the domain—These are the steps in a flow of activities, whether high or low level. This information is modeled in flowcharts, Gantt charts, sequence diagrams, state diagrams, or other representations.
- The data required for or produced by the processes or tasks in the domain—Data can represent information at a number of levels. Low-level data consists of numbers, names, and other base-level information. High-level data consists of mathematical results or logical conclusions made based upon the base-level data. Data models are critical for designing databases and the solution's data structures.
- The business rules that drive the solution—Business rules are statements that indicate whether an actor can or cannot do something. They also provide the conditions and criteria for making a decision. For example, "a user must have an account to make a purchase." In essence, a business rule is an implementation of a business requirement.
To describe all aspects of the information collected during elicitation, there are several different kinds of documents created, as described in the Requirements Documentation section. These documents need to be comprehensive, complete, consistent, and understood by all stakeholders.
7.1.2 Specify and Model
Specifying and modeling the information takes the organization process to another level. The goal of this activity is to start formulating the details of the solution. Often this activity describes and models information, such as:
- Current ("as is") state of the organization
- Needs and desires of the stakeholders for the ("to be") solution
- Models of the business logic currently being used
- Details about the data, and how it needs to be defined and organized
- How the data flows through the processes
- How decisions are made and the contexts that they are made in
- How the processes flow and what intermediate states can be identified
- Under what scope each of the requirements, data, and processes applies
The result of the specification and modeling task are a host of analysis documents described in Requirements Documentation, including state diagrams, data modeling diagrams, business rule documents, sequence diagrams, and use cases. [7] [8]
7.1.3 Verify Completeness
One of the parts of the analysis process is verifying that you have collected all the information you need. It is often the case that the team discovers during analysis or documentation that they don't have everything that they need to define a solution; there are holes in their information that can block the implementation team from finishing the solution. While the completion verification process is not easy, it is critical.
7.1.4 Identify and Remedy Inconsistencies
Not only is data often incomplete, it is also often inconsistent or even contradictory. The inconsistencies can be obvious; however, at times the inconsistencies are subtle, such as data being used as an integer in one context and a real number in another. Business rules might be contradictory in subtle ways, hiding the inconsistency until lower-level requirements based upon the inconsistent rules are identified as being inconsistent.
It is the role of the analyst to identify inconsistencies in the process as soon as possible, and then to go back to the sources to get the inconsistencies resolved. There are several techniques, such as using quasi-classical logic to resolve the issues. [2]
7.1.5 Define Assumptions
Assumptions are factors upon which design decisions are made, which are believed to be true, but have not been or cannot be confirmed at the time of collecting the requirements. Assumptions can affect all aspects of a project, and their associated uncertainty adds a certain degree of risk to the project. It is crucial to identify, document, and attempt to confirm all assumptions in order to manage their associated risks. Assumptions are one of the major factors associated with problem tracking and risk analysis.
Some assumptions are high risk. For example, if you are running an app on a mobile device, you might have an assumption that Wi-Fi is available. Or maybe, your app depends on the user being able to hear the device. If either of these assumptions is incorrect, the application doesn't work or isn't useful as designed.
Assumptions can also be low risk. These are assumptions that define boundary or likely conditions for the solution, such as how a user is likely to respond to a particular situation.
7.1.6 Define Constraints
During the project, it is typical to identify constraints on the solution. Constraints are restrictions or limitations on solutions imposed by outside influences, whether by the EIT infrastructure, organizational policies and culture, legal requirements for safety, privacy, budget, available resources, or schedule. It is critical to identify, document, and publish constraints as part of the problem-tracking process. Constraints figure heavily in the prioritization process.
7.1.7 Prioritize
More often than anyone would like to admit, requirements conflict with one another. You might need some functionality but have no budget to implement it. You might have a requirement for putting the application on a smart phone or tablet, but it requires significantly more horsepower and space than is available on the device.
One of the tasks is to determine (and document) the relative importance of requirements based upon the value to the enterprise, business risk, technical risk, the difficulty to implement, or likelihood of success. Regulatory or policy compliance (legal) can also be a critical aspect. Even a requirement's relationship to other requirements, such as a critical dependence, needs to be considered.
The difficulty with this task is that it often requires stakeholder approval—maybe approval from all the stakeholders. And, they often have differing opinions on the relative value and risk associated with requirements. Often there are "non-negotiable" demands and unrealistic tradeoffs that need to be addressed.
Several techniques are particularly helpful in this area, such as decision analysis, MoSCoW (acronym for Must have, Should have, Could have, and Would like but won't get) analysis, risk analysis, time boxing, and budgeting.
7.1.8 Ensure Completeness of the Analysis
All of this analysis is useless if the analyst team does not make sure that each requirement is well-formed and completely specified, as described in Qualities of Well-Formed Requirements.
7.2 Qualities of Well-Formed Requirements
There are a number of sources that define the properties of well-formed or "good" requirements. [3] [4] These beneficial characteristics help ensure that the requirements process is complete and that it results in a successful solution implementation. The more critical and more complex the project, the more important these qualities are.
- Clear and unambiguous—Can all stakeholders and solution implementers understand the requirement? Is there any disagreement about what the requirement means? Each requirement needs to be specified (or modeled) in a way that is clear and unambiguous.
- Usable—Is the requirement useful in creating or defining the solution? Requirements that are not useful or usable confuse the situation and the solution definition process.
- Current—Does the requirement reflect the current situation or where the solution must head? Requirements should not conduct history lessons and should not tell stories about the past. They need to reflect the current situation or where the organization needs to head.
- Traceable—Do you know where the requirement came from? It is critical to know the source of each piece of information. Did it come from an interview with an SME? Is it from a particular manager or executive? If another requirement appears to be in conflict with it, do you know who to discuss the issue with?
- Granular—Is there only one criterion/data item in the requirement? It is critical to be able to distinguish between the pieces of information. This isn't as easy as it seems. It is hard to get individuals to disambiguate issues, so they often develop requirements/goals that address both issues, when they should split the issues and then develop new business rules.
- Measurable success criteria—Is the requirement written in a way in which you can measure whether it has been satisfied? Can these measurements be incorporated in tests and in release criteria?
7.3 Requirements Verification and Validation
Validation and verification happen frequently during the requirements, design, and construction processes. They ensure that the implemented solution truly fills the gap identified by the enterprise. Validation and verification during the requirements analysis phase has a particular slant:
- Requirements validation ensures that all requirements reflect the customer's real needs. Because there is no prototype available at this point, this means asking the stakeholders to validate that the requirements and resulting analysis support their needs.
- Requirements verification ensures that the results of the analysis process are consistent with previously collected requirements. This process verifies robustness, correctness, and consistency among all requirements and analysis results.
8 Requirements Documentation
There are a number of ways to document criteria/requirements/data that is collected during the requirements analysis process. The techniques or document types that are needed depend on the type of domain and the nature of the solution. One size does not fit all; however, the list below includes the most commonly used documents. Each of these document types are text-based; diagrams (described below) can be added for additional clarity.
8.1 Text-based Documentation
- Interview transcripts can be relatively unstructured documents that follow the flow of the interview. There are a few characteristics that help them be effective documents. They should be dated and all participants should be listed. The purpose of the interview should be stated up front. The person making each statement should be clearly indicated. More advanced analysts also color code statements that indicate different kinds of information, or they add comments after the fact to shed light on the importance of a statement or action that needs to be performed because of the statement. It is also helpful to make notes about topics that should be covered in future sections.
- Scenarios and use cases are predominantly a list of steps that someone takes to perform a task. The steps often document an interaction with a system, such as a computer application, but they could be steps that a repairman takes to identify and fix a problem. Why use one versus the other?
As mentioned earlier, scenarios go through a single path of the process. They don't cover multiple possible outcomes or alternative flows. Scenarios are great elicitation tools and are often used by the QA team to create tests for a single logical path through the domain. The QA team can use the scenario as a gold standard of the interaction between the solution and the user.
Use cases, however, cover multiple outcomes and alternate flows. Use cases are better at guiding the developer in building the solution. They describe all the options available for the user at a given point. They build a more complete picture of the current state and all the options that the user has. There are lots of templates available for use cases and they are often considered a critical tool in the solution-definition process. For a good how-to reference, refer to Writing Effective Use Cases. [5] - Data dictionary is a dictionary of data items. This repository of information describes each item including its meaning, origin, use, data type, possible values, and relationship to other data. A data dictionary is a critical repository for any application that contains a significant number of data items.
- Security, privacy, and data classification—Enterprise solutions require a security plan. These plans are usually separate documents that cover all the security risks and the means for addressing them. The plan should list all the assets that need to be protected, the associated risks with each asset, the way to protect the assets, and the cost of protection. Basic questions include: How are users going to be authenticated? How is personal data going to be protected? What data needs to be protected? [6]
- Business rules define how the enterprise operates. They are statements or conditions that indicate what actions individuals can perform or what decisions they can make. A business rule might be something like: An online store customer must have a valid email address. Business rules must be stated precisely. Slight changes in wording can make a huge difference in how the requirements are developed. Rules need to have owners and they need to be easily found and tracked.
- Metrics for testing and release criteria—A key aspect of specifying requirements is identifying the criteria that are used to determine whether the requirement has been satisfied (the definition of Done). When requirements are well formed, they contain the measures of success for the intended application or solution. These measures need to be captured as the evaluation and acceptance criteria for the solution. In other words, how do you know when the solution is good enough? What conditions must the solution satisfy to be accepted by the stakeholders?
Typically there is a document that collects these necessary conditions and labels them as release criteria. These criteria specify how the solution performs, as well as expectations of how the organization performs with the solution. These criteria are sometimes called the solution's key performance indicators (KPIs). They should be included in tests and can be things such as the response time during a session, accuracy/relevance of a recommendation to a user, uptime of the solution, or mean time between failure. The KPIs for the organization can be metrics such as the level of customer satisfaction, the number of defects per 1000 units, labor spent per month, burn-down rates, or the return on investment (ROI).
8.2 Graphic-based Documentation
Diagrams are useful for illustrating what would take many paragraphs to explain. Diagrams do not stand alone as documentation—descriptions of the diagrams are also important.
- Sequence diagrams describe a process. They show how processes operate or interact with one another. They are often referred to as event diagrams or event scenarios. There is a specific visual language used with these diagrams.
- State diagrams are used to model behavior. There are several different kinds of state diagrams, but most represent states of a system (e.g., on and off) using objects (such as circles) with lines from one circle to another that represent an event or action taken to get from one state to another. State diagrams are not flowcharts, which describe process flows. See example below.
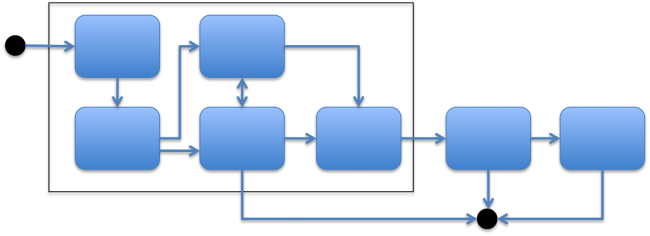
- Data flow diagrams are graphic representations of the flow of data through an information system. They show the flow of inputs and outputs through the system and its components, and where the data is stored. These diagrams can be used at a number of levels to describe the system. See example below.
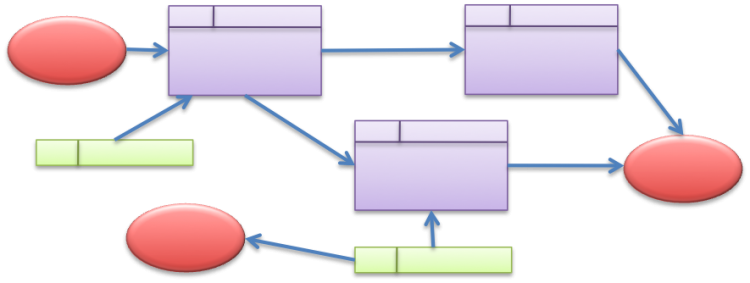
- Decision tables, trees, and rules are tools used to model decisions and their consequences. They model algorithms. They often lead from observations to conclusions. There are several different ways to use these representations and they are closely related to influence diagrams. See example below.

8.3 Image Creation Accepted Practices
When creating diagrams for requirements documentation, there are some guidelines that can help make your images more readable and understandable.
- Choose a direction for your flow. All arrows should point in the same general direction as much as possible. The reader then can start from one end of the diagram and follow the paths to the other end. Circular flows are acceptable, as long as there is a definable path.
- Use a legend, and keep the legend in the same area of all images. Pick a corner or a side for the legend location. All legend elements should be in the same place on the diagram so the reader does not have to screen out multiple areas when reading the diagram.
- Use the same size icons for the same things. Different sizes of icons for similar objects makes it appear that the items are different somehow, and is distracting if there is no reason for dissimilar sizes.
- Create templates for common image types if possible, so that all diagrams use the same icons for the same thing, similar to the way flowchart elements have a standard icon list.
8.4 Important Characteristics of the Documents
The documents themselves need to have many of the same characteristics as the requirements:
- Understandable and usable—The documents need to be understandable and usable, and not just by the person who wrote them. These documents are likely to be read and reviewed by many stakeholders including SMEs, users, management, and solution implementers. Each reader should find them usable and useful. For example, a tester should find information critical to designing tests; a writer composing a user manual needs to understand how the user's actions are responded to; customer support needs to know how the solution works, such as if there are known problems and known workarounds; and so on.
- Consistent—The requirements documents cover the description of many requirements and it is critical that there is consistency of terminology, structure, and tone between the documents. For example, a characteristic of a situation that is used to make a logical conclusion in a case study should be included in the data dictionary. In addition, the name and the qualities of that item should be the same in both documents. Keeping the documents consistent takes considerable effort, but it is absolutely necessary to ensure a robust solution design.
- Current—These documents need to be kept current. These documents are not useful if they are behind the elicitation and analysis activities by weeks or months. They should be updated within days of collecting new information.
- Traceable—The information in each of the documents as well as the documents themselves need to be traceable. The owners of the documents should be clear. There should be a change-tracking system associated with these documents so that all stakeholders know when particular information was added or changed, and by whom.
- Organized and modifiable—It is inevitable that some requirement previously gathered will change when analyzed. Organize and label the requirements to enable searching.
9 Conceptual and Logical Design Development
The requirements elicitation and analysis process is inextricably intertwined with the development of the solution's conceptual and logical design. You can't have one team collect the requirements and data, and then have another team do the design, because having intimate knowledge of the requirements analysis results is critical. On the other hand, the solution design process requires skills beyond those needed for requirements gathering. Therefore, team members who are solution design experts, such as UI designers, system architects, and data engineers, need to become involved as the requirements evolve in specificity.
At this point, it is important to make some distinctions about the design process. Most sources divide the design process into three phases:
- The conceptual design describes the proposed solution in a functional manner that could be easily understood by a future user. It describes how the solution looks and behaves.
- The logical design defines objects, entities, their attributes, and their relationships. It also describes the business rules associated with these entities.
- The physical design is where the other two designs are converted to a definition of how the solution is implemented in hardware, software, and potentially other media. The physical (a.k.a. technical) design is developed by the construction team, not by the requirements team (see the Construction chapter).
9.1 Solution Components
The majority of business solutions are composed of multiple components. Each component is associated with a subset of the requirements, and it is important to understand which requirements are driving the design of a particular component.
Solution components can include:
- Business policies and business rules
- Business processes to be performed and managed
- Job functions and responsibilities of the people who operate and maintain the solution
- Software applications and application components used in the solution
- Supporting hardware (such as servers) for processing efficiency, data storage, additional networking capabilities, or new capabilities like voice inputs, mobile applications, and 3-D printers
- Structure of the organization, including interactions between the organization, its customers, and its suppliers
9.2 Design Techniques
There are a number of techniques used during the design process that enable the team to develop an optimized solution for the set of requirements. A few of these are listed below.
- Impact analysis—Understanding the impact of each component and function is critical to determine what functionality is implemented in the solution and when it is implemented. Impact analysis identifies the potential consequences of a change or estimates what needs to be modified to accomplish a change, as defined in A Guide to the Business Analysis Body of Knowledge. [8]
A good impact analysis report includes a detailed cost/benefit analysis. It outlines the risks, costs, and business requirements that are being met. It shows the links between requirements both in respect to dependency and traceability. The design team uses the impact analysis report to determine the scope and prioritization of the solution implementation. They may also find a need to refine the report as they work on the details of the scoping and prioritization. - Prioritization of development—The design team works with stakeholders, the impact analysis, and the enterprise requirements to develop a priority order for the development of the requirements and components. Prioritization might also drive changes in project scope.
- Scoping—This process determines what is and is not included in the solution. This might include functionality, requirements, cost, timing, and personnel. Scoping is often an effective technique for staging the development of a solution. For example, an organization can implement low-cost and easy-to-implement solutions first, and then add the more expensive and harder components later.
Iterative and incremental development approaches (such as scrum, agile, lean manufacturing, DSDM, and spiral) split the total scope of the project into smaller chunks. This allows stakeholders to adjust a project's requirements or goals after they see prototypes or demonstrations that have partial functionality. The stakeholders along with the development team determine the features to include at each iteration cycle. After each cycle, the next cycle's features are selected and the requirements analysis, design, and construction phases occur for the new cycle. At times, the results of a cycle provide information that prompts an adjustment to the full scope of the project. - Prototyping or proof of concept (POC)—This technique creates a preliminary version or model of the final solution. We often think of creating a prototype for computer programs or machines; however, the technique is equally valid for job aids, job descriptions, training programs, and so on. The job of the prototype is to illustrate the qualities and functionality of the component. Prototypes are especially effective, because users can experience them and give detailed feedback on how well they meet their needs. Prototypes are also effective vehicles for identifying faulty assumptions and missing functionality.
- Security design—Security design has become increasing important over the last 30 years. The team must understand the security requirements and design the features necessary to meet them. The design needs to take into account authorization and authentication, data encryption, user and data privacy, data auditing, non-repudiation, and conformance to standards. See the Security chapter for more information.
9.2.1 Alternatives Analysis: Functionality Reallocation
During solution design, it is often necessary to reallocate functionality between the different solution components. The reason for this is often the cost required to develop or maintain the solution. For example, it might cost too much to implement a computer application to provide some functionality, so simpler job aids are created instead. Or perhaps a desired new business rule requires too much manpower to implement to make it worth the benefit received. In general, when the design process is well underway and the cost to implement each component becomes evident, the team can determine which functionality allocations have the best cost/benefit ratio for the enterprise.
10 Solution Review, Verification, and Validation
Verification is one of the most important things to do after creating a conceptual and logical solution design. Stakeholders must assess proposed solutions to see if they meet all stakeholder and solution requirements. This verification process ensures that requirement specifications, models, and prototypes meet the necessary standard of quality for the solution to be correct and of acceptable quality. The process determines whether a solution design component is ready for formal review and signoff.
One of the activities during this process is to validate that requirements are met. This means that the requirements, as they are manifested in the solution design, support the delivery of value to the business, fulfill the enterprise's goals and objectives, and meet the stakeholders' needs. To ensure that this is the case, it is often valuable to define detailed acceptance and evaluation criteria. Key metrics and key performance indicators for the solution are also often developed.
Sometimes a design appears to meet all the criteria, but when the stakeholders (especially future users) see the design through structured walkthroughs or interaction with a prototype, they point out issues with the design. Often these issues are associated with requirements that were never collected or ones that were not well understood. But often, the solution just isn't mature enough. It is common for a design to be refined three or more times during the review and validation process.
A solution needs to be complete, correct, consistent, unambiguous, cohesive, testable, robust, and feasible; if not, the solution should not be approved. Most of these qualities were covered with respect to requirements qualities (see Qualities of Well-Formed Requirements). There are four qualities that are specific to the conceptual and logical solution design:
- Feasible—The design can be successfully implemented.
- Cohesive—All components of the solution are well integrated and unified. In addition, the components of the solution are created so that their role is clear, complete, and easily distinguished from the other components.
- Testable—A solution is testable when its functionality and its ability to address the goals of the project can be tested and measured.
- Robust—A solution design is robust when it covers not only the base-level functionality, but also the ability to cope with errors during use. That is, the solution can continue to operate in a reasonable way even if it receives abnormal inputs or encounters unforeseen situations.
The review with the stakeholders can take several forms. It can be a walkthrough of a paper solution component with the relevant stakeholders, users working with a prototype, or stakeholders determining which one of several competing solutions is the best. Each solution component has an associated method for review and validation. Each component should also have its own acceptance and performance criteria.
11 Requirements Management and Communication
Throughout the requirements and design process, managing and communicating the requirements, the state of analysis, and the solutions/designs is a vital activity. The success of the project often reflects the ability of the team to manage and communicate, and that often requires a requirements management plan. This plan defines the process of documenting, analyzing, tracing, prioritizing, and agreeing on requirements. It states clearly who attends and who approves during reviews.
At the heart of the communication process is developing a shared understanding of the requirements among all the stakeholders, dealing with conflicts and disagreements when they arise, and then securing approvals from the stakeholders.
When approvals for the requirements and solution designs have been acquired, the team transfers the package to the construction team. Sometimes the construction team is engaged before the requirements effort is done. It is common for the construction team to work on a subsection of the project, while the requirements analysis and solution design process continues on other sections. It is also important to note that transferring the package to the construction team often requires face-to-face training, or that a member of the requirements team works with the developers during the construction process to keep them from straying from the approved requirements and design, and answering any questions that may arise before rework is necessary.
The lifetime of the requirements does not end when the development phase is over; many requirements are valid beyond the scope of one project. It is essential that the requirements are maintained for long-term use (reuse) by the enterprise. As such, the requirements and other artifacts need to be well labeled and stored in a repository where other projects can get access to them. Subsequent projects on the same system may be able to reuse substantial parts of requirements to prevent changes to the system, and feed into regression testing requirements.
12 Summary
The requirements analysis or requirements specification process is often the most complex stage of defining and building an EIT solution. It takes a number of skills and knowledge of many techniques to create a complete and verifiable set of requirements. Expertise in requirements analysis takes years of work; it is best to learn as an apprentice, where one can watch an expert analyst work through the process.
The activities in this phase are not typically sequential. Many activities overlap and requirements analysis for one part of the domain may overlap with construction of another part of the solution. It is even necessary to take knowledge acquired during implementation and feed it back into the requirements process.
This stage is a key to having a successful solution that meets the business criteria, stays within budget, and is easily maintained. For general books on the topics of software requirements and specifications, refer to [8], [9], [10], [11], and [12].
13 Key Maturity Frameworks
Capability maturity for EIT refers to its ability to reliably perform. Maturity is measured by an organization's readiness and capability expressed through its people, processes, data, technologies, and the consistent measurement practices that are in place. See Appendix F for additional information about maturity frameworks.
Many specialized frameworks have been developed since the original Capability Maturity Model (CMM) that was developed by the Software Engineering Institute in the late 1980s. This section describes how some of those apply to the activities described in this chapter.
13.1 IT-Capability Maturity Framework (IT-CMF)
The IT-CMF was developed by the Innovation Value Institute in Ireland. This framework helps organizations to measure, develop, and monitor their EIT capability maturity progression. It consists of 35 EIT management capabilities that are organized into four macro capabilities:
- Managing EIT like a business
- Managing the EIT budget
- Managing the EIT capability
- Managing EIT for business value
The three most relevant critical capabilities are user experience design (UED), solutions delivery (SD), and service provisioning (SRP).
13.1.1 User Experience Design Maturity
The following statements provide a high-level overview of the user experience design (UED) capability at successive levels of maturity.
| Level 1 | There is no official recognition of user experience as a discipline within the organization. EIT services and solutions are not typically considered user-friendly. |
| Level 2 | Defined user experience approaches are emerging in the design and development of a limited number of EIT services and solutions. The user experience of most EIT services and solutions is improving |
| Level 3 | Standardized user experience approaches guide the design and development of most EIT services and solutions, which increasingly enable users to accomplish their tasks and goals easily, efficiently, and accurately. |
| Level 4 | Comprehensive user experience approaches are used during the design and development of all EIT services and solutions, so that they are generally suitable for their audiences, purposes, and contexts of use. |
| Level 5 | User experience approaches are adopted, and are continually reviewed for improvement opportunities. EIT services and solutions offered/brokered by the EIT function consistently provide richer user experiences when compared to market alternatives. |
13.1.2 Solutions Delivery Maturity
The following statements provide a high-level overview of the solutions delivery (SD) capability at successive levels of maturity.
| Level 1 | There is ad hoc use of solutions delivery methodologies. EIT solutions are typically delivered with wide variations in quality, schedule, and cost expectations. |
| Level 2 | Basic solutions delivery methodologies are defined and applied to a limited number of EIT solution projects, which are beginning to meet expectations, but variations in quality, schedule, and cost still occur. |
| Level 3 | Standardized solutions delivery methodologies are applied to most EIT solution projects, enabling many of them to regularly meet expectations for quality, schedule, and cost. |
| Level 4 | Comprehensive and flexible project delivery methodologies are applied to all projects, enabling most projects to meet expectations for quality, schedule, and cost. |
| Level 5 | Solutions delivery methodologies are continually analyzed and refreshed. Solutions delivery expectations for quality, schedule, and cost are nearly always met. |
13.1.3 Service Provisioning Maturity
The following statements provide a high-level overview of the service provisioning (SRP) capability at successive levels of maturity.
| Level 1 | The service provisioning processes are ad hoc, resulting in unpredictable EIT service quality. |
| Level 2 | Service provisioning processes are increasingly defined and documented, but execution is dependent on individual interpretation of the documentation. Service level agreements (SLAs) are typically defined at the technical operational level only. |
| Level 3 | Service provisioning is supported by standardized tools for most EIT services, but may not yet be adequately integrated. SLAs are typically defined at the business operational level. |
| Level 4 | Customers have access to services on demand. Management and troubleshooting of services are highly automated. |
| Level 5 | Customers experience zero downtime or delays, and service provisioning is fully automated. |
14 Key Competence Frameworks
While many large companies have defined their own sets of skills for purposes of talent management (to recruit, retain, and further develop the highest quality staff members that they can find, afford and hire), the advancement of EIT professionalism will require common definitions of EIT skills that can be used not just across enterprises, but also across countries. We have selected three major sources of skill definitions. While none of them is used universally, they provide a good cross-section of options.
Creating mappings between these frameworks and our chapters is challenging, because they come from different perspectives and have different goals. There is rarely a 100 percent correspondence between the frameworks and our chapters, and, despite careful consideration some subjectivity was used to create the mappings. Please take that in consideration as you review them.
14.1 Skills Framework for the Information Age
The Skills Framework for the Information Age (SFIA) has defined nearly 100 skills. SFIA describes seven levels of competency that can be applied to each skill. However, not all skills cover all seven levels. Some reach only partially up the seven-step ladder. Others are based on mastering foundational skills, and start at the fourth or fifth level of competency. SFIA is used in nearly 200 countries, from Britain to South Africa, South America, to the Pacific Rim, to the United States. (http://www.sfia-online.org)
| Skill | Skill Description | Competency Levels |
|---|---|---|
| Availability management | The definition, analysis, planning, measurement, maintenance, and improvement of all aspects of the availability of services, including the availability of power. The overall control and management of service availability to ensure that the level of service delivered in all services is matched to or exceeds the current and future agreed needs of the business, in a cost-effective manner. | 4-6 |
| Business analysis | The methodical investigation, analysis, review, and documentation of all or part of a business in terms of business functions and processes, the information used, and the data on which the information is based. The definition of requirements for improving processes and systems, reducing their costs, enhancing their sustainability, and the quantification of potential business benefits. The collaborative creation and iteration of viable specifications and acceptance criteria in preparation for the deployment of information and communication systems. | 3-6 |
| Business modeling | The production of abstract or distilled representations of real world, business, or gaming situations in traditional or trans-media applications, to aid the communication and understanding of existing, conceptual, or proposed scenarios. Predominantly focused around the representation of processes, roles, data, organization, and time. Models may be used to represent a subject at varying levels of detail and decomposition. | 2-6 |
| Business process improvement | The identification of new and alternative approaches to performing business activities. The analysis of business processes, including recognition of the potential for automation of the processes, assessment of the costs and potential benefits of the new approaches considered, and, where appropriate, management of change, and assistance with implementation. May include the implementation of a process management capability/discipline at the enterprise level. | 5-7 |
| Continuity management | The provision of service continuity planning and support. This includes the identification of information systems that support critical business processes; the assessment of risks to those systems' availability, integrity, and confidentiality; and the co-ordination of planning, designing, testing, maintenance procedures, and contingency plans to address exposures and maintain agreed levels of continuity. This function should be performed as part of, or in close cooperation with, the function that plans business continuity for the whole organization. | 4-5 |
| Data analysis | The investigation, evaluation, interpretation, and classification of data, in order to define and clarify information structures that describe the relationships between real world entities. Such structures facilitate the development of software systems, links between systems, or retrieval activities. | 2-5 |
| Data management | The management of practices and processes to ensure the security, integrity, safety, and availability of all forms of data and data structures that make up the organization's information. The management of data and information in all its forms and the analysis of information structure (including logical analysis of taxonomies, data, and metadata). The development of innovative ways of managing the information assets of the organization. | 2-6 |
| Emerging technology monitoring | The identification of new and emerging hardware, software and communication technologies and products, services, methods, and techniques and the assessment of their relevance and potential value as business enablers, improvements in cost/performance, or sustainability. The promotion of emerging technology awareness among staff and business management. | 4-6 |
| Enterprise and business architecture | The creation, iteration, and maintenance of structures such as enterprise and business architectures embodying the key principles, methods, and models that describe the organization's future state, and that enable its evolution. This typically involves the interpretation of business goals and drivers; the translation of business strategy and objectives into an "operating model"; the strategic assessment of current capabilities; the identification of required changes in capabilities; and the description of inter-relationships between people, organization, service, process, data, information, technology, and the external environment.
The architecture development process supports the formation of the constraints, standards, and guiding principles necessary to define, ensure, and govern the required evolution; this facilitates change in the organization's structure, business processes, systems, and infrastructure in order to achieve predictable transition to the intended state. | 5-7 |
| Information assurance | The protection of integrity, availability, authenticity, non-repudiation, and confidentiality of information and data in storage and in transit. The management of risk in a pragmatic and cost-effective manner to ensure stakeholder confidence. | 5-7 |
| Information management | The overall governance of how all types of information, structured and unstructured, whether produced internally or externally, are used to support decision-making, business processes, and digital services. Encompasses development and promotion of the strategy and policies covering the design of information structures and taxonomies, the setting of policies for the sourcing and maintenance of the data content, and the development of policies, procedures, working practices, and training to promote compliance with legislation regulating all aspects of holding, use, and disclosure of data. | 4-7 |
| Information security | The selection, design, justification, implementation, and operation of controls and management strategies to maintain the security, confidentiality, integrity, availability, accountability, and relevant compliance of information systems with legislation, regulation, and relevant standards. | 3-7 |
| Information systems coordination | Typically within a large organization in which the information strategy function is devolved to autonomous units, or within a collaborative enterprise of otherwise independent organizations, the coordination of information strategy matters where the adoption of a common approach (such as shared services) would benefit the organization. | 6-7 |
| Innovation | The capability to recognize and exploit business opportunities provided by information and communication technology, accepted practices, methods, and standards, to ensure more efficient and effective performance of organizations, to explore possibilities for new ways of conducting business and organizational processes, and to establish new services or businesses. | 5-6 |
| EIT strategy and planning | The creation, iteration, and maintenance of a strategy to align EIT plans with business objectives and the development of plans to drive forward and execute that strategy. Working with stakeholders to communicate and embed strategic management via objectives, accountabilities, and monitoring of progress. | 5-7 |
| Network planning | The creation and maintenance of overall network plans, encompassing the communication of data, voice, text, and image, in the support of an organization's business strategy. This includes participation in the creation of service level agreements and the planning of all aspects of infrastructure necessary to ensure provision of network services to meet such agreements. Physical implementation may include copper wire, fiber optic, wireless, or any other technology. | 5-6 |
| Portfolio, program, and project support | The provision of support and guidance on portfolio, program, and project management processes, procedures, tools, and techniques. Support includes definition of portfolios, programs, and projects; advice on the development, production, and maintenance of business cases; time, resource, cost, and exception plans; and the use of related software tools. Tracking and reporting of program/project progress and performance are also covered, as is the capability to facilitate all aspects of portfolio/program/project meetings, workshops, and documentation. | 2-6 |
| Project management | The management of projects, typically (but not exclusively) involving the development and implementation of business processes to meet identified business needs, acquiring and utilizing the necessary resources and skills, within agreed parameters of cost, timescales, and quality. | 4-7 |
| Requirements definition and management | The definition and management of the business goals and scope of change initiatives. The specification of business requirements to a level that enables effective delivery of agreed changes. | 2-6 |
| Service level management | The planning, implementation, control, review, and audit of service provision, to meet customer business requirements. This includes negotiation, implementation, and monitoring of service level agreements (SLAs), and the ongoing management of operational facilities to provide the agreed levels of service, seeking continually and proactively to improve service delivery and sustainability targets. | 2-7 |
| Solution architecture | The design and communication of high-level structures to enable and guide the design and development of integrated solutions that meet current and future business needs. In addition to technology components, solution architecture encompasses changes to service, process, organization, and operating models. Architecture definition must demonstrate how requirements (such as automation of business processes) are met, any requirements that are not fully met, and any options or considerations that require a business decision. The provision of comprehensive guidance on the development of, and modifications to, solution components to ensure that they take account of relevant architectures, strategies, policies, standards, and practices (including security) and that existing and planned solution components remain compatible. | 5-6 |
| User experience analysis | The identification, analysis, clarification, and communication of the context of use in which applications will operate, and of the goals of products, systems, or services. Analysis and prioritization of stakeholders' "user experience" needs and definition of required system behavior and performance. Resolution of potential conflicts between user requirements and determination of usability objectives. | 3-5 |
14.2 European Competency Framework
The European Union's European e-Competence Framework (e-CF) has 40 competences and is used by a large number of companies, qualification providers, and others in public and private sectors across the EU. It uses five levels of competence proficiency (e-1 to e-5). No competence is subject to all five levels.
The e-CF is published and legally owned by CEN, the European Committee for Standardization, and its National Member Bodies (www.cen.eu). Its creation and maintenance has been co-financed and politically supported by the European Commission, in particular, DG (Directorate General) Enterprise and Industry, with contributions from the EU ICT multi-stakeholder community, to support competitiveness, innovation, and job creation in European industry. The Commission works on a number of initiatives to boost ICT skills in the workforce. Version 1.0 to 3.0 were published as CEN Workshop Agreements (CWA). The e-CF 3.0 CWA 16234-1 was published as an official European Norm (EN), EN 16234-1. For complete information, see http://www.ecompetences.eu.
| e-CF Dimension 2 | e-CF Dimension 3 |
|---|---|
| A.4. Product/Service Planning (PLAN) Analyzes and defines current and target status. Estimates cost effectiveness, points of risk, opportunities, strengths, and weaknesses, with a critical approach. Creates structured plans; establishes time scales and milestones, ensuring optimization of activities and resources. Manages change requests. Defines delivery quantity and provides an overview of additional documentation requirements. Specifies correct handling of products, including legal issues, in accordance with current regulations. | Level 2-4 |
| A.5. Architectural Design (PLAN) Specifies, refines, updates, and makes available a formal approach to implement solutions necessary to develop and operate the IS architecture. Identifies change requirements and the components involved: hardware, software, applications, processes, information, and technology platform. Takes into account interoperability, scalability, usability, and security. Maintains alignment between business evolution and technology developments. | Level 3-5 |
| A.6. Application Design (PLAN) Analyzes, specifies, updates, and makes available a model to implement applications in accordance with IS policy and user/customer needs. Selects appropriate technical options for application design, optimizing the balance between cost and quality. Designs data structures and builds system structure models according to analysis results through modeling languages. Ensures that all aspects take account of interoperability, usability and security. Identifies a common reference framework to validate the models with representative users, based upon development models (e.g., iterative approach). | Level 1-3 |
| D.10. Information and Knowledge Management (ENABLE) Identifies and manages structured and unstructured information and considers information distribution policies. Creates information structure to enable exploitation and optimization of information. Understands appropriate tools to be deployed to create, extract, maintain, renew, and propagate business knowledge in order to capitalize from the information asset. | Level 3-5 |
| D.11. Needs Identification (ENABLE) Actively listens to internal/external customers, articulates and clarifies their needs. Manages the relationship with all stakeholders to ensure that the solution is in line with business requirements. Proposes different solutions (e.g., make-or-buy) by performing contextual analysis in support of user centered system design. Advises the customer on appropriate solution choices. Acts as an advocate engaging in the implementation or configuration process of the chosen solution. | Level 3-5 |
14.3 i Competency Dictionary
The Information Technology Promotion Agency (IPA) of Japan has developed the i Competency Dictionary (iCD) and translated it into English, and describes it at https://www.ipa.go.jp/english/humandev/icd.html. The iCD is an extensive skills and tasks database, used in Japan and southeast Asian countries. It establishes a taxonomy of tasks and the skills required to perform the tasks. The IPA is also responsible for the Information Technology Engineers Examination (ITEE), which has grown into one of the largest scale national examinations in Japan, with approximately 600,000 applicants each year.
The iCD consists of a Task Dictionary and a Skill Dictionary. Skills for a specific task are identified via a "Task x Skill" table. (See Appendix A for the task layer and skill layer structures.) EITBOK activities in each chapter require several tasks in the Task Dictionary.
The table below shows a sample task from iCD Task Dictionary Layer 2 (with Layer 1 in parentheses) that corresponds to activities in this chapter. It also shows the Layer 2 (Skill Classification), Layer 3 (Skill Item), and Layer 4 (knowledge item from the IPA Body of Knowledge) prerequisite skills associated with the sample task, as identified by the Task x Skill Table of the iCD Skill Dictionary. The complete iCD Task Dictionary (Layer 1-4) and Skill Dictionary (Layer 1-4) can be obtained by returning the request form provided at http://www.ipa.go.jp/english/humandev/icd.html.
| Task Dictionary | Skill Dictionary | ||
|---|---|---|---|
| Task Layer 1 (Task Layer 2) | Skill Classification | Skill Item | Associated Knowledge Items |
| Computerization requirements definition (system requirements definition and architecture design) |
Requirement analysis methods | Requirement extraction methods |
|
15 Key Roles
These roles are common to ITSM:
- Application Developer
- Applications Analyst
- Business Relationship Manager
- Configuration Manager
- Knowledge Manager
- Process Architect
- Process Owner
- Project Manager
- Release Manager
- Service Design Manager
- Supplier Manager
- Technical Analyst
- Test Manager
Other key roles are:
- Business Architect
- Compliance Manager
- Data Architect
- Executive Sponsor
- Governance Body
- Operations Manager
- Security Manager
- User Experience Sponsor
16 Standards
ISO/IEC/IEEE 15288:2015, Systems and software engineering—Systems lifecycle processes
ISO/IEC/IEEE 29148:2011, Systems and software engineering—Lifecycle processes—Requirements engineering
17 References
[1] A. C. Scott, J. Clayton, & E. Gibson, A Practical Guide to Knowledge Acquisition, Addison-Wesley Publishing Company, 1991.
[2] S.A. Bohner and R.S. Arnold, Software Change Impact Analysis, IEEE CS Press, 1996.
[3] Jim Heumann, The Five Levels of Requirements Management Maturity, The Rational Edge, 2003; http://www.ibm.com/developerworks/rational/library/content/RationalEdge/feb03/ManagementMaturity_TheRationalEdge_Feb2003.pdf.
[4] IEEE Guide for Developing System Requirements Specifications, IEEE Std 1233, 1998 Edition; pp. 11-14.
[5] A. Cockburn, Writing Effective Use Cases, Addison Wesley Professional, 2000.
[6] C. Benson, Security Planning, MSDN Library, https://msdn.microsoft.com/en-us/library/cc723503.aspx.
[7] DAMA International, The DAMA Guide to the Data Management Body of Knowledge, Technics Publications, LLC, 2009.
[8] IIBA, A Guide to the Business Analysis Body of Knowledge (BABOK Guide), Version 3.0, 2015.
[9] M. Jackson, Software Requirements and Specifications: A Lexicon of Practice, Principles, and Prejudices (ACM Press), Addison-Wesley Professional, 1995.
[10] K. Wiegers, Requirements Analysis 3 (Developers Best Practices), Microsoft Press, 2003.
[11] D. Leffingwell, Software Requirements: Lean Requirements Practices for Teams, Programs, and the Enterprise, Agile Software Development Series, Addison-Wesley Professional, 2011.
[12] H. Podeswa, The Business Analyst's Handbook, Cengage Learning PTR, 2008.