Difference between revisions of "What is Enterprise IT?"
| Line 1: | Line 1: | ||
<table border="3"> | <table border="3"> | ||
<tr><td> | <tr><td> | ||
| − | + | <table> | |
| − | + | <tr> | |
| − | + | <td width="60%"><font color="#246196">'''Welcome to the initial version of the EITBOK wiki. Like all wikis, it is a work in progress and may contain errors. We welcome feedback, edits, and real-world examples. [[Main_Page#How to Make Comments and Suggestions|Click here]] for instructions about how to send us feedback.''' </font></td> | |
| − | + | <td width="20%">[[File:Ieee logo 1.png|100px|center]]</td> | |
| − | + | <td width="20%"> [[File:Acm_logo_3.png|175px|center]]</td> | |
| − | + | </tr></table> | |
</td></tr></table> | </td></tr></table> | ||
<p> </p> | <p> </p> | ||
| Line 12: | Line 12: | ||
<h1>Enterprise IT and the Business Environment</h1> | <h1>Enterprise IT and the Business Environment</h1> | ||
| − | In this | + | In this BOK, we have adopted the term '''[http://eitbokwiki.org/Glossary#eit enterprise information technology (EIT)]''' to distinguish it from the IT industry at large, which includes companies that produce the technology that enterprise IT (EIT) employs, such as software packages, computers, and routers. Enterprise IT, as used in this guide, refers to IT services provided to (and maintained by) the enterprise by an IT department. Although the principles and standard practices covered in this guide can apply to technology put in place by non-IT personnel in other departments of the enterprise, when they are outside the purview of the IT department, they are not considered enterprise IT. |
| − | The business environment of an enterprise consists of all the internal and external factors that influence the performance and growth of the enterprise. | + | The business environment of an enterprise consists of all the internal and external factors that influence the performance and growth of the enterprise. The external factors include macro- and microeconomics, social trends, politics, technology, and others, and any of these factors can potentially help or harm the enterprise. The internal factors include things such as the enterprise’s objectives and goals, policies, methods, organizational structure, and management style, among others. |
| − | One of the internal factors is the capability and structure of the enterprise’s information technology function. | + | One of the internal factors is the capability and structure of the enterprise’s information technology function. What is interesting about this factor is that it is inextricably related to all the factors. In fact, successful EIT must take into account all the other functions’ directives, policies, goals, and constraints as inputs to its organizational and service design. All relevant environment factors need to be investigated, thoroughly understood, and documented so that they can be fully considered during the design of IT services. An added challenge is that these factors change—some frequently—which requires near constant reinvestigation of the business environment. To do its job right, EIT needs to have visibility into the enterprise’s understanding of all its business factors. |
| − | In many organizations, EIT has become a key functional area through which enterprises | + | In many organizations, EIT has become a key functional area through which enterprises design new business processes and develop specialized organizational capabilities. These new processes and capabilities are not generated in isolation. Instead, EIT needs to be fully integrated with all departments where their solutions will have an effect. In today’s environment, that is typically the entire enterprise. In general, EIT provides the scaffolding over which business processes run, from one department to another. A good example of this is the order management process, which runs from the sales department taking an order, through billing and inventory management, to eventual delivery to the customer. |
<h1>Defining Enterprise Information Technology</h1> | <h1>Defining Enterprise Information Technology</h1> | ||
| − | Enterprise IT (EIT) is made up of the people, processes, data, and technologies that support the enterprise. Enterprises collect data, analyze it, and then run their functions based upon information gathered or deduced. In essence, data flows through nearly all business processes to enable the organization to make decisions and take actions. Information technology enables the speedy flow of data through an enterprise. | + | Enterprise IT (EIT) is made up of the people, processes, data, and technologies that support the enterprise. Enterprises collect data, analyze it, and then run their functions based upon information gathered or deduced. In essence, data flows through nearly all business processes to enable the organization to make decisions and take actions. Information technology enables the speedy flow of data through an enterprise. It also provides tools for data input, analysis, and sharing. |
[[File:Processes-technology-people.jpg]]<br /> | [[File:Processes-technology-people.jpg]]<br /> | ||
| − | '''Figure 1 | + | '''Figure 1. IT processes, data, technologies, and people support the enterprise''' |
| − | <p>More explicitly, EIT supports the data needs of the | + | <p>More explicitly, EIT supports the data needs of the enterprise by:</p> |
<ul> | <ul> | ||
<li>Seeking to understand the business’s workings and needs for automation</li> | <li>Seeking to understand the business’s workings and needs for automation</li> | ||
| Line 35: | Line 35: | ||
</ul> | </ul> | ||
| − | <p>EIT professionals accomplish these things by building on existing national and international | + | <p>EIT professionals accomplish these things by building on existing national and international standards and frameworks (for building or acquiring and integrating technologies) and by relying on the knowledge of experts who develop guides to the specialized bodies of knowledge. Figure 2 reflects how standardized professional knowledge is used as a basis to provide secure, interoperable, and high-quality information technology to the enterprise. </P> |
[[File:EIT_tree.png]]<br /> | [[File:EIT_tree.png]]<br /> | ||
| − | '''Figure 2 | + | '''Figure 2. The enterprise ITG organization’s world''' |
| − | + | EIT is often described through a layered hierarchical architectural model (originally defined by the National Institute of Standards and Technology), which links the enterprise to the delivery of its products and services (shown in Figure 3). The original late 1980s NIST model provides an early view of defining enterprise IT via a layered hierarchical architectural model that links the business to the delivery of products and services. The layered views have retained their resiliency, although they are now generally represented as a BIAT model: Business, Information, Architecture, and Technology, as discussed in subsequent chapters of this guide. | |
| − | EIT is often described through a layered | + | |
[[File:EIT-Layered-Architecture.jpg]]<br /> | [[File:EIT-Layered-Architecture.jpg]]<br /> | ||
| − | '''Figure 3 | + | '''Figure 3. Enterprise IT hierarchy architectural model''' |
| − | At the business | + | At the '''business architecture''' layer, IT business strategy alignment, business case analysis, projected return on investments, prioritization, and resource allocation decisions are addressed. The results of these activities drive the development of the information architecture. |
| − | The information | + | The '''information architecture''' layer is where the information needed to support the business is defined and likely sources for the information are identified. The output of the information architecture provides the requirements for the information systems architecture. |
| − | The software application architecture layer defines the business applications that offer information services to business functions and to each other. The output of information systems architecture feeds the data architecture. | + | The '''software application architecture''' layer defines the business applications that offer information services to business functions and to each other. The output of information systems architecture feeds the data architecture. |
| − | + | ||
| − | + | The '''data architecture''' is composed of enterprise models, policies, rules and standards that govern which data is collected, and how it is stored, arranged, integrated, kept secure and put to use. | |
| − | At each level of the EIT architecture, people, processes, data, and technology are interrelated. Although this is a layered architectural model of EIT, it should be noted that iteration between the layers and regression among the layers occurs depending on the needs of the organization. | + | Data flow is supported by the delivery '''systems architecture''', which is composed of hardware, networks, and platform applications that offer platform services to each other and to business applications. |
| + | |||
| + | At each level of the EIT architecture, people, processes, data, and technology are interrelated. Although this is a layered architectural model of EIT, it should be noted that iteration between the layers and regression among the layers occurs depending on the needs of the organization. Also, the model permits external inputs, such as advancements in technologies, changes in business directions, regulatory changes, and other demands on the business. | ||
<h1>Evolution of the Role of EIT</h1> | <h1>Evolution of the Role of EIT</h1> | ||
| − | + | ||
<h2>EIT Eras</h2> | <h2>EIT Eras</h2> | ||
| − | The history of IT can be divided into four hardware-related eras: mainframes, personal computers (PCs), networks, and the World Wide Web. | + | The history of IT can be divided into four hardware-related eras: mainframes, personal computers (PCs), networks, and the World Wide Web. The computer industry was born with the first giant calculators—mainframes that digitally processed and manipulated numbers for specific purposes. EIT became a reality when general-purpose mainframes became commercially available and started to take on transaction-oriented activities within organizations, such as back-office accounting functions and airline reservations. Until the 1980s, most computer-related activities revolved around interactions between a specialist computer operator and a computer in a “glass house” to which ordinary workers weren’t allowed access. Enterprise IT was made possible through teams of in-house programmers who wrote the software needed to automate jobs within the enterprise. |
| − | When the first PCs arrived on the scene, they were simply a single-user, mini-mainframe that anybody could use. Of course, PCs unleashed a stream of shrink-wrapped, personal-productivity applications that contributed greatly to the growth of enterprise software and data. The role of IT at this point was to ensure that applications were available for the users that needed them to execute the specialized processes associated with their jobs. That, of course, then entailed trouble-shooting application | + | When the first PCs arrived on the scene, they were simply a single-user, mini-mainframe that anybody could use. Of course, PCs unleashed a stream of shrink-wrapped, personal-productivity applications that contributed greatly to the growth of enterprise software and data. The role of IT at this point was to ensure that applications were available for the users that needed them to execute the specialized processes associated with their jobs. That, of course, then entailed trouble-shooting application and desktop problems for end users, and the era of desktop support was launched. |
| − | The role of IT took a major quantitative and qualitative leap when PCs became connected to each | + | The role of IT took a major quantitative and qualitative leap when PCs became connected to each other—first through local area networks (LANs) and then across long-distances via wide area networks (WANs). Computer networks (and applications like email) enabled many process to become entirely digital, ensuring the proliferation of information, as well as drastically increasing the amount of data created, stored, moved, and consumed. |
| − | Connecting people in a vast and distributed network of computers not only increased the amount of data generated, but also led to new ways of getting value out of data through many new enterprise applications. It also created a new passion for “data mining.” In essence, networks changed the focus of IT from backroom operations to managing the integration of business processes for the enterprise. | + | Connecting people in a vast and distributed network of computers not only increased the amount of data generated, but also led to new ways of getting value out of data through many new enterprise applications. It also created a new passion for “data mining.” In essence, networks changed the focus of IT from backroom operations to managing the integration of business processes for the enterprise. This change increased the role of the Chief Information Office to include management of the networks and the associated methods, processes, and technologies. The enterprise began to regard the IT role not as a specific function responsible for running the computer infrastructure, but as the core of their business. |
| − | The next phase of the EIT function came with the invention of the World Wide Web. | + | The next phase of the EIT function came with the invention of the World Wide Web. While networks expanded IT into all corners of the enterprise, the World Wide Web expanded IT to all corners of the globe. |
| − | The introduction of the Web has led to the proliferation of new applications that are not limited to enterprise-related | + | The introduction of the Web has led to the proliferation of new applications that are not limited to enterprise-related activities—they can be dynamically linked via enterprise networks to strategic partners and supply chains. The Web has provided individual users within an enterprise with tools and applications that greatly facilitate the creation and sharing of information with other business enterprise partners connected to the World Wide Web. With the introduction of web access to ever widening sources of data, EIT has become responsible for ever-larger data lakes and data pools. Data and its analysis has become even more of a competitive edge and given rise to a demand for “data scientists” within the enterprise, often in EIT itself. |
<h2>The Evolution of EIT Structure</h2> | <h2>The Evolution of EIT Structure</h2> | ||
| − | With the changing roles of EIT, the structure of the EIT department has had to change, as well. In the back-office, mainframe era, the IT organization structure was relatively simple, supporting back-office functions. | + | With the changing roles of EIT, the structure of the EIT department has had to change, as well. In the back-office, mainframe era, the IT organization structure was relatively simple, supporting back-office functions. There was an IT Director (who typically reported to a Chief Financial Officer), a manager of mainframe operations and computer operators—people who operated and maintained the hardware, and ran the jobs requested by specialized users, usually computer programmers. As time went on, a programming department grew to create and enhance critical back-office applications. So, there was a simple structure: an operations group that kept the hardware running and ran requested jobs on the mainframe and its output devices, and a simple programming services group that interfaced with the end users who needed the services of the mainframe. This was really the start of the development role of the IT organization. Users could request features and the IT department would run development projects that would add those features. |
| − | When PCs were added to the mix, the organization often added a new division specifically for desktop | + | When PCs were added to the mix, the organization often added a new division specifically for desktop support—the care and feeding of the PCs and their users. These new functions required an entirely different set of skills, which put significant demands on the EIT department to modify how they supported their user community. Not only did the IT department need to understand PC hardware, but also the software that was now available to users. In addition, users started to become much more savvy of their computing hardware. In some situations, the user community knew more about their computing equipment and applications than the EIT staff, which caused significant conflicts about who was in control of the software and hardware—the users or EIT. |
| − | Before shrink-wrapped applications were available, it was | + | Before shrink-wrapped applications were available, it was EIT’s responsibility to support the users with customized productivity applications. Thus, the Development group had to become proficient in new areas. |
The institution of the network and shared data added two new departments to the IT structure: network management as well as database development and management. By this point, EIT departments had transitioned into critical service providers. Enhancements and innovations to the services and functions that they provided were critical to the health of the organization. More and more, EIT departments started to become the nerve center of the enterprise; they transitioned into being EIT departments, and IT Directors became Chief Information Officers or Chief Technology Officers. | The institution of the network and shared data added two new departments to the IT structure: network management as well as database development and management. By this point, EIT departments had transitioned into critical service providers. Enhancements and innovations to the services and functions that they provided were critical to the health of the organization. More and more, EIT departments started to become the nerve center of the enterprise; they transitioned into being EIT departments, and IT Directors became Chief Information Officers or Chief Technology Officers. | ||
| Line 84: | Line 84: | ||
Once the Web entered the picture, even more aspects became critical, such as EIT security and open technology architectures. In addition, the proliferation of “outside” applications and functions require that EIT departments develop and enforce EIT processes and procedures for the entire enterprise. | Once the Web entered the picture, even more aspects became critical, such as EIT security and open technology architectures. In addition, the proliferation of “outside” applications and functions require that EIT departments develop and enforce EIT processes and procedures for the entire enterprise. | ||
| − | In sum, EIT is the custodian of the massive investment in | + | In sum, EIT is the custodian of the massive investment in assets—the corporate information and the corporate technology to derive value from it. EIT has a responsibility (and accountability) to protect the confidentiality, integrity, and availability of that asset. Given that responsibility, it must also have the resources and the authority to carry it out. |
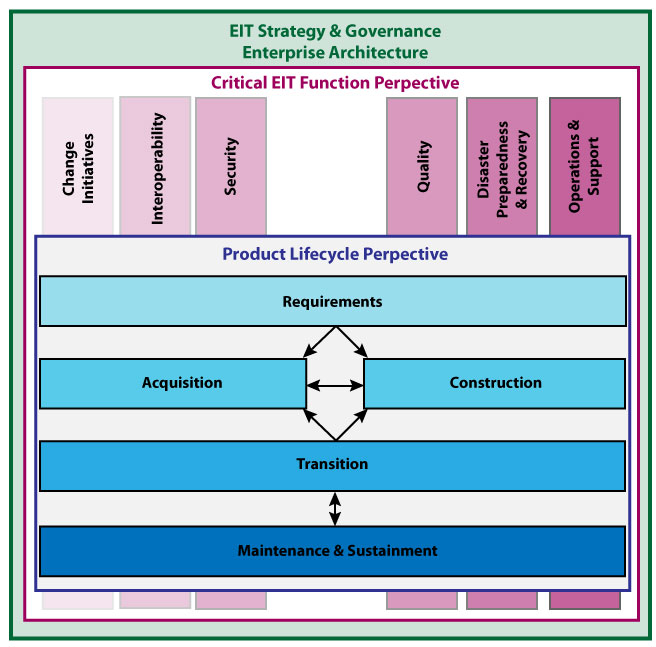
| − | What does the structure of today’s EIT department look like? That depends on the organization’s functions and needs for information technology. | + | What does the structure of today’s EIT department look like? That depends on the organization’s functions and needs for information technology. In addition, for any evolving organization, EIT’s structure also needs to evolve. Here is a simplistic view of the core EIT functions. |
[[File:LifeCycle-vs-Function_v3.jpg]]<br /> | [[File:LifeCycle-vs-Function_v3.jpg]]<br /> | ||
| − | '''Figure 4 | + | '''Figure 4. Core EIT functions''' |
<h3>Shadow IT Groups</h3> | <h3>Shadow IT Groups</h3> | ||
| − | Shadow IT is a term often used to describe information-technology systems and solutions built and used inside an enterprise without explicit IT approval. It is also used, along with the term | + | Shadow IT is a term often used to describe information-technology systems and solutions built and used inside an enterprise without explicit IT approval. It is also used, along with the term stealth IT, to describe solutions specified and deployed by departments other than the IT department. Lately, the term dark IT has cropped up. There are several good blogs about the problems that can arise from these other modes of IT, such as http://www.itskeptic.org/content/dark-it and http://bobmartens.net/2014/09/dark-it/. |
| − | Shadow IT is considered by many as an important source for innovation, and such systems can turn out to be important prototypes for future approved EIT solutions. On the other hand, shadow IT solutions can expose the enterprise to high levels of risk, since they are not often in line with the | + | Shadow IT is considered by many as an important source for innovation, and such systems can turn out to be important prototypes for future approved EIT solutions. On the other hand, shadow IT solutions can expose the enterprise to high levels of risk, since they are not often in line with the enterprise’s requirements for appropriate governance, security, and reliability, although these issues can apply equally to authorized EIT solutions. |
| − | Unofficial data flows that don’t go through EIT can be as simple as USB sticks or other portable data storage devices, online messaging software, | + | Unofficial data flows that don’t go through EIT can be as simple as USB sticks or other portable data storage devices, online messaging software, email services, Google Docs, or other web-based collaboration tools. The challenges with shadow IT solutions are: |
<ul> | <ul> | ||
| − | <li>Non-compliance with governmental or industrial standards (e.g. COBIT, GAAP, HIPAA, ITIL, Sarbanes-Oxley)</li> | + | <li>Non-compliance with governmental or industrial standards (e.g., COBIT, GAAP, HIPAA, ITIL, Sarbanes-Oxley)</li> |
<li>Duplication of effort resulting in wasted resources</li> | <li>Duplication of effort resulting in wasted resources</li> | ||
<li>Inconsistent business logic</li> | <li>Inconsistent business logic</li> | ||
<li>Higher risk of unauthorized intrusion, as well as data destruction, corruption, and leaks</li> | <li>Higher risk of unauthorized intrusion, as well as data destruction, corruption, and leaks</li> | ||
<li>Security risks when data or applications are moved outside protected systems, networks, physical location, or security domains</li> | <li>Security risks when data or applications are moved outside protected systems, networks, physical location, or security domains</li> | ||
| − | <li>Lack of adequate user support when problems are encountered</li> | + | <li>Lack of adequate user support when problems are encountered</li></ul> |
<h3>Cost Center Versus Profit Center</h3> | <h3>Cost Center Versus Profit Center</h3> | ||
| − | EIT organizations service other organizations within the enterprise. | + | EIT organizations service other organizations within the enterprise. In the traditional view, they don’t generate revenue, and as a result are considered cost centers. This point of view has EIT as a cost burden in the organization, and it typically leads to demands from management to cut costs. |
| − | With the advent of better integration into the overall work of the enterprise and better portfolio management, EIT contributions have become more visible and more appreciated. EIT departments have put more resources into innovation, thus increasing their contributions to the bottom line. They also have worked to cut costs, of course, attempting to decrease the cost of maintaining existing solutions by better portfolio management, outsourcing maintenance activities, and using cloud computing; however, it is unclear whether | + | With the advent of better integration into the overall work of the enterprise and better portfolio management, EIT contributions have become more visible and more appreciated. EIT departments have put more resources into innovation, thus increasing their contributions to the bottom line. They also have worked to cut costs, of course, attempting to decrease the cost of maintaining existing solutions by better portfolio management, outsourcing maintenance activities, and using cloud computing; however, it is unclear whether these techniques are really decreasing costs in the long run. |
| − | Many people believe that EIT should be treated as a profit center. Note that EIT is often closely associated with profit centers, and the profit centers would not be functional without EIT’s efforts. | + | Many people believe that EIT should be treated as a profit center. Note that EIT is often closely associated with profit centers, and the profit centers would not be functional without EIT’s efforts. For example, Amazon can’t really differentiate between its EIT function and its ability to make sales. |
<h2>The Evolution of EIT Management Roles</h2> | <h2>The Evolution of EIT Management Roles</h2> | ||
| − | The traditional head of the EIT department is the Chief Information Officer (CIO). | + | The traditional head of the EIT department is the Chief Information Officer (CIO). This individual serves as the organization’s top information technology manager. The CIO runs the internal IT operations, and ensures that the organization’s IT infrastructure is in alignment with the business goals and needs. The CIO’s job is to be focused on satisfying internal customers, both users and business units, yet keep the cost of serving those customers at a reasonable level. |
<h3>CIO Versus CTO and CMO</h3> | <h3>CIO Versus CTO and CMO</h3> | ||
| − | The Chief Information Officer, Chief Technology Officer, and the Chief Marketing Officer typically report to the CEO. | + | The Chief Information Officer, Chief Technology Officer, and the Chief Marketing Officer typically report to the CEO. Their functions are different, but sometimes overlapping. |
| − | The '''Chief Technology Officer''' (CTO) is the chief technology visionary for the enterprise. This is a technology focused position. In a non-technical enterprise, the CTO usually reports to the CIO and is primarily concerned with long-term and over-arching technical issues, especially architectures. In technology focused organizations, CIO and CTO can be at the same level with the CIO focused on the information technology that runs the enterprise and the CTO focused on the company’s core product technology and other supporting technologies. | + | The '''Chief Technology Officer''' (CTO) is the chief technology visionary for the enterprise. This is a technology-focused position. In a non-technical enterprise, the CTO usually reports to the CIO and is primarily concerned with long-term and over-arching technical issues, especially architectures. In technology-focused organizations, CIO and CTO can be at the same level with the CIO focused on the information technology that runs the enterprise and the CTO focused on the company’s core product technology and other supporting technologies. |
The '''Chief Marketing Officer''' (CMO) is responsible for overseeing marketing initiatives within the organization. Even though this job’s main goal is to develop sales management, product development, distribution channel management, and customer service, the CMO’s job often bumps up against the CIO’s and CTO’s jobs in the area of marketing communications, especially in the areas of web advertising and social engineering. | The '''Chief Marketing Officer''' (CMO) is responsible for overseeing marketing initiatives within the organization. Even though this job’s main goal is to develop sales management, product development, distribution channel management, and customer service, the CMO’s job often bumps up against the CIO’s and CTO’s jobs in the area of marketing communications, especially in the areas of web advertising and social engineering. | ||
| Line 130: | Line 130: | ||
As EIT has become more diverse and more sophisticated, new roles have emerged, in addition to the classic roles of development and operations management. | As EIT has become more diverse and more sophisticated, new roles have emerged, in addition to the classic roles of development and operations management. | ||
| − | The '''Chief Enterprise Architect''' focuses on business modeling, processes, and integration. | + | The '''Chief Enterprise Architect''' (CEA) focuses on business modeling, processes, and integration. The CEA translates the business vision into effective enterprise change. The CEA works on creating technology and business process changes within the boundary of the business. |
| − | The '''Chief Data Officer''' | + | The '''Chief Data Officer''' (CDO) focuses on information, how data assets can be turned into useful and timely information, its accuracy, and the policies needed to protect it for its intended use. |
| − | The '''Chief Digital Officer''' has an external customer interaction focus, and works to improve the value of interactions with user and customers. | + | The '''Chief Digital Officer''' (CDO) has an external customer interaction focus, and works to improve the value of interactions with user and customers. |
| − | The '''Chief Web Officer''' | + | The responsibilities of the '''Chief Web Officer''' (CWO) vary among enterprises, depending on the needs and goals of the business. A CWO should have a deep and broad understanding of the Web and website governance issues including online strategy, systems and software administration, web hosting, e-commerce, online community and social media, web content development and workflows, website graphic design, user experience (analysis/design), website analytics, and security, among others. |
| − | Note that | + | Note that in many organizations, especially smaller ones, one person may carry out several of the above responsibilities. |
<h2>Evolving EIT Standards</h2> | <h2>Evolving EIT Standards</h2> | ||
| − | <div style="margin-left: 5em;"><em> | + | <div style="margin-left: 5em;"><em>“The world is getting smaller on a daily basis. Hardware, software, and content move independent of, and irrespective of, international boundaries. As that increasingly happens, the need to have commonality and interoperability grows. We need standards so that the movie made in China or India plays in the equipment delivered in the United States, or the Web site in the United States plays on the computer in China.”</em> <br />~ Craig Barrett, former Intel CEO</div> |
| − | of, and irrespective of, international boundaries. As that increasingly happens, the need to have commonality and interoperability grows. We need standards so that the movie made in China or India plays in the equipment delivered in the United States, or the Web site in the United States plays on the computer in China.”</em> | + | |
| − | Over time, technical standards have emerged as the industry has demanded common interfaces and common protocols, as well as standard reference models. One well known evolutionary path is that of proprietary standards for manual and electronic communication within the enterprise (e.g., mainframe) in the 1970s; emerging standards for intra-enterprise technology and communication (e.g., TCP/IP, Client Server) in the 1980s and open standards based on common technology and communications protocols (e.g., XML, Linux , JBOSS) in the 1990s and 2000s. Companies use standards associated with their | + | Over time, technical standards have emerged as the industry has demanded common interfaces and common protocols, as well as standard reference models. One well-known evolutionary path is that of proprietary standards for manual and electronic communication within the enterprise (e.g., mainframe) in the 1970s; emerging standards for intra-enterprise technology and communication (e.g., TCP/IP, Client Server) in the 1980s; and open standards based on common technology and communications protocols (e.g., XML, Linux , JBOSS) in the 1990s and 2000s. Companies use standards associated with their infrastructure service provider (ISP) and application service provider (ASP) approaches. These technical standards, whether created by formal standards developing organizations (SDOs) like the IEEE and ISO, or by industry consortia like the Open Group, are needed by the EIT community across the world, so that each EIT organization does not have to reinvent the wheel and reinvent ways to communicate each time a new relationship is created. Thus, they promote the flow of electronic data and knowledge in a global economy. For example, in a global EIT community: |
<ul> | <ul> | ||
| − | <li> | + | <li>Each morning, companies receive software that was written in India overnight in time to be tested in their country and returned to India for further production that same evening—making the 24-hour workday a practicality.</li> |
| − | + | <li>Back-offices of firms operate in such places as Costa Rica, Ireland, and Switzerland.</li> | |
| − | <li>Back-offices of firms operate in such places as Costa Rica, Ireland and Switzerland.</li> | + | |
| − | + | ||
<li>Drawings for architectural firms are produced in Brazil. </li> | <li>Drawings for architectural firms are produced in Brazil. </li> | ||
| − | + | <li>Call centers are based in India, where employees are now being taught to speak with client based accents.</li> | |
| − | <li>Call centers are based in | + | |
| − | + | ||
<li>Hospitals have x-rays and CAT scans read by radiologists in Australia and India.</li> | <li>Hospitals have x-rays and CAT scans read by radiologists in Australia and India.</li> | ||
| − | |||
<li>At some McDonald’s drive-in windows orders are transmitted to a processing center a thousand miles away (currently in the U.S.), where they are processed and returned to the worker who actually prepares the order.</li> | <li>At some McDonald’s drive-in windows orders are transmitted to a processing center a thousand miles away (currently in the U.S.), where they are processed and returned to the worker who actually prepares the order.</li> | ||
| − | |||
<li>Accounting firms have client’s tax returns prepared by experts in India.</li> | <li>Accounting firms have client’s tax returns prepared by experts in India.</li> | ||
| − | + | <li>Visitors to an office not far from the White House are greeted on a flat screen display by a receptionist who controls access to the building and arranges contacts; the person behind the flat screen is in Pakistan.</li> | |
| − | <li>Visitors to an office not far from the White House are greeted | + | <li>Surgeons sit on the opposite side of the operating room and control robots that perform the procedures. It is not a huge leap of imagination to have highly specialized, world-class surgeons located not just across the operating room but geographically separated by large distances.</li> |
| − | + | ||
| − | <li>Surgeons sit on the opposite side of the operating room and control robots | + | |
</ul> | </ul> | ||
| Line 170: | Line 161: | ||
<div style="margin-left: 5em;"> | <div style="margin-left: 5em;"> | ||
| − | <em> | + | <em>“Methods for developing and delivering EIT systems, especially software systems, have evolved ever since the ‘Software Crisis’ of the 1960s. The major cause of the software crisis is that the machines have become several orders of magnitude more powerful! To put it quite bluntly: as long as there were no machines, programming was no problem at all; when we had a few weak computers, programming became a mild problem, and now we have gigantic computers, programming has become an equally gigantic problem.”</em> <br />~ Edsger Dijkstra, The Humble Programmer (EWD340)</div> |
| − | And now that we thousands of interlinked computers, both programming and the development of the technology infrastructure that the software runs on have become exponentially more complex. Thus, we have seen the need for standards | + | And now that we have thousands of interlinked computers, both programming and the development of the technology infrastructure that the software runs on have become exponentially more complex. Thus, we have seen an increase in the need for standards, reference models, and frameworks. At the same time, professionals have sought more effective ways to build systems to meet expectations of budget and capabilities. |
Djikstra put forth one of the earliest codifications of practice in his proposals for structured programming. He campaigned for more discipline in programming, and pointed out that software productivity was closely related to rigor in design. | Djikstra put forth one of the earliest codifications of practice in his proposals for structured programming. He campaigned for more discipline in programming, and pointed out that software productivity was closely related to rigor in design. | ||
| − | As IBM and other systems integrators became widely used by EIT organizations to build internal systems for them, EIT practitioners learned the contractors’ methods for completing contracts on time and budget. These methods were also adopted by various government agencies in order to control their expenses in having technology outsourced. Essentially, these were project management processes that provided for distinct approval points in the development of the technology: requirements sign-off, design sign-off, etc. Theoretically, once each “stage” was approved, the project was on-track. | + | As IBM and other systems integrators became widely used by EIT organizations to build internal systems for them, EIT practitioners learned the contractors’ methods for completing contracts on time and budget. These methods were also adopted by various government agencies in order to control their expenses in having technology outsourced. Essentially, these were project management processes that provided for distinct approval points in the development of the technology: requirements sign-off, design sign-off, etc. Theoretically, once each “stage” was approved, the project was on-track. This approach has popularly been called the Waterfall Method. Many systems integrators packaged their project management processes as methodologies, with brands like Navigator, and sold them to their EIT clients. |
| − | Software product companies, on the other hand, arose quickly in the 1970s and 1980s, and rejected the systems integrators’ approach as too cumbersome. | + | Software product companies, on the other hand, arose quickly in the 1970s and 1980s, and rejected the systems integrators’ approach as too cumbersome. One of the most important things they instituted was the concept of the product management team, wherein each stakeholder in the product had a place at the table where decisions were made. These teams included the product manger, the development manger, the test manager, the documentation manager, and customer support manager, at a minimum. |
| − | Since then, many different approaches have had their day, such as Rapid Application Development in the 1990s and, since then, various “agile” approaches (Scrum, DSDM, | + | Since then, many different approaches have had their day, such as Rapid Application Development in the 1990s and, since then, various “agile” approaches (Scrum, DSDM, feature-driven development, test-driven development, etc.). |
| − | DevOps goes a step further than previous EIT approaches, and is somewhat akin to the use of | + | DevOps goes a step further than previous EIT approaches, and is somewhat akin to the use of product teams in software product companies, in that it takes into account the need for discipline in the transition of new EIT capabilities from development (or acquisition) to the operations arm of EIT. |
| − | DevOps is the practice of operations and development engineers participating together in the entire service lifecycle, from design through the development process to production support, most notably characterized by operations staff making use many of the same techniques as developers for their systems work. DevOps brings discipline to the process of delivering capabilities by using continuous integration and continuous deployment, and rigorous | + | DevOps is the practice of operations and development engineers participating together in the entire service lifecycle, from design through the development process to production support, most notably characterized by operations staff making use of many of the same techniques as developers for their systems work. DevOps brings discipline to the process of delivering capabilities by using continuous integration and continuous deployment, and rigorous configuration management, along with dependence on metrics and monitoring schemes. |
Still, the twin plagues underlying the software crisis of the 1960s bedevil us today. | Still, the twin plagues underlying the software crisis of the 1960s bedevil us today. | ||
| Line 190: | Line 181: | ||
<h1>Current Trends in the Enterprise IT Landscape</h1> | <h1>Current Trends in the Enterprise IT Landscape</h1> | ||
| − | <div style="margin-left: 5em;"><em> | + | <div style="margin-left: 5em;"><em>“We are now in the steep part of the exponential trajectory of information technologies in a broad variety of business fields.”</em> <br />~ Raymond Kurzweil, Google</div> |
| − | It is these accelerating information technologies that can instigate major innovations | + | It is these accelerating information technologies that can instigate major innovations in enterprises, ranging from energy and the environment, to health systems and telecommunications. With this strong focus on information technology, the planet seems to getting smaller, flatter, and smarter every day. New businesses and business models have come into existence and old ones are dying at a tremendous speed. The exponential increase in both intelligence and information in consumer devices is incredible. Now cars, kitchen appliances, electrical systems, traffic systems, and even clothing contain sophisticated computational devices, many or most of which plug into “the grid.” This trend has greatly changed not only our lives, but the nature of EIT. |
| − | There are a number of current technology trends that are driving the EIT business environment. | + | There are a number of current technology trends that are driving the EIT business environment. Businesses are working hard to gain or maintain a leadership role in these areas; however, being on the leading edge often means being on the bleeding edge. The challenges are significant and often painful. We discuss a few of those trends here. |
<h2>Big Data and Predictive Analytics</h2> | <h2>Big Data and Predictive Analytics</h2> | ||
| − | Early in the age of data collection, enterprises viewed collecting data as a way to support their enterprise applications for customer relationship management (CRM) and | + | Early in the age of data collection, enterprises viewed collecting data as a way to support their enterprise applications for customer relationship management (CRM) and enterprise resource planning (ERP) as well as manufacturing. But more recently, the trend has been to collect nearly all the information that they can about their users (characteristics, preferences, and actions), their own processes (building and plant performance), and business trends, among other things. Most businesses these days collect huge amounts of disparate and unstructured data, and the data being collected goes well beyond what they need to serve their customers and operate standard business functions. Instead, huge amounts of data are grabbed in the hope of predicting the future. |
Leading enterprises are not putting effort into understanding the data that they have collected just to help them drive key business decisions. Data collection and analysis is now a critical part of business intelligence and the enterprise’s ability to predict the future; however, many feel that careful analysis of often disparate datasets can also aide enterprises in optimizing their predictive analytics capabilities across the enterprise. Key challenge areas for current EIT functions to support the data analysis needs of the enterprise are: | Leading enterprises are not putting effort into understanding the data that they have collected just to help them drive key business decisions. Data collection and analysis is now a critical part of business intelligence and the enterprise’s ability to predict the future; however, many feel that careful analysis of often disparate datasets can also aide enterprises in optimizing their predictive analytics capabilities across the enterprise. Key challenge areas for current EIT functions to support the data analysis needs of the enterprise are: | ||
<ul> | <ul> | ||
| − | <li>Providing advanced analytics to support definition, growth and nurturing of commercial services</li> | + | <li>Providing advanced analytics to support definition, growth, and nurturing of commercial services.</li> |
| − | <li>Leveraging data to enhance customer relationship management (CRM)</li> | + | <li>Leveraging data to enhance customer relationship management (CRM).</li> |
| − | <li>Enabling predictive analytics from large disparate data sources to improve effectiveness (such as predicting or anticipating customer behavior, plant monitoring, planning plant equipment upgrades, diagnosing customer equipment issues)</li></ul> | + | <li>Enabling predictive analytics from large disparate data sources to improve effectiveness (such as predicting or anticipating customer behavior, plant monitoring, planning plant equipment upgrades, and diagnosing customer equipment issues).</li></ul> |
<h2>Social Platforms</h2> | <h2>Social Platforms</h2> | ||
| − | Due to the evolution of social media and social platforms, static company websites are often not necessarily the first or most effective way to engage customers. This change has required that organizations rethink their online marketing (and data collection) strategies. | + | Due to the evolution of social media and social platforms, static company websites are often not necessarily the first or most effective way to engage customers. This change has required that organizations rethink their online marketing (and data collection) strategies. Social media and platforms have given enterprises new opportunities to attract customers, but this requires that EIT learn new skills to match the media. For example, the social identities of individuals, which are often based on a rich history of information about the individual and their activities, have become much more valuable than the isolated information obtained when an individual visits or even registers on an enterprise’s website. Key social media/platform challenges for current EIT professionals include: |
<ul> | <ul> | ||
| − | <li>Dealing with multiple and ever growing sources and amounts of data that often are not directly correlated with each other or with the enterprise’s business</li> | + | <li>Dealing with multiple and ever-growing sources and amounts of data that often are not directly correlated with each other or with the enterprise’s business.</li> |
| − | <li>Effectively working with both unstructured (such as data from social networking, email, chats) and other organizations’ structured data (such as database formats and attributes)</li> | + | <li>Effectively working with both unstructured data (such as data from social networking, email, chats) and other organizations’ structured data (such as database formats and attributes).</li> |
</ul> | </ul> | ||
<h2>Cyber Security and Data Privacy</h2> | <h2>Cyber Security and Data Privacy</h2> | ||
| − | The fortress mentality, in which all EIT has to be architected to be shut off from the world is no longer viable. | + | The fortress mentality, in which all EIT has to be architected to be shut off from the world, is no longer viable. Instead, enterprises need to develop a security architecture that responds appropriately to threats when and where they happen. Automated capabilities that detect, assess, and respond immediately are a focus for most organizations. However, organizations need to put significant effort into identifying the necessary and appropriate security designs, quality and performance attributes, and appropriate risk/cost tradeoffs that drive how security is positioned within the organization, and how it relates to the overall system/EIT architecture. |
| − | In addition, individual privacy and protection of data has been taking center | + | In addition, individual privacy and protection of data has been taking center stage—especially in Europe—as a result of increased government regulation, policy enforcement, and public outcry about the increasing number of data breaches. Leading enterprises, public and private, governmental and commercial, are developing a better understanding about the distinctions between being a data processor (i.e., broadly handling the personal data of others) versus a data controller. Key challenges for the EIT environment are: |
<ul> | <ul> | ||
<li>Figuring out how to better protect</li> | <li>Figuring out how to better protect</li> | ||
| − | + | <ul> | |
| − | + | <li>Enterprise technology assets (e.g., networks, applications, and databases)</li> | |
| − | + | <li>Customer information</li> | |
| − | + | <li>Employee information</li> | |
| − | + | <li>EIT’s services from operational disruption</li> | |
| − | + | <li>EIT’s community and work against terrorism and external attack</li> | |
| − | + | </ul> | |
| − | <li>Figuring out how to comply with government and industry regulations, such as | + | <li>Figuring out how to comply with government and industry regulations, such as payment card industry (PCI) and HIPAA requirements.</li> |
</ul> | </ul> | ||
<h3>Cloud Services and Service Oriented Architectures (SOA)</h3> | <h3>Cloud Services and Service Oriented Architectures (SOA)</h3> | ||
| − | Cloud computing has evolved to a point where the term itself has become nearly superfluous. Hybrid | + | Cloud computing has evolved to a point where the term itself has become nearly superfluous. Hybrid clouds—software-as-a-service (SaaS) and platform-as-a-service (PaaS), in combination with internal applications—are cementing EIT’s role as a driver of business growth. The cloud-computing focus is shifting from providing simple infrastructure solutions to developing cloud strategies that deliver increased functionality and flexibility, whie maintaining security and reliability. These strategies use a mix of public and private cloud-based applications and platform services. While many challenges remain, cloud technologies are nonetheless poised to change the face of enterprise computing. Key challenges for the current EIT organization are: |
<ul> | <ul> | ||
| − | <li>Leveraging repeatable (SOA) technologies across platforms (e.g. web, mobile devices, customer support and self-service)</li> | + | <li>Leveraging repeatable (SOA) technologies across platforms (e.g., web, mobile devices, customer support, and self-service).</li> |
| − | <li>Combining and leveraging internal/private and external/public cloud computing</li> | + | <li>Combining and leveraging internal/private and external/public cloud computing.</li> |
| − | <li>Using cloud services to leverage new and existing data</li> | + | <li>Using cloud services to leverage new and existing data.</li> |
<li>Decreasing time and costs to market and support enterprise needs via:</li> | <li>Decreasing time and costs to market and support enterprise needs via:</li> | ||
| − | + | <ul> | |
<li>Increasing flexibility of platforms</li> | <li>Increasing flexibility of platforms</li> | ||
<li>Increasing operational efficiencies of the business</li> | <li>Increasing operational efficiencies of the business</li> | ||
| Line 250: | Line 241: | ||
<h3>Mobility for the Enterprise’s Workforce and Customers</h3> | <h3>Mobility for the Enterprise’s Workforce and Customers</h3> | ||
| − | Mobile platforms have created new business models. | + | Mobile platforms have created new business models. Improvements to mobile device technology in recent years have opened up many business opportunities, most notably the ability of mobile devices to be location-aware; however, location-awareness is just the tip of the iceberg. For example, some devices know about an individual’s medical information and physical state. These new capabilities have created not only incredible opportunities, but also daunting challenges for EIT including: |
<ul> | <ul> | ||
<li>Allowing employees to use mobile devices, whether owned by the employee or the company, for business purposes:</li> | <li>Allowing employees to use mobile devices, whether owned by the employee or the company, for business purposes:</li> | ||
<ul> | <ul> | ||
| − | <li>Protecting privacy and security both for the enterprise and the employee in using consumer devices in the workplace </li> | + | <li>Protecting privacy and security both for the enterprise and the employee in using consumer devices in the workplace.</li> |
| − | <li> | + | <li>Impacting the economics of the business and business/employee policies.</li> |
| − | <li>Protecting data on personal devices, even | + | <li>Protecting data on personal devices, even beyond email.</li> |
<li>Enabling employee mobility, originally for the sales force, but now for executives, engineers, etc. </li></ul> | <li>Enabling employee mobility, originally for the sales force, but now for executives, engineers, etc. </li></ul> | ||
<li>Configuring the enterprise platform to better support mobile services and applications for customers:</li> | <li>Configuring the enterprise platform to better support mobile services and applications for customers:</li> | ||
| − | <ul><li>Creating effective mobile delivery mechanisms</li> | + | <ul><li>Creating effective mobile delivery mechanisms.</li> |
| − | <li>Enabling more effective marketing to mobile customers</li> | + | <li>Enabling more effective marketing to mobile customers.</li> |
| − | <li>Addressing alternative media for viewing and use of video</li> | + | <li>Addressing alternative media for viewing and use of video.</li> |
</ul></ul> | </ul></ul> | ||
| Line 268: | Line 259: | ||
Information technology is evolving from a world that is server-centric to one that is service-centric. This is done by decoupling infrastructure, systems, applications, and business processes from one another. The move is away from monolithic systems wedded to one or more servers toward finer-grained, reusable services whether inside or outside the enterprise. The key challenges for our current security issues are: | Information technology is evolving from a world that is server-centric to one that is service-centric. This is done by decoupling infrastructure, systems, applications, and business processes from one another. The move is away from monolithic systems wedded to one or more servers toward finer-grained, reusable services whether inside or outside the enterprise. The key challenges for our current security issues are: | ||
<ul> | <ul> | ||
| − | <li>The lack of any U.S. or international standards for specifying security quality attributes that would enable the development of measurably secure systems | + | <li>The lack of any U.S. or international standards for specifying security quality attributes that would enable the development of measurably secure systems</li> |
| − | <li>Design, modeling, and coding tools that might automatically assess and validate security attributes | + | <li>Design, modeling, and coding tools that might automatically assess and validate security attributes</li> |
</ul> | </ul> | ||
<h1>EIT Challenges</h1> | <h1>EIT Challenges</h1> | ||
| − | |||
| − | In general, there are few regulatory frameworks in the IT environment, whether based on country, global, or sector. As a result, enterprises in the highly competitive, global IT environment that has few regulatory frameworks are constantly trying to outrun their competitors. | + | <h2>Regulatory Constraints: Country, Worldwide, and Sector-based</h2> |
| + | |||
| + | In general, there are few regulatory frameworks in the IT environment, whether based on country, global, or sector. As a result, enterprises in the highly competitive, global IT environment that has few regulatory frameworks are constantly trying to outrun their competitors. They are also creating their own regulatory constraints to help their business. | ||
| − | <h2>Lack of | + | <h2>Lack of Codified Knowledge and Training</h2> |
Currently, it typically takes months to years before a recent engineering graduate can become a fully productive member of an IT team. There are two reasons: | Currently, it typically takes months to years before a recent engineering graduate can become a fully productive member of an IT team. There are two reasons: | ||
| − | <ul> <li> | + | <ul><li>Most universities focus less on analyzing problems (and their root causes) and solving them than on the mechanics of using tools, and many are behind the times with respect to the technology and tools that they are teaching. The educational experience does not match the professional one. So, despite the extensive amount of learning being done in the classroom, a new-hire often still needs to be extensively trained to function in a real-world EIT organization. The ACM and the IEEE are working together to solve this problem with their reference curricula for IT and IS. (They have also produced reference curricula for Software Engineering, Computer Engineering, and Systems Engineering.)</li> |
| − | Most universities focus less on analyzing problems (and their root causes) and solving them than on the mechanics of using tools, and many are behind the times with respect to the technology and tools that they are teaching. The educational experience does not match the professional one. So, despite the extensive amount of learning being done in the classroom, a new-hire often still needs to be extensively trained to function in a real-world EIT organization. The ACM and the IEEE are working together to solve this problem with their reference curricula for IT and IS. (They have also produced reference curricula for Software Engineering, Computer Engineering and Systems Engineering.)</li> | + | |
| − | <li>Second, organizations rarely have enough internal documentation to support a fast onboarding of a new individual into their computing environment. This is often due to short-term thinking (today’s urgent issues are thought to be more important than laying a foundation for future success) as well as the fact that most IT grads lack fundamental writing skills. | + | <li>Second, organizations rarely have enough internal documentation to support a fast onboarding of a new individual into their computing environment. This is often due to short-term thinking (today’s urgent issues are thought to be more important than laying a foundation for future success) as well as the fact that most IT grads lack fundamental writing skills. Even engineers with the right background can take months to become productive. A lack of architectural information, software and database design principals, and so on slows the process greatly. </li></ul> |
| − | Many organizations are so complex that knowledge is fragmented, difficult to locate and share, and therefore redundant, inconsistent, or not used at all. Successful organizations pass their accumulated knowledge and commercial wisdom on to future organizational members via formal documentation, documented processes, methods, tools and techniques, such as mentoring and “buddy” systems. | + | Many organizations are so complex that knowledge is fragmented, difficult to locate and share, and therefore redundant, inconsistent, or not used at all. Successful organizations pass their accumulated knowledge and commercial wisdom on to future organizational members via formal documentation, documented processes, methods, tools, and techniques, such as mentoring and “buddy” systems. |
| − | Leading management theorists have popularized the concept of treating organizational knowledge as a valuable strategic asset. They advise that, to remain competitive, an organization must efficiently and effectively create, locate, capture, and share knowledge and expertise in order to apply that knowledge to solve problems and exploit opportunities. As more firms begin to incorporate onboarding and knowledge management into their overall business strategy, some are showing tremendous interest in leveraging these management processes and technologies. Although | + | Leading management theorists have popularized the concept of treating organizational knowledge as a valuable strategic asset. They advise that, to remain competitive, an organization must efficiently and effectively create, locate, capture, and share knowledge and expertise in order to apply that knowledge to solve problems and exploit opportunities. As more firms begin to incorporate onboarding and knowledge management into their overall business strategy, some are showing tremendous interest in leveraging these management processes and technologies. Although some are questioning the basic premise given the rapid changes in technology and communication mechanisms, others recognize the need to take advantage of the underlying principles that outlast specific technologies. |
<h2>Emerging Standardized Definitions of Relevant EIT Skills and Competencies</h2> | <h2>Emerging Standardized Definitions of Relevant EIT Skills and Competencies</h2> | ||
| − | The increasing globalization of | + | The increasing globalization of world economies is being fueled by a number of EIT technological changes. The challenge facing policy makers, practitioners, and academics is how to achieve significant and measurable improvements in addressing the rapid emergence of the information-rich economy. This requires strategies, standard practices, frameworks, and tools and techniques for ascertaining the effects of IT on critical infrastructures in government, civil society, and the private sector. |
| − | There are numerous emerging frameworks, taxonomies, and methods that are growing in visibility and use. Most of these are national frameworks that have evolved to meet their | + | There are numerous emerging frameworks, taxonomies, and methods that are growing in visibility and use. Most of these are national frameworks that have evolved to meet their government’s demands for EIT certifications. What is needed, though, is a consensually agreed framework that can be used as an international reference model. A representative set of frameworks relevant to codifying the skills needed by practitioners in the international community of EIT professionals are described in the sections below. |
<h3>Skills Framework for the Information Age (SFIA)</h3> | <h3>Skills Framework for the Information Age (SFIA)</h3> | ||
| − | SFIA is a model for describing and managing nearly 100 competencies for EIT professionals for the 21st century, and is intended to help match the skills of the workforce to the needs of the business. | + | Skills Framework for the Information Age (SFIA) is a model for describing and managing nearly 100 competencies for EIT professionals for the 21st century, and is intended to help match the skills of the workforce to the needs of the business. SFIA is also an international organization working to ensure cross-compatibility in IT qualifications across nations. |
| − | <h3>European Competency Framework</h3> | + | <h3>European e-Competency Framework (e-CF)</h3> |
| − | The European e-Competence Framework (e-CF) provides a reference of 40 competences as required and applied at the Information and Communication Technology (ICT) workplace, using a common language for competences, skills and proficiency levels that can be understood across Europe. | + | The European e-Competence Framework (e-CF) provides a reference of 40 competences as required and applied at the Information and Communication Technology (ICT) workplace, using a common language for competences, skills, and proficiency levels that can be understood across Europe. |
| − | <h3>i Competency Dictionary (Japan)</h3> | + | <h3>i Competency Dictionary (iCD) (Japan)</h3> |
| − | The very detailed | + | The very detailed i Competency Dictionary (iCD) was released as a structured dictionary combining a '''task dictionary''' with a '''skill dictionary''' on 31 July 2014, although work began as early as 2004. The iCD provides tasks, skills, roles, and jobs needed for not only the conventional business model such as system integrator but also new models such as security, cloud, and data science. |
| − | <h1>Other Relevant | + | <h1>Other Relevant BOKs</h1> |
| − | Guides to specific | + | Guides to specific bodies of knowledge (BOKs) provide pathways to the collected wisdom, experience, processes, and other knowledge to facilitate international agreement on guidelines, characteristics, and accepted practices for the area being discussed. There are several relevant bodies of knowledge and frameworks that were referenced in the development of the EITBOK: |
<ul> | <ul> | ||
<li>Guide to the Software Engineering Body of Knowledge (SWEBOK)</li> | <li>Guide to the Software Engineering Body of Knowledge (SWEBOK)</li> | ||
| Line 325: | Line 316: | ||
<h1>Summary</h1> | <h1>Summary</h1> | ||
| − | Enterprise IT has changed drastically over the last 20 years and it continues to change rapidly as its role within the organization changes, and as the nature and trends of global computing change. | + | Enterprise IT has changed drastically over the last 20 years and it continues to change rapidly as its role within the organization changes, and as the nature and trends of global computing change. The EITBOK is a collection of information about processes and standard practices to help give a high-level perspective of the EIT body of knowledge. |
Revision as of 01:57, 6 December 2017
|
Contents
1 Enterprise IT and the Business Environment
In this BOK, we have adopted the term enterprise information technology (EIT) to distinguish it from the IT industry at large, which includes companies that produce the technology that enterprise IT (EIT) employs, such as software packages, computers, and routers. Enterprise IT, as used in this guide, refers to IT services provided to (and maintained by) the enterprise by an IT department. Although the principles and standard practices covered in this guide can apply to technology put in place by non-IT personnel in other departments of the enterprise, when they are outside the purview of the IT department, they are not considered enterprise IT.
The business environment of an enterprise consists of all the internal and external factors that influence the performance and growth of the enterprise. The external factors include macro- and microeconomics, social trends, politics, technology, and others, and any of these factors can potentially help or harm the enterprise. The internal factors include things such as the enterprise’s objectives and goals, policies, methods, organizational structure, and management style, among others.
One of the internal factors is the capability and structure of the enterprise’s information technology function. What is interesting about this factor is that it is inextricably related to all the factors. In fact, successful EIT must take into account all the other functions’ directives, policies, goals, and constraints as inputs to its organizational and service design. All relevant environment factors need to be investigated, thoroughly understood, and documented so that they can be fully considered during the design of IT services. An added challenge is that these factors change—some frequently—which requires near constant reinvestigation of the business environment. To do its job right, EIT needs to have visibility into the enterprise’s understanding of all its business factors.
In many organizations, EIT has become a key functional area through which enterprises design new business processes and develop specialized organizational capabilities. These new processes and capabilities are not generated in isolation. Instead, EIT needs to be fully integrated with all departments where their solutions will have an effect. In today’s environment, that is typically the entire enterprise. In general, EIT provides the scaffolding over which business processes run, from one department to another. A good example of this is the order management process, which runs from the sales department taking an order, through billing and inventory management, to eventual delivery to the customer.
2 Defining Enterprise Information Technology
Enterprise IT (EIT) is made up of the people, processes, data, and technologies that support the enterprise. Enterprises collect data, analyze it, and then run their functions based upon information gathered or deduced. In essence, data flows through nearly all business processes to enable the organization to make decisions and take actions. Information technology enables the speedy flow of data through an enterprise. It also provides tools for data input, analysis, and sharing.
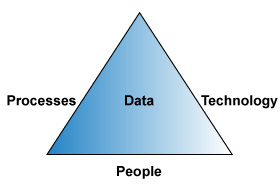
Figure 1. IT processes, data, technologies, and people support the enterprise
More explicitly, EIT supports the data needs of the enterprise by:
- Seeking to understand the business’s workings and needs for automation
- Planning technology changes based on business priorities
- Defining technology projects to bring about needed changes
- Delivering technology support for business processes
EIT professionals accomplish these things by building on existing national and international standards and frameworks (for building or acquiring and integrating technologies) and by relying on the knowledge of experts who develop guides to the specialized bodies of knowledge. Figure 2 reflects how standardized professional knowledge is used as a basis to provide secure, interoperable, and high-quality information technology to the enterprise.
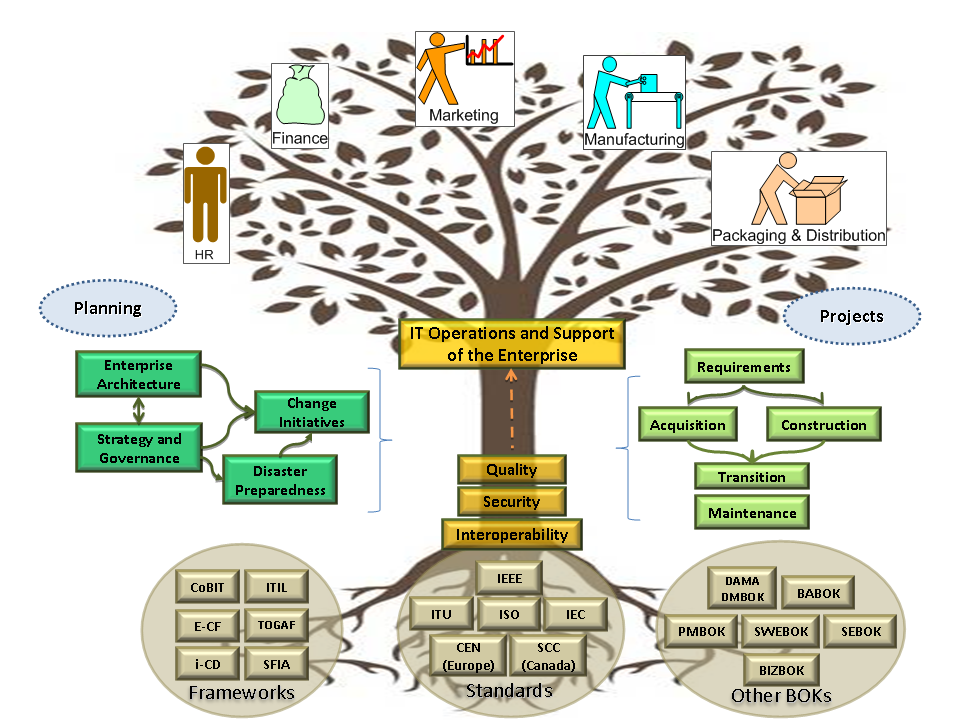
Figure 2. The enterprise ITG organization’s world
EIT is often described through a layered hierarchical architectural model (originally defined by the National Institute of Standards and Technology), which links the enterprise to the delivery of its products and services (shown in Figure 3). The original late 1980s NIST model provides an early view of defining enterprise IT via a layered hierarchical architectural model that links the business to the delivery of products and services. The layered views have retained their resiliency, although they are now generally represented as a BIAT model: Business, Information, Architecture, and Technology, as discussed in subsequent chapters of this guide.
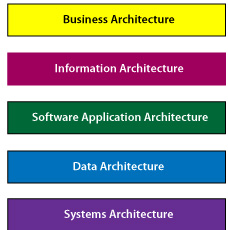
Figure 3. Enterprise IT hierarchy architectural model
At the business architecture layer, IT business strategy alignment, business case analysis, projected return on investments, prioritization, and resource allocation decisions are addressed. The results of these activities drive the development of the information architecture. The information architecture layer is where the information needed to support the business is defined and likely sources for the information are identified. The output of the information architecture provides the requirements for the information systems architecture.
The software application architecture layer defines the business applications that offer information services to business functions and to each other. The output of information systems architecture feeds the data architecture.
The data architecture is composed of enterprise models, policies, rules and standards that govern which data is collected, and how it is stored, arranged, integrated, kept secure and put to use.
Data flow is supported by the delivery systems architecture, which is composed of hardware, networks, and platform applications that offer platform services to each other and to business applications.
At each level of the EIT architecture, people, processes, data, and technology are interrelated. Although this is a layered architectural model of EIT, it should be noted that iteration between the layers and regression among the layers occurs depending on the needs of the organization. Also, the model permits external inputs, such as advancements in technologies, changes in business directions, regulatory changes, and other demands on the business.
3 Evolution of the Role of EIT
3.1 EIT Eras
The history of IT can be divided into four hardware-related eras: mainframes, personal computers (PCs), networks, and the World Wide Web. The computer industry was born with the first giant calculators—mainframes that digitally processed and manipulated numbers for specific purposes. EIT became a reality when general-purpose mainframes became commercially available and started to take on transaction-oriented activities within organizations, such as back-office accounting functions and airline reservations. Until the 1980s, most computer-related activities revolved around interactions between a specialist computer operator and a computer in a “glass house” to which ordinary workers weren’t allowed access. Enterprise IT was made possible through teams of in-house programmers who wrote the software needed to automate jobs within the enterprise.
When the first PCs arrived on the scene, they were simply a single-user, mini-mainframe that anybody could use. Of course, PCs unleashed a stream of shrink-wrapped, personal-productivity applications that contributed greatly to the growth of enterprise software and data. The role of IT at this point was to ensure that applications were available for the users that needed them to execute the specialized processes associated with their jobs. That, of course, then entailed trouble-shooting application and desktop problems for end users, and the era of desktop support was launched.
The role of IT took a major quantitative and qualitative leap when PCs became connected to each other—first through local area networks (LANs) and then across long-distances via wide area networks (WANs). Computer networks (and applications like email) enabled many process to become entirely digital, ensuring the proliferation of information, as well as drastically increasing the amount of data created, stored, moved, and consumed.
Connecting people in a vast and distributed network of computers not only increased the amount of data generated, but also led to new ways of getting value out of data through many new enterprise applications. It also created a new passion for “data mining.” In essence, networks changed the focus of IT from backroom operations to managing the integration of business processes for the enterprise. This change increased the role of the Chief Information Office to include management of the networks and the associated methods, processes, and technologies. The enterprise began to regard the IT role not as a specific function responsible for running the computer infrastructure, but as the core of their business.
The next phase of the EIT function came with the invention of the World Wide Web. While networks expanded IT into all corners of the enterprise, the World Wide Web expanded IT to all corners of the globe.
The introduction of the Web has led to the proliferation of new applications that are not limited to enterprise-related activities—they can be dynamically linked via enterprise networks to strategic partners and supply chains. The Web has provided individual users within an enterprise with tools and applications that greatly facilitate the creation and sharing of information with other business enterprise partners connected to the World Wide Web. With the introduction of web access to ever widening sources of data, EIT has become responsible for ever-larger data lakes and data pools. Data and its analysis has become even more of a competitive edge and given rise to a demand for “data scientists” within the enterprise, often in EIT itself.
3.2 The Evolution of EIT Structure
With the changing roles of EIT, the structure of the EIT department has had to change, as well. In the back-office, mainframe era, the IT organization structure was relatively simple, supporting back-office functions. There was an IT Director (who typically reported to a Chief Financial Officer), a manager of mainframe operations and computer operators—people who operated and maintained the hardware, and ran the jobs requested by specialized users, usually computer programmers. As time went on, a programming department grew to create and enhance critical back-office applications. So, there was a simple structure: an operations group that kept the hardware running and ran requested jobs on the mainframe and its output devices, and a simple programming services group that interfaced with the end users who needed the services of the mainframe. This was really the start of the development role of the IT organization. Users could request features and the IT department would run development projects that would add those features.
When PCs were added to the mix, the organization often added a new division specifically for desktop support—the care and feeding of the PCs and their users. These new functions required an entirely different set of skills, which put significant demands on the EIT department to modify how they supported their user community. Not only did the IT department need to understand PC hardware, but also the software that was now available to users. In addition, users started to become much more savvy of their computing hardware. In some situations, the user community knew more about their computing equipment and applications than the EIT staff, which caused significant conflicts about who was in control of the software and hardware—the users or EIT.
Before shrink-wrapped applications were available, it was EIT’s responsibility to support the users with customized productivity applications. Thus, the Development group had to become proficient in new areas.
The institution of the network and shared data added two new departments to the IT structure: network management as well as database development and management. By this point, EIT departments had transitioned into critical service providers. Enhancements and innovations to the services and functions that they provided were critical to the health of the organization. More and more, EIT departments started to become the nerve center of the enterprise; they transitioned into being EIT departments, and IT Directors became Chief Information Officers or Chief Technology Officers.
Once the Web entered the picture, even more aspects became critical, such as EIT security and open technology architectures. In addition, the proliferation of “outside” applications and functions require that EIT departments develop and enforce EIT processes and procedures for the entire enterprise.
In sum, EIT is the custodian of the massive investment in assets—the corporate information and the corporate technology to derive value from it. EIT has a responsibility (and accountability) to protect the confidentiality, integrity, and availability of that asset. Given that responsibility, it must also have the resources and the authority to carry it out.
What does the structure of today’s EIT department look like? That depends on the organization’s functions and needs for information technology. In addition, for any evolving organization, EIT’s structure also needs to evolve. Here is a simplistic view of the core EIT functions.
3.2.1 Shadow IT Groups
Shadow IT is a term often used to describe information-technology systems and solutions built and used inside an enterprise without explicit IT approval. It is also used, along with the term stealth IT, to describe solutions specified and deployed by departments other than the IT department. Lately, the term dark IT has cropped up. There are several good blogs about the problems that can arise from these other modes of IT, such as http://www.itskeptic.org/content/dark-it and http://bobmartens.net/2014/09/dark-it/.
Shadow IT is considered by many as an important source for innovation, and such systems can turn out to be important prototypes for future approved EIT solutions. On the other hand, shadow IT solutions can expose the enterprise to high levels of risk, since they are not often in line with the enterprise’s requirements for appropriate governance, security, and reliability, although these issues can apply equally to authorized EIT solutions.
Unofficial data flows that don’t go through EIT can be as simple as USB sticks or other portable data storage devices, online messaging software, email services, Google Docs, or other web-based collaboration tools. The challenges with shadow IT solutions are:
- Non-compliance with governmental or industrial standards (e.g., COBIT, GAAP, HIPAA, ITIL, Sarbanes-Oxley)
- Duplication of effort resulting in wasted resources
- Inconsistent business logic
- Higher risk of unauthorized intrusion, as well as data destruction, corruption, and leaks
- Security risks when data or applications are moved outside protected systems, networks, physical location, or security domains
- Lack of adequate user support when problems are encountered
3.2.2 Cost Center Versus Profit Center
EIT organizations service other organizations within the enterprise. In the traditional view, they don’t generate revenue, and as a result are considered cost centers. This point of view has EIT as a cost burden in the organization, and it typically leads to demands from management to cut costs. With the advent of better integration into the overall work of the enterprise and better portfolio management, EIT contributions have become more visible and more appreciated. EIT departments have put more resources into innovation, thus increasing their contributions to the bottom line. They also have worked to cut costs, of course, attempting to decrease the cost of maintaining existing solutions by better portfolio management, outsourcing maintenance activities, and using cloud computing; however, it is unclear whether these techniques are really decreasing costs in the long run.
Many people believe that EIT should be treated as a profit center. Note that EIT is often closely associated with profit centers, and the profit centers would not be functional without EIT’s efforts. For example, Amazon can’t really differentiate between its EIT function and its ability to make sales.
3.3 The Evolution of EIT Management Roles
The traditional head of the EIT department is the Chief Information Officer (CIO). This individual serves as the organization’s top information technology manager. The CIO runs the internal IT operations, and ensures that the organization’s IT infrastructure is in alignment with the business goals and needs. The CIO’s job is to be focused on satisfying internal customers, both users and business units, yet keep the cost of serving those customers at a reasonable level.
3.3.1 CIO Versus CTO and CMO
The Chief Information Officer, Chief Technology Officer, and the Chief Marketing Officer typically report to the CEO. Their functions are different, but sometimes overlapping.
The Chief Technology Officer (CTO) is the chief technology visionary for the enterprise. This is a technology-focused position. In a non-technical enterprise, the CTO usually reports to the CIO and is primarily concerned with long-term and over-arching technical issues, especially architectures. In technology-focused organizations, CIO and CTO can be at the same level with the CIO focused on the information technology that runs the enterprise and the CTO focused on the company’s core product technology and other supporting technologies.
The Chief Marketing Officer (CMO) is responsible for overseeing marketing initiatives within the organization. Even though this job’s main goal is to develop sales management, product development, distribution channel management, and customer service, the CMO’s job often bumps up against the CIO’s and CTO’s jobs in the area of marketing communications, especially in the areas of web advertising and social engineering.
3.3.2 Evolving EIT Roles
As EIT has become more diverse and more sophisticated, new roles have emerged, in addition to the classic roles of development and operations management.
The Chief Enterprise Architect (CEA) focuses on business modeling, processes, and integration. The CEA translates the business vision into effective enterprise change. The CEA works on creating technology and business process changes within the boundary of the business.
The Chief Data Officer (CDO) focuses on information, how data assets can be turned into useful and timely information, its accuracy, and the policies needed to protect it for its intended use.
The Chief Digital Officer (CDO) has an external customer interaction focus, and works to improve the value of interactions with user and customers.
The responsibilities of the Chief Web Officer (CWO) vary among enterprises, depending on the needs and goals of the business. A CWO should have a deep and broad understanding of the Web and website governance issues including online strategy, systems and software administration, web hosting, e-commerce, online community and social media, web content development and workflows, website graphic design, user experience (analysis/design), website analytics, and security, among others.
Note that in many organizations, especially smaller ones, one person may carry out several of the above responsibilities.
3.4 Evolving EIT Standards
~ Craig Barrett, former Intel CEO
Over time, technical standards have emerged as the industry has demanded common interfaces and common protocols, as well as standard reference models. One well-known evolutionary path is that of proprietary standards for manual and electronic communication within the enterprise (e.g., mainframe) in the 1970s; emerging standards for intra-enterprise technology and communication (e.g., TCP/IP, Client Server) in the 1980s; and open standards based on common technology and communications protocols (e.g., XML, Linux , JBOSS) in the 1990s and 2000s. Companies use standards associated with their infrastructure service provider (ISP) and application service provider (ASP) approaches. These technical standards, whether created by formal standards developing organizations (SDOs) like the IEEE and ISO, or by industry consortia like the Open Group, are needed by the EIT community across the world, so that each EIT organization does not have to reinvent the wheel and reinvent ways to communicate each time a new relationship is created. Thus, they promote the flow of electronic data and knowledge in a global economy. For example, in a global EIT community:
- Each morning, companies receive software that was written in India overnight in time to be tested in their country and returned to India for further production that same evening—making the 24-hour workday a practicality.
- Back-offices of firms operate in such places as Costa Rica, Ireland, and Switzerland.
- Drawings for architectural firms are produced in Brazil.
- Call centers are based in India, where employees are now being taught to speak with client based accents.
- Hospitals have x-rays and CAT scans read by radiologists in Australia and India.
- At some McDonald’s drive-in windows orders are transmitted to a processing center a thousand miles away (currently in the U.S.), where they are processed and returned to the worker who actually prepares the order.
- Accounting firms have client’s tax returns prepared by experts in India.
- Visitors to an office not far from the White House are greeted on a flat screen display by a receptionist who controls access to the building and arranges contacts; the person behind the flat screen is in Pakistan.
- Surgeons sit on the opposite side of the operating room and control robots that perform the procedures. It is not a huge leap of imagination to have highly specialized, world-class surgeons located not just across the operating room but geographically separated by large distances.
3.5 Evolving EIT Methods
~ Edsger Dijkstra, The Humble Programmer (EWD340)
And now that we have thousands of interlinked computers, both programming and the development of the technology infrastructure that the software runs on have become exponentially more complex. Thus, we have seen an increase in the need for standards, reference models, and frameworks. At the same time, professionals have sought more effective ways to build systems to meet expectations of budget and capabilities.
Djikstra put forth one of the earliest codifications of practice in his proposals for structured programming. He campaigned for more discipline in programming, and pointed out that software productivity was closely related to rigor in design.
As IBM and other systems integrators became widely used by EIT organizations to build internal systems for them, EIT practitioners learned the contractors’ methods for completing contracts on time and budget. These methods were also adopted by various government agencies in order to control their expenses in having technology outsourced. Essentially, these were project management processes that provided for distinct approval points in the development of the technology: requirements sign-off, design sign-off, etc. Theoretically, once each “stage” was approved, the project was on-track. This approach has popularly been called the Waterfall Method. Many systems integrators packaged their project management processes as methodologies, with brands like Navigator, and sold them to their EIT clients.
Software product companies, on the other hand, arose quickly in the 1970s and 1980s, and rejected the systems integrators’ approach as too cumbersome. One of the most important things they instituted was the concept of the product management team, wherein each stakeholder in the product had a place at the table where decisions were made. These teams included the product manger, the development manger, the test manager, the documentation manager, and customer support manager, at a minimum.
Since then, many different approaches have had their day, such as Rapid Application Development in the 1990s and, since then, various “agile” approaches (Scrum, DSDM, feature-driven development, test-driven development, etc.).
DevOps goes a step further than previous EIT approaches, and is somewhat akin to the use of product teams in software product companies, in that it takes into account the need for discipline in the transition of new EIT capabilities from development (or acquisition) to the operations arm of EIT.
DevOps is the practice of operations and development engineers participating together in the entire service lifecycle, from design through the development process to production support, most notably characterized by operations staff making use of many of the same techniques as developers for their systems work. DevOps brings discipline to the process of delivering capabilities by using continuous integration and continuous deployment, and rigorous configuration management, along with dependence on metrics and monitoring schemes.
Still, the twin plagues underlying the software crisis of the 1960s bedevil us today.
4 Current Trends in the Enterprise IT Landscape
~ Raymond Kurzweil, Google
It is these accelerating information technologies that can instigate major innovations in enterprises, ranging from energy and the environment, to health systems and telecommunications. With this strong focus on information technology, the planet seems to getting smaller, flatter, and smarter every day. New businesses and business models have come into existence and old ones are dying at a tremendous speed. The exponential increase in both intelligence and information in consumer devices is incredible. Now cars, kitchen appliances, electrical systems, traffic systems, and even clothing contain sophisticated computational devices, many or most of which plug into “the grid.” This trend has greatly changed not only our lives, but the nature of EIT.
There are a number of current technology trends that are driving the EIT business environment. Businesses are working hard to gain or maintain a leadership role in these areas; however, being on the leading edge often means being on the bleeding edge. The challenges are significant and often painful. We discuss a few of those trends here.
4.1 Big Data and Predictive Analytics
Early in the age of data collection, enterprises viewed collecting data as a way to support their enterprise applications for customer relationship management (CRM) and enterprise resource planning (ERP) as well as manufacturing. But more recently, the trend has been to collect nearly all the information that they can about their users (characteristics, preferences, and actions), their own processes (building and plant performance), and business trends, among other things. Most businesses these days collect huge amounts of disparate and unstructured data, and the data being collected goes well beyond what they need to serve their customers and operate standard business functions. Instead, huge amounts of data are grabbed in the hope of predicting the future.
Leading enterprises are not putting effort into understanding the data that they have collected just to help them drive key business decisions. Data collection and analysis is now a critical part of business intelligence and the enterprise’s ability to predict the future; however, many feel that careful analysis of often disparate datasets can also aide enterprises in optimizing their predictive analytics capabilities across the enterprise. Key challenge areas for current EIT functions to support the data analysis needs of the enterprise are:
- Providing advanced analytics to support definition, growth, and nurturing of commercial services.
- Leveraging data to enhance customer relationship management (CRM).
- Enabling predictive analytics from large disparate data sources to improve effectiveness (such as predicting or anticipating customer behavior, plant monitoring, planning plant equipment upgrades, and diagnosing customer equipment issues).
4.2 Social Platforms
Due to the evolution of social media and social platforms, static company websites are often not necessarily the first or most effective way to engage customers. This change has required that organizations rethink their online marketing (and data collection) strategies. Social media and platforms have given enterprises new opportunities to attract customers, but this requires that EIT learn new skills to match the media. For example, the social identities of individuals, which are often based on a rich history of information about the individual and their activities, have become much more valuable than the isolated information obtained when an individual visits or even registers on an enterprise’s website. Key social media/platform challenges for current EIT professionals include:
- Dealing with multiple and ever-growing sources and amounts of data that often are not directly correlated with each other or with the enterprise’s business.
- Effectively working with both unstructured data (such as data from social networking, email, chats) and other organizations’ structured data (such as database formats and attributes).
4.3 Cyber Security and Data Privacy
The fortress mentality, in which all EIT has to be architected to be shut off from the world, is no longer viable. Instead, enterprises need to develop a security architecture that responds appropriately to threats when and where they happen. Automated capabilities that detect, assess, and respond immediately are a focus for most organizations. However, organizations need to put significant effort into identifying the necessary and appropriate security designs, quality and performance attributes, and appropriate risk/cost tradeoffs that drive how security is positioned within the organization, and how it relates to the overall system/EIT architecture.
In addition, individual privacy and protection of data has been taking center stage—especially in Europe—as a result of increased government regulation, policy enforcement, and public outcry about the increasing number of data breaches. Leading enterprises, public and private, governmental and commercial, are developing a better understanding about the distinctions between being a data processor (i.e., broadly handling the personal data of others) versus a data controller. Key challenges for the EIT environment are:
- Figuring out how to better protect
- Enterprise technology assets (e.g., networks, applications, and databases)
- Customer information
- Employee information
- EIT’s services from operational disruption
- EIT’s community and work against terrorism and external attack
- Figuring out how to comply with government and industry regulations, such as payment card industry (PCI) and HIPAA requirements.
4.3.1 Cloud Services and Service Oriented Architectures (SOA)
Cloud computing has evolved to a point where the term itself has become nearly superfluous. Hybrid clouds—software-as-a-service (SaaS) and platform-as-a-service (PaaS), in combination with internal applications—are cementing EIT’s role as a driver of business growth. The cloud-computing focus is shifting from providing simple infrastructure solutions to developing cloud strategies that deliver increased functionality and flexibility, whie maintaining security and reliability. These strategies use a mix of public and private cloud-based applications and platform services. While many challenges remain, cloud technologies are nonetheless poised to change the face of enterprise computing. Key challenges for the current EIT organization are:
- Leveraging repeatable (SOA) technologies across platforms (e.g., web, mobile devices, customer support, and self-service).
- Combining and leveraging internal/private and external/public cloud computing.
- Using cloud services to leverage new and existing data.
- Decreasing time and costs to market and support enterprise needs via:
- Increasing flexibility of platforms
- Increasing operational efficiencies of the business
- Increasing utilization of commercial services
4.3.2 Mobility for the Enterprise’s Workforce and Customers
Mobile platforms have created new business models. Improvements to mobile device technology in recent years have opened up many business opportunities, most notably the ability of mobile devices to be location-aware; however, location-awareness is just the tip of the iceberg. For example, some devices know about an individual’s medical information and physical state. These new capabilities have created not only incredible opportunities, but also daunting challenges for EIT including:
- Allowing employees to use mobile devices, whether owned by the employee or the company, for business purposes:
- Protecting privacy and security both for the enterprise and the employee in using consumer devices in the workplace.
- Impacting the economics of the business and business/employee policies.
- Protecting data on personal devices, even beyond email.
- Enabling employee mobility, originally for the sales force, but now for executives, engineers, etc.
- Configuring the enterprise platform to better support mobile services and applications for customers:
- Creating effective mobile delivery mechanisms.
- Enabling more effective marketing to mobile customers.
- Addressing alternative media for viewing and use of video.
4.3.3 Architectural Changes
Information technology is evolving from a world that is server-centric to one that is service-centric. This is done by decoupling infrastructure, systems, applications, and business processes from one another. The move is away from monolithic systems wedded to one or more servers toward finer-grained, reusable services whether inside or outside the enterprise. The key challenges for our current security issues are:
- The lack of any U.S. or international standards for specifying security quality attributes that would enable the development of measurably secure systems
- Design, modeling, and coding tools that might automatically assess and validate security attributes
5 EIT Challenges
5.1 Regulatory Constraints: Country, Worldwide, and Sector-based
In general, there are few regulatory frameworks in the IT environment, whether based on country, global, or sector. As a result, enterprises in the highly competitive, global IT environment that has few regulatory frameworks are constantly trying to outrun their competitors. They are also creating their own regulatory constraints to help their business.
5.2 Lack of Codified Knowledge and Training
Currently, it typically takes months to years before a recent engineering graduate can become a fully productive member of an IT team. There are two reasons:
- Most universities focus less on analyzing problems (and their root causes) and solving them than on the mechanics of using tools, and many are behind the times with respect to the technology and tools that they are teaching. The educational experience does not match the professional one. So, despite the extensive amount of learning being done in the classroom, a new-hire often still needs to be extensively trained to function in a real-world EIT organization. The ACM and the IEEE are working together to solve this problem with their reference curricula for IT and IS. (They have also produced reference curricula for Software Engineering, Computer Engineering, and Systems Engineering.)
- Second, organizations rarely have enough internal documentation to support a fast onboarding of a new individual into their computing environment. This is often due to short-term thinking (today’s urgent issues are thought to be more important than laying a foundation for future success) as well as the fact that most IT grads lack fundamental writing skills. Even engineers with the right background can take months to become productive. A lack of architectural information, software and database design principals, and so on slows the process greatly.
Many organizations are so complex that knowledge is fragmented, difficult to locate and share, and therefore redundant, inconsistent, or not used at all. Successful organizations pass their accumulated knowledge and commercial wisdom on to future organizational members via formal documentation, documented processes, methods, tools, and techniques, such as mentoring and “buddy” systems.
Leading management theorists have popularized the concept of treating organizational knowledge as a valuable strategic asset. They advise that, to remain competitive, an organization must efficiently and effectively create, locate, capture, and share knowledge and expertise in order to apply that knowledge to solve problems and exploit opportunities. As more firms begin to incorporate onboarding and knowledge management into their overall business strategy, some are showing tremendous interest in leveraging these management processes and technologies. Although some are questioning the basic premise given the rapid changes in technology and communication mechanisms, others recognize the need to take advantage of the underlying principles that outlast specific technologies.
5.3 Emerging Standardized Definitions of Relevant EIT Skills and Competencies
The increasing globalization of world economies is being fueled by a number of EIT technological changes. The challenge facing policy makers, practitioners, and academics is how to achieve significant and measurable improvements in addressing the rapid emergence of the information-rich economy. This requires strategies, standard practices, frameworks, and tools and techniques for ascertaining the effects of IT on critical infrastructures in government, civil society, and the private sector.
There are numerous emerging frameworks, taxonomies, and methods that are growing in visibility and use. Most of these are national frameworks that have evolved to meet their government’s demands for EIT certifications. What is needed, though, is a consensually agreed framework that can be used as an international reference model. A representative set of frameworks relevant to codifying the skills needed by practitioners in the international community of EIT professionals are described in the sections below.
5.3.1 Skills Framework for the Information Age (SFIA)
Skills Framework for the Information Age (SFIA) is a model for describing and managing nearly 100 competencies for EIT professionals for the 21st century, and is intended to help match the skills of the workforce to the needs of the business. SFIA is also an international organization working to ensure cross-compatibility in IT qualifications across nations.
5.3.2 European e-Competency Framework (e-CF)
The European e-Competence Framework (e-CF) provides a reference of 40 competences as required and applied at the Information and Communication Technology (ICT) workplace, using a common language for competences, skills, and proficiency levels that can be understood across Europe.
5.3.3 i Competency Dictionary (iCD) (Japan)
The very detailed i Competency Dictionary (iCD) was released as a structured dictionary combining a task dictionary with a skill dictionary on 31 July 2014, although work began as early as 2004. The iCD provides tasks, skills, roles, and jobs needed for not only the conventional business model such as system integrator but also new models such as security, cloud, and data science.
6 Other Relevant BOKs
Guides to specific bodies of knowledge (BOKs) provide pathways to the collected wisdom, experience, processes, and other knowledge to facilitate international agreement on guidelines, characteristics, and accepted practices for the area being discussed. There are several relevant bodies of knowledge and frameworks that were referenced in the development of the EITBOK:
- Guide to the Software Engineering Body of Knowledge (SWEBOK)
- A Guide to the Project Management Body of Knowledge (PMBOK)
- A Guide to the Project Management Body of Knowledge – Software Extension (PMBOK - SWX)
- Canadian Information Technology Body of Knowledge (CITBOK)
- DAMA International’s Data Management Body of knowledge (DAMA_DMBOK)
- The Service Quality Body of Knowledge (SQBOK)
- Guide to the Systems Engineering Body of Knowledge (SEBoK)
- Business Analyst Body of Knowledge (BABOK)
- Business Architecture Guild’s Body of Knowledge (BizBOK)
7 Summary
Enterprise IT has changed drastically over the last 20 years and it continues to change rapidly as its role within the organization changes, and as the nature and trends of global computing change. The EITBOK is a collection of information about processes and standard practices to help give a high-level perspective of the EIT body of knowledge.