Difference between revisions of "Security"
| (94 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | < | + | <table border="3"> |
| − | + | <tr><td> | |
| + | <table> | ||
| + | <tr> | ||
| + | <td width="60%"><font color="#246196">'''Welcome to the initial version of the EITBOK wiki. Like all wikis, it is a work in progress and may contain errors. We welcome feedback, edits, and real-world examples. [[Main_Page#How to Make Comments and Suggestions|Click here]] for instructions about how to send us feedback.''' </font></td> | ||
| + | <td width="20%">[[File:Ieee logo 1.png|100px|center]]</td> | ||
| + | <td width="20%"> [[File:Acm_logo_3.png|175px|center]]</td> | ||
| + | </tr></table> | ||
| + | </td></tr></table> | ||
| + | <p> </p> | ||
<h2>Introduction</h2> | <h2>Introduction</h2> | ||
| − | <div style="margin-left: 5em;"><p>'' | + | <div style="margin-left: 5em;"><p>''"There are only two types of companies: those that have been hacked, and those that will be." <br />~ FBI Director Robert Mueller, October 2012</p></div> |
| − | <div style="margin-left: 5em;"><p>'' | + | <div style="margin-left: 5em;"><p>''"There are two kinds of big companies in the United States. There are those who've been hacked by the Chinese and those who don't know that they've been hacked by the Chinese." <br />~ FBI Director James Comey, October 2014</p></div> |
| − | <p>Whether you call it computer security, cybersecurity, or EIT security, one thing is true, technological security is a rapidly changing area. The change is so rapid that it is nearly impossible for organizations (whether commercial, educational, or governmental) to keep up with the perpetrators of cyberattacks. Attacks that used to be carried out by lone individuals trying to see if they could get access to | + | <p>Whether you call it computer security, cybersecurity, or EIT security, one thing is true, technological security is a rapidly changing area. The change is so rapid that it is nearly impossible for organizations (whether commercial, educational, or governmental) to keep up with the perpetrators of cyberattacks. Attacks that used to be carried out by lone individuals trying to see if they could get access to "secure" servers are now being organized and financed by governments. The way that an organization approached security in 2005 isn't sufficient in 2017, and we are pretty sure that it will be a totally different world in 2025. Flexibility and adaptability in this area is essential. </p> |
<p>Organizations (both small and large) depend on information technology and the information systems that are developed to successfully carry out their missions and business functions. Information systems can include a vast range of diverse computing platforms from high-end supercomputers and highly virtualized platforms to tablets and mobile devices. Information systems also include specialized systems and devices, such as telecommunication systems, industrial/process control systems, testing and calibration devices, weapons systems, command and control systems, and environmental control systems. '''All of these systems are subject to serious threats''' that can have adverse impacts on organizational operations, assets, individuals, associated organizations, and even countries by compromising the confidentiality, integrity, or availability of information being processed, stored, or transmitted by those systems.</p> | <p>Organizations (both small and large) depend on information technology and the information systems that are developed to successfully carry out their missions and business functions. Information systems can include a vast range of diverse computing platforms from high-end supercomputers and highly virtualized platforms to tablets and mobile devices. Information systems also include specialized systems and devices, such as telecommunication systems, industrial/process control systems, testing and calibration devices, weapons systems, command and control systems, and environmental control systems. '''All of these systems are subject to serious threats''' that can have adverse impacts on organizational operations, assets, individuals, associated organizations, and even countries by compromising the confidentiality, integrity, or availability of information being processed, stored, or transmitted by those systems.</p> | ||
<p>Threats to information and information systems include environmental disruptions, human and machine errors, and purposeful attacks. Cyberattacks on information systems today are often aggressive, disciplined, well-organized, long-term, well-funded, and in a growing number of documented cases, extremely sophisticated. Successful attacks on public and private sector information systems (especially toward critical infrastructure) can result in serious damage not only to the organization that was attacked, but also to the national and economic security interests of an entire country.</p> | <p>Threats to information and information systems include environmental disruptions, human and machine errors, and purposeful attacks. Cyberattacks on information systems today are often aggressive, disciplined, well-organized, long-term, well-funded, and in a growing number of documented cases, extremely sophisticated. Successful attacks on public and private sector information systems (especially toward critical infrastructure) can result in serious damage not only to the organization that was attacked, but also to the national and economic security interests of an entire country.</p> | ||
| − | <p>We make an attempt in this chapter to describe EIT security | + | <p>We make an attempt in this chapter to describe EIT security as we know it today. We highlight the current challenges and indicate some of the most successful processes that enterprises use in this ongoing battle.</p> |
<h2>Goals and Principles</h2> | <h2>Goals and Principles</h2> | ||
<p>While there are many definitions for security, most include the three dimensions of [http://eitbokwiki.org/Glossary#ciatriad confidentiality, integrity, and availability] (sometimes referred to as the ''CIA triad''). As such, the primary goal of EIT security is to preserve the ''confidentiality, integrity, and availability of information and information systems''. [[#One|[1]]]</p> | <p>While there are many definitions for security, most include the three dimensions of [http://eitbokwiki.org/Glossary#ciatriad confidentiality, integrity, and availability] (sometimes referred to as the ''CIA triad''). As such, the primary goal of EIT security is to preserve the ''confidentiality, integrity, and availability of information and information systems''. [[#One|[1]]]</p> | ||
| − | <p>The principles behind an | + | <p>The principles behind an organization's [http://eitbokwiki.org/Glossary#isms information security management system (ISMS)] should be to design, implement, and maintain a coherent set of policies, processes, and systems that keep the risks associated with its information assets at a tolerable level, and yet, manage the cost and inconvenience of said risk management. As such, the goals of EIT security are to:</p> |
<ul> | <ul> | ||
<li>Always understand the current risk tolerance of the enterprise with respect to information and device security.</li> | <li>Always understand the current risk tolerance of the enterprise with respect to information and device security.</li> | ||
| Line 18: | Line 26: | ||
</ul> | </ul> | ||
<h2>Context Diagram</h2> | <h2>Context Diagram</h2> | ||
| − | [[File: | + | <p>[[File:05 Security CD.png|700px]]<br />'''Figure 1. Context Diagram for Security'''</p> |
| − | < | + | |
<h2>Information Security Management</h2> | <h2>Information Security Management</h2> | ||
| − | <div style="margin-left: 5em;"><p>'' | + | <div style="margin-left: 5em;"><p>''"An information security management system (ISMS) includes policies, processes, procedures, organizational structures, software, and hardware to protect the identified information assets. These controls need to be specified, implemented, monitored, reviewed, and improved where necessary, to ensure that the specific information security and business objectives of the organization are met. Relevant information security controls are expected to be seamlessly integrated with an organization's business processes." ~ ISO/IEC 27002:2013, Clause 3.2.3 Information security, Pg. 26 [[#Three|[3]]]</p></div> |
<p>An ISMS must remain in place and be effective for a long period of time; however, it must also be able to adapt to changes in the EIT organization and the solutions that it supports, as well as evolving security threats. As a result, the ISMS must be carefully designed, implemented with care, strongly managed, and continuously reevaluated and updated.</p> | <p>An ISMS must remain in place and be effective for a long period of time; however, it must also be able to adapt to changes in the EIT organization and the solutions that it supports, as well as evolving security threats. As a result, the ISMS must be carefully designed, implemented with care, strongly managed, and continuously reevaluated and updated.</p> | ||
<h3>Security Management Practices and Frameworks</h3> | <h3>Security Management Practices and Frameworks</h3> | ||
| − | <p>A mature ISMS uses an information security framework to achieve the | + | <p>A mature ISMS uses an information security framework to achieve the enterprise's objectives. Such a framework is a series of documented processes that are used to define policies and procedures that support the implementation and ongoing management of information security controls. A framework is basically a blueprint for building an information security program to manage risk and reduce vulnerabilities, and to define and prioritize the tasks required to build security into an organization.</p> |
<p>There are several mature information security frameworks, including the following more widely used frameworks:</p> | <p>There are several mature information security frameworks, including the following more widely used frameworks:</p> | ||
<ul> | <ul> | ||
| − | <li>'''ISO/IEC 27000 Series''' | + | <li>'''ISO/IEC 27000 Series'''—The International Organization for Standardization (IOS) and the International Electrotechnical Commission (IEC) provide recommended practices on information security management and program elements. ISO defines the broadest structure of an effective overall program, supporting information security as a systems issue that includes technology, practice, and people. It also describes the need for a formal security program.</li> |
| − | <li>'''NIST SP 800 Series''' | + | <li>'''NIST SP 800 Series'''—The National Institute of Standards and Technology (U.S. Department of Commerce) has produced a number of special publications (the 800 series) that are specifically focused on computer security. This series discusses the Information Technology Laboratory's research, guidelines, and outreach efforts concerning computer security, along with its collaborative activities with industry, government, and educational institutions. Some examples of these collaborations include catalogs of security controls for information systems (800-53).</li> |
| − | <li>'''COBIT''' | + | <li>'''COBIT'''—The Control Objectives for Information and Related Technology (COBIT) is a set of mythologies and practices for EIT management that focuses on defining program and management control functions. Use of these standard practices can help ensure that EIT programs are implemented and managed effectively. COBIT states that the security publication "provides guidance to help EIT and security professionals understand, utilize, implement, and direct important information-security-related activities, and make more informed decisions while maintaining awareness about emerging technologies and the accompanying threats."</li> |
| − | <li>''Information Security | + | <li>''Information Security Forum's Standard of Good Practice'''—This document is a comprehensive, business-focused guide to managing information security risks. It is aligned with the requirements for an ISMS as described in the ISO/IEC 2700X standards. It provides deeper coverage for most of the control topics.</li> |
| − | <li>'''ISACA RISK IT''' | + | <li>'''ISACA RISK IT'''—The Information Systems Audit and Control Association (ISACA) has produced a Risk IT framework that aims to fill the gap between generic risk management frameworks and more specific EIT risk management frameworks. It provides a wide view of all risks related to EIT and a similarly thorough treatment of risk management. It builds upon the other risk-related components within the current ISACA frameworks, such as COBIT and Val IT.</li> |
| − | <li>'''OCTAVE''' | + | <li>'''OCTAVE'''—The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) method is used to assess an organization's information security needs. OCTAVE methods are self-directed and flexible. Small teams across business units and EIT can work together to address the security needs of the enterprise. OCTAVE can be customized to match the organization's unique risk environment, security and resilience objectives, and skill level. OCTAVE moves an organization toward an operational risk-based view of security and puts it in a business context.</li> |
| − | <li>'''COSO''' | + | <li>'''COSO'''—The Committee of Sponsoring Organizations (COSO) of the Treadway Commission has created a list of control objectives for enterprise governance and risk management. COSO defines a set of business, management, and security-relevant controls that can be used to demonstrate good business practices, and can be used to show compliance with Sarbanes-Oxley.</li> |
| − | <li>'''HITRUST CSF''' | + | <li>'''HITRUST CSF'''—This is a certifiable framework that provides healthcare-relevant security regulations and standards. It describes a flexible approach to risk management and compliance for the HIPAA and HITECH regulations (described later). At the present time, it is the most widely adopted security framework by the US healthcare industry.</li> |
</ul> | </ul> | ||
| − | <h3> | + | <h3>Cybersecurity Laws and Regulations Factor</h3> |
| − | <p>An ISMS cannot be constructed without considering the laws and regulations that affect the enterprise. The issue here is that those laws and regulations are under constant flux. When | + | <p>An ISMS cannot be constructed without considering the laws and regulations that affect the enterprise. The issue here is that those laws and regulations are under constant flux. When investigating cybersecurity laws and regulations, we have to look at local, state, national, and international regulations. We also have to consider regulations specific to the enterprise's industry, such as health care. For larger organizations that have significant risk, security lawyers may be required to identify relevant regulations and to keep track of new legislation. Here is a brief overview. [[#Sixteen|[16]]]</p> |
| − | <p>Each country has its own laws, and those laws differ a great deal. Over the last several years, the UN has taken up the issue of cybersecurity. In 2013, the United Nations Group of Governmental Experts (GGE) published a report that listed a set of | + | <p>Each country has its own laws, and those laws differ a great deal. Over the last several years, the UN has taken up the issue of cybersecurity. In 2013, the United Nations Group of Governmental Experts (GGE) published a report that listed a set of "high-level cyber norms" that all countries should follow. They include:</p> |
<ul> | <ul> | ||
<li>Abide by international law when operating in cyberspace.</li> | <li>Abide by international law when operating in cyberspace.</li> | ||
| − | <li>Honor the | + | <li>Honor the "norm of state responsibility" for cyberattacks emanating from their territory.</li> |
<li>Work to develop confidence-building measures to reduce risk of conflict.</li> | <li>Work to develop confidence-building measures to reduce risk of conflict.</li> | ||
| − | <li>Engage in capacity building efforts to assist developing countries build skills to protect their networks and citizens.</li> | + | <li>Engage in capacity-building efforts to assist developing countries build skills to protect their networks and citizens.</li> |
</ul> | </ul> | ||
<p>The GGE meets fairly regularly to build on their work and have recently taken on defining limits on the use of national cyberpower aimed at the critical infrastructure of other states.</p> | <p>The GGE meets fairly regularly to build on their work and have recently taken on defining limits on the use of national cyberpower aimed at the critical infrastructure of other states.</p> | ||
<h4>Laws and Regulations Outside the United States</h4> | <h4>Laws and Regulations Outside the United States</h4> | ||
| − | <p>As mentioned above, cybersecurity is a fast changing area globally. Although the US, China, and Russia have been considered in the lead, most countries have basic cybersecurity laws and policies. Many of those are associated with the | + | <p>As mentioned above, cybersecurity is a fast-changing area globally. Although the US, China, and Russia have been considered in the lead, most countries have basic cybersecurity laws and policies. Many of those are associated with the country's national security and defense strategies. It would take too long to go through every country, so we have picked a few to discuss. For information about specific countries and their policies and security strategies, visit https://ccdcoe.org/cyber-security-strategy-documents.html.</p> |
<ul> | <ul> | ||
| − | <li>'''China''' | + | <li>'''China'''—China has a set of the world's tightest Internet restrictions and this is part of their cybersecurity strategy. They have numerous laws that authorize the control of flow of online information in the country and many foreign sites are blocked. Laws also require companies to censor and restrict online anonymity, to store user data in China, and to monitor and report all network security incidents. China is serious about security and jails more people for computer "misuse" than any other country; however, most of the people are arrested as part of their censorship laws, not cybercrimes. Blogs and social-site posts critical of the government usually result in an arrest. </li> |
| − | <li>'''Russia''' | + | <li>'''Russia'''—Like China, for many years Russia was worried about cybercontent (the information) more than cybersecurity. However, they have not overtly censored social media or blogs, like the Chinese. In addition, they have maintained a strict "non-interference" policy concerning their cyberspace, which has pushed them to create numerous international non-interference pacts. Russia has well-developed tools for incident detection and is also considered a leader in developing software and techniques for cybercrime. Interestingly enough, it has only been since 2012 or so that Russia started to take cybercrimes committed by Russians seriously.</li> |
| − | <li>'''The European Union''' | + | <li>'''The European Union'''—In 2013, the European Commission and High Representative's ''Cyber Security Strategy'' document was the first comprehensive EU document concerning cyberspace. It set the tone of the EU's strategy as "open, safe, and secure," and it specified how the EU would approach building their cybersecurity capacity. In August 2015, the EU proposed a strict law to impose security requirements on Internet service providers and web companies. The new law also requires reporting data breaches to EU governments. One of the critical points brought up in the deliberations of the law is that if a cloud computing company or ISP does business with a "critical sector" company, the web company needs to follow the same security rules as the critical sector company.</li> |
</ul> | </ul> | ||
<h4>Laws and Regulations in the United States</h4> | <h4>Laws and Regulations in the United States</h4> | ||
<h5>National Laws and Regulations</h5> | <h5>National Laws and Regulations</h5> | ||
| − | <p>Over the last 15 year, the US federal government has lead the way in developing laws and regulations regarding cyberhacking and cybersecurity. The laws treat different organization types differently, so some enterprises are strongly affected by cybersecurity laws and regulations while other are not affected at all. Despite the fact that most people believe that cybersecurity regulations are necessary, there is a lot of disagreement about who these laws should regulate. Some people believe that laws should cover only acts of breaching security (hacking). Others think that laws | + | <p>Over the last 15 year, the US federal government has lead the way in developing laws and regulations regarding cyberhacking and cybersecurity. The laws treat different organization types differently, so some enterprises are strongly affected by cybersecurity laws and regulations while other are not affected at all. Despite the fact that most people believe that cybersecurity regulations are necessary, there is a lot of disagreement about who these laws should regulate. Some people believe that laws should cover only acts of breaching security (hacking). Others think that there should be laws to regulate businesses and how they protect data.</p> |
| − | <p>In the US, cybersecurity regulation consists of directives (both administrative directives and legislation) that safeguard information technology and computer systems. The purpose of these directives is to force companies and organizations to protect their systems and information from cyberattacks, such as viruses, worms, Trojan horses, phishing, [http://eitbokwiki.org/Glossary#dos denial-of-service (DOS)] attacks, unauthorized access (stealing intellectual property or confidential information), | + | <p>In the US, cybersecurity regulation consists of directives (both administrative directives and legislation) that safeguard information technology and computer systems. The purpose of these directives is to force companies and organizations to protect their systems and information from cyberattacks, such as viruses, worms, Trojan horses, phishing, [http://eitbokwiki.org/Glossary#dos denial-of-service (DOS)] attacks, unauthorized access (stealing intellectual property or confidential information), and control system attacks.</p> |
| − | <p>Most regulations encourage the use of measures that are designed to prevent cyberattacks, including firewalls, antivirus software, intrusion detection and prevention systems, encryption, and login passwords. [[#Two|[2]]] For most industries, these measures are currently voluntary. There are three regulations that mandate healthcare organizations, financial institutions, and federal agencies: the 1996 Health Insurance Portability and Accountability Act (HIPAA), the 1999 Gramm-Leach-Bliley Act, and the 2002 Homeland Security Act | + | <p>Most regulations encourage the use of measures that are designed to prevent cyberattacks, including firewalls, antivirus software, intrusion detection and prevention systems, encryption, and login passwords. [[#Two|[2]]] For most industries, these measures are currently voluntary. There are three regulations that mandate healthcare organizations, financial institutions, and federal agencies protect their systems and information: the 1996 Health Insurance Portability and Accountability Act (HIPAA), the 1999 Gramm-Leach-Bliley Act, and the 2002 Homeland Security Act.</p> |
<p>Although the mandates only cover a few industries right now, many industry regulators are planning to include cybersecurity measures as a part of their standard regulatory examinations in the near future.</p> | <p>Although the mandates only cover a few industries right now, many industry regulators are planning to include cybersecurity measures as a part of their standard regulatory examinations in the near future.</p> | ||
<h5>State and Local Regulations</h5> | <h5>State and Local Regulations</h5> | ||
| − | <p>State governments have attempted to improve cybersecurity by increasing public visibility of firms with weak security. In 2003, California passed the Notice of Security Breach Act and California Assembly Bill 1958, which requires that any company maintaining personal information (name, social security number, | + | <p>State governments have attempted to improve cybersecurity by increasing public visibility of firms with weak security. In 2003, California passed the Notice of Security Breach Act and California Assembly Bill 1958, which requires that any company maintaining personal information (name, social security number, driver's license number, credit card number, or financial information) of California citizens that has a security breach must disclose the details of the event. In 2004, California passed California Assembly Bill 1950, which also applies to businesses that own or maintain personal information for California residents. This regulation dictates that businesses maintain a reasonable level of security and that these required security practices also extend to business partners. These security breach notification regulations punish firms for their cybersecurity failures while giving them the freedom to choose how to secure their systems. Many other states have passed similar laws. The problem with many of these laws is that they use the phrase "reasonable level of security." This phrase gives businesses too much room for interpretation. In addition, it is unclear whether organizations can actually be held accountable in court.</p> |
<h5>Privacy Laws and Regulations</h5> | <h5>Privacy Laws and Regulations</h5> | ||
<p>As mentioned above, the number of laws and regulations concerning data security are increasing over time. Privacy of customer transactions, whether a purchase or some other action, is considered the ethical responsibility of EIT by most governing bodies these days. This is a huge area of vulnerability for many enterprises, and many cybersecurity experts believe that litigation associated with privacy and data protection breaches are going to increase significantly in the near future.</p> | <p>As mentioned above, the number of laws and regulations concerning data security are increasing over time. Privacy of customer transactions, whether a purchase or some other action, is considered the ethical responsibility of EIT by most governing bodies these days. This is a huge area of vulnerability for many enterprises, and many cybersecurity experts believe that litigation associated with privacy and data protection breaches are going to increase significantly in the near future.</p> | ||
| − | <p> | + | <p>The International Association of Privacy Professionals (IAPP) glossary [[#Five|[5]]] defines privacy as: ''The appropriate use of personal information under the circumstances. What is appropriate will depend on context, law, and the individual's expectations; also, the right of an individual to control the collection, use and disclosure of information.'' Data protection is defined as the management of personal information.</p> |
<p>In the United States, ''privacy'' is the term that is used in policies, laws, and regulation. However, in the European Union and other countries, the term ''data protection'' often identifies privacy-related laws and regulations. Because of the different levels of regulation, international agreements have come into existence to manage compliance between countries and regions. The best known example being the US-EU Safe Harbor Principles, which streamline compliance for US companies attempting to meet the EU directive (95/46/EC) on protection of personal data.</p> | <p>In the United States, ''privacy'' is the term that is used in policies, laws, and regulation. However, in the European Union and other countries, the term ''data protection'' often identifies privacy-related laws and regulations. Because of the different levels of regulation, international agreements have come into existence to manage compliance between countries and regions. The best known example being the US-EU Safe Harbor Principles, which streamline compliance for US companies attempting to meet the EU directive (95/46/EC) on protection of personal data.</p> | ||
<p>The regulations associated with privacy are changing frequently, but the most common US laws are listed below.</p> | <p>The regulations associated with privacy are changing frequently, but the most common US laws are listed below.</p> | ||
<ul> | <ul> | ||
| − | <li>Healthcare providers, payers, clearinghouses, and similar organizations must comply with a set of government regulations such as the '''Health Insurance Portability and Accountability Act (HIPAA)''' and the '''Health Information Technology for Economic and Clinical Health Act (HITECH)'''. Over the years, enforcement for violations of both of these acts has been strengthened, and incentives have been put in place for the adoption of a secure electronic health records act | + | <li>Healthcare providers, payers, clearinghouses, and similar organizations must comply with a set of government regulations such as the '''Health Insurance Portability and Accountability Act (HIPAA)''' and the '''Health Information Technology for Economic and Clinical Health Act (HITECH)'''. Over the years, enforcement for violations of both of these acts has been strengthened, and incentives have been put in place for the adoption of a secure electronic health records act to protect personal health information.</li> |
<li>The '''Gramm-Leach-Bliley Act''' requires financial institutions that offer consumers financial products or services to safeguard sensitive client data.</li> | <li>The '''Gramm-Leach-Bliley Act''' requires financial institutions that offer consumers financial products or services to safeguard sensitive client data.</li> | ||
<li>The '''Payment Card Industry Data Security Standard (PCI-DSS)''' is a common set of security controls for protecting credit card information maintained by the PCI Security Standards Council. </li> | <li>The '''Payment Card Industry Data Security Standard (PCI-DSS)''' is a common set of security controls for protecting credit card information maintained by the PCI Security Standards Council. </li> | ||
| Line 74: | Line 81: | ||
<p>Data and privacy protection is important to most other countries and regulations have been uniformly increased around the world in the last few years:</p> | <p>Data and privacy protection is important to most other countries and regulations have been uniformly increased around the world in the last few years:</p> | ||
<ul> | <ul> | ||
| − | <li>The EU Data Protection Directive has been in place since 2011, and will be updated by the end of 2015 to Directive 95/46/EC. It will likely be one of the strongest sets of regulations to protect personal data in the world. Its primary goal is to bring all EU nations into alignment with respect to data protection and to raise every member | + | <li>The EU Data Protection Directive has been in place since 2011, and will be updated by the end of 2015 to Directive 95/46/EC. It will likely be one of the strongest sets of regulations to protect personal data in the world. Its primary goal is to bring all EU nations into alignment with respect to data protection and to raise every member country's standards, but it will also lay the groundwork for fining companies that do not comply with the new regulations. </li> |
<li>In 2014, Australia amended its Privacy Act to cover cloud and communications service providers and any other organizations that collect, process, or store personal information. As with many of the policies of other countries, not only does this amendment increase coverage of the law to global service providers, it enables the Australian Information Commissioner to monitor how companies comply with the policy, train their staff, and handle incidents and complaints.</li> | <li>In 2014, Australia amended its Privacy Act to cover cloud and communications service providers and any other organizations that collect, process, or store personal information. As with many of the policies of other countries, not only does this amendment increase coverage of the law to global service providers, it enables the Australian Information Commissioner to monitor how companies comply with the policy, train their staff, and handle incidents and complaints.</li> | ||
</ul> | </ul> | ||
<h4>More about Privacy and Data Protection</h4> | <h4>More about Privacy and Data Protection</h4> | ||
| − | <p>ISO/IEC 29100 [ | + | <p>ISO/IEC 29100 [[#Six|[6]]] identifies a number of what they call privacy principles that should be followed by all organizations that handle personal information:</p> |
<ul> | <ul> | ||
<li>The owner of the data must have consent and choice.</li> | <li>The owner of the data must have consent and choice.</li> | ||
| Line 87: | Line 94: | ||
<li>The organization should be able to ensure the accuracy and quality of the data.</li> | <li>The organization should be able to ensure the accuracy and quality of the data.</li> | ||
<li>The organization should demonstrate openness, transparency, and notice.</li> | <li>The organization should demonstrate openness, transparency, and notice.</li> | ||
| − | <li> The organization must be accountable.</li> | + | <li>The organization must be accountable.</li> |
<li>The organization needs to provide a reasonable amount of information security.</li> | <li>The organization needs to provide a reasonable amount of information security.</li> | ||
<li>The organization must be compliant with all privacy laws and regulations.</li> | <li>The organization must be compliant with all privacy laws and regulations.</li> | ||
</ul> | </ul> | ||
<h2>Establishing Enterprise-Wide Security</h2> | <h2>Establishing Enterprise-Wide Security</h2> | ||
| − | <p>Establishing an effective enterprise-wide security program is a critical and difficult task. It requires both careful assessment of the | + | <p>Establishing an effective enterprise-wide security program is a critical and difficult task. It requires both careful assessment of the enterprise's current situation, and an understanding of the organization's tolerance for risk. When those things are understood, a plan needs to be developed that covers all departments of the enterprise, as well as staff, vendors, and clients.</p> |
<h3>Enterprise-Level Vulnerability Assessment and Risk Tolerance</h3> | <h3>Enterprise-Level Vulnerability Assessment and Risk Tolerance</h3> | ||
| − | <div style="margin-left: 5em;"><p>'' | + | <div style="margin-left: 5em;"><p>''"Risk management is the process for identifying, analyzing, and communicating risk and accepting, avoiding, transferring, or controlling it to an acceptable level considering associated costs and benefits of any actions taken."'' ~ DHS Risk Lexicon, 2010 Edition</p></div> |
| − | <p>The area of vulnerability assessment and risk management is a key security competency for all enterprises. Risk management is more than just looking for vulnerabilities and then planning how to protect against them. There are two factors to consider. First, an organization could just shut down access to systems to control threats, but that likely does not meet the | + | <p>The area of vulnerability assessment and risk management is a key security competency for all enterprises. Risk management is more than just looking for vulnerabilities and then planning how to protect against them. There are two factors to consider. First, an organization could just shut down access to systems to control threats, but that likely does not meet the business's objectives and purpose for existence. For example, an online store has to provide access to its customers, and therefore has significant vulnerabilities by definition. Second, no institution can afford to be completely secure—if that is even possible. So, the risk management area is a balancing act; one that requires careful technical and cost/benefit analysis. </p> |
| − | <p>As such, listing an | + | <p>As such, listing an organization's vulnerabilities isn't good enough. Instead, it is critical to understand three other factors:</p> |
<ul> | <ul> | ||
<li>The potential cost in damages of each identified risk/threat (monetary, disruption of business, and loss of trust by customers, vendors, and other associates)</li> | <li>The potential cost in damages of each identified risk/threat (monetary, disruption of business, and loss of trust by customers, vendors, and other associates)</li> | ||
| Line 102: | Line 109: | ||
<li>The means and costs of protection (or mitigation) from the threat</li> | <li>The means and costs of protection (or mitigation) from the threat</li> | ||
</ul> | </ul> | ||
| − | <p>When you have thoroughly analyzed each threat, you can prioritize the | + | <p>When you have thoroughly analyzed each threat, you can prioritize the organization's efforts in protecting against or mitigating the threats.</p> |
| − | <p>Maybe just as important as performing a risk analysis is understanding the | + | <p>Maybe just as important as performing a risk analysis is understanding the organization's risk appetite (or risk aversion). The organization needs to understand how much risk it is willing to take, along with what types of damage are tolerable and intolerable. And, it is also critical to understand how much the organization can afford to protect against the threats. The organization's lawyers need to be engaged to identify and evaluate potential litigation risks.</p> |
| − | <p>Internal risk comes from three sources: the technology, the | + | <p>Internal risk comes from three sources: the technology, the organization's standard procedures, and the staff. All of these change constantly, so security planning and policy development is a non-stop process. The technology (software and hardware) is in a constant state of flux. Although often overlooked, the lack of carefully designed policies and operating procedures open up the enterprise to a number of threats and losses. Finally, an organization's own employees, consultants, and vendors are sources of exposure to breaches of security. According to analysts, insiders are responsible for more security violations and breaches than all the other sources of harm combined.</p> |
<h3>Developing a Security Plan and Program</h3> | <h3>Developing a Security Plan and Program</h3> | ||
<p>An effective security program requires a comprehensive security plan. The security plan should cover all security functions, areas, processes, policies, and procedures. It needs to be specific, clear, and well organized. The activities associated with developing a security plan and program are discussed below.</p> | <p>An effective security program requires a comprehensive security plan. The security plan should cover all security functions, areas, processes, policies, and procedures. It needs to be specific, clear, and well organized. The activities associated with developing a security plan and program are discussed below.</p> | ||
| − | [[File:SecurityPlanDevelopment.jpg|700px]] | + | <p>[[File:SecurityPlanDevelopment.jpg|700px]]<br />'''Figure 2. Security Plan Development'''</p> |
| − | < | + | |
<ul> | <ul> | ||
| − | <li>'''Define specific security goals''' | + | <li>'''Define specific security goals'''—The goal of this activity is to define or frame measurable EIT security goals. These goals must be in complete alignment with the enterprise's security objectives and with the risk tolerance of the organization. They also need to be specific, detailed, and measurable. Security goals should typically cover the following areas:<br /> |
<ul> | <ul> | ||
<li>Identifying, prioritizing, and addressing security gaps</li> | <li>Identifying, prioritizing, and addressing security gaps</li> | ||
| Line 116: | Line 122: | ||
<li>Law and regulation compliance</li> | <li>Law and regulation compliance</li> | ||
<li>Threat detection and response</li> | <li>Threat detection and response</li> | ||
| − | <li>Ongoing training and certification for security personnel </li> | + | <li>Ongoing training and certification for security personnel</li> |
| − | <li>Ongoing training of non-security personnel </li> | + | <li>Ongoing training of non-security personnel</li> |
<li>Continuous communication of program goals and potentials for exposures</li></ul></li> | <li>Continuous communication of program goals and potentials for exposures</li></ul></li> | ||
| − | <li>'''Categorize and assess information assets''' | + | <li>'''Categorize and assess information assets'''—This activity involves creating a comprehensive catalog of the organization's information assets. Each asset must be evaluated with respect to the value of its information to the organization and the cost of potential damage, whether that damage is due to a leak of information, actual damage to the systems or information, or a lack of availability for a short or extended period of time. In addition, the report should list the acceptable level of exposure to risk for the asset (loss, damage, unauthorized access) and the acceptable constraints that can be placed on the asset by the technology and policies designed to keep it secure.</li> |
| − | <li>'''Design alternative risk controls''' | + | <li>'''Design alternative risk controls'''—There are a number of alternatives available for protecting information assets. Each alternative has its strengths and weakness with respect to the enterprise's strategic and security goals. Each alternative also has its associated implementation and maintenance costs. By setting priorities and managing costs, the team can build an effective security architecture that contains routine electronic and process-based actions.</li> |
| − | <li>'''Implement and communicate selected controls''' | + | <li>'''Implement and communicate selected controls'''—Implementing the controls is often more than just installing security software and establishing security-related policies and procedures. Often general controls must be customized for the specific threat and information asset that they are meant to address. In addition, the controls need to be an integral part of the processes or assets that they support. Simply adding them on and expecting them to be used or followed is wishful thinking.</li> |
| − | <li>'''Test controls''' | + | <li>'''Test controls'''—The organization needs to create an assessment method to evaluate the effectiveness of the implemented controls. These come in the form of prearranged tests and reviews that ensure that the controls are protecting the assets as designed. The testing process should also assess whether policies and procedures are being followed by employees. If an organization doesn't test its controls, it can't certify to any governing body that its controls are effective. In some industries, being able to demonstrate that you are in compliance is critical. For other industries, it's just good business.</li> |
| − | <li>'''Detect and address security incidents''' | + | <li>'''Detect and address security incidents'''—Finally, an organization needs to detect when security breaches occur and deal with those breaches in an effective and efficient manner. We discuss this subject at length in the [[#SecurityIncident|Security Incident Response and Management]] section.</li> |
</ul> | </ul> | ||
| − | <h3> | + | <h3>Ongoing Security Planning Cycle</h3> |
| − | <div style="margin-left: 5em;"><p>" | + | <div style="margin-left: 5em;"><p>''"The risk management process is a continuous process for systematically addressing risk throughout the lifecycle of a system, product, or service."'' <br />~ ISO/IEC 16085:2006 Systems and software engineering—Lifecycle processes—Risk management, 3.12</p></div> |
| − | <p>Because security is now an aspect in the | + | <p>Because security is now an aspect in the lifecycle of all systems and services provided by an organization, the planning cycle is never over. Each time an organization fields a new capability, security must be considered. Even when maintaining an old system, security planning is involved. In addition, new threats and vulnerabilities are regularly identified, which requires an organization to constantly update their security capabilities. </p> |
| − | <p>The result is that organizations need to continuously take inventory, analyze, design, implement, and test their security | + | <p>The result is that organizations need to continuously take inventory, analyze, design, implement, and test their security system—and update the security plan accordingly. This ongoing process makes it essential to implement some kind of continuous improvement program that allows the organization to adapt to change quickly. This activity needs to be part of the overall security program.</p> |
<p>Here are some of the most often used processes.</p> | <p>Here are some of the most often used processes.</p> | ||
<ul> | <ul> | ||
| − | <li>'''[http://eitbokwiki.org/Glossary#pdca Deming | + | <li>'''[http://eitbokwiki.org/Glossary#pdca Deming cycle (plan, do, check, act)]'''—The PDCA process was incorporated into ISO/IEC 27001:2005 as the preferred risk management processes. This cycle contains four steps:<br /> |
<ol> | <ol> | ||
| − | <li>Plan | + | <li>''Plan'' phase—Design the ISMS by assessing information security risks and then selecting the appropriate controls for the risks.</li> |
| − | <li>Do | + | <li>''Do'' phase—Implement and use the security controls.</li> |
| − | <li>Check | + | <li>''Check'' phase—Review and evaluate the effectiveness and efficiency of the ISMS.</li> |
| − | <li>Act | + | <li>''Act'' phase—Modify the ISMS as necessary to improve effectiveness or efficiency. </li></ol></li> |
| − | <li>'''[http://eitbokwiki.org/Glossary#dmaic Six Sigmas DMAIC (define, measure, analyze, improve, control)]''' | + | <li>'''[http://eitbokwiki.org/Glossary#dmaic Six Sigmas DMAIC (define, measure, analyze, improve, control)]'''—This process refines the Deming cycle and is a data-driven quality strategy for improving a process that is often customized for use by security departments.</li> |
| − | <li>'''Information Security | + | <li>'''Information Security Forum's SOGP (Standard of Good Practice)'''—This document is a comprehensive, business-focused guide to managing information security risks. One of its sections discusses good practices with respect to security risk management. It also discusses the details of policies, standards, and procedures.</li> |
</ul> | </ul> | ||
<h2>Security Education and Training</h2> | <h2>Security Education and Training</h2> | ||
| − | <p>An essential part of any ISMS is the | + | <p>An essential part of any ISMS is the organization's security training program. These training programs often come in several different levels that match the sophistication and job function of employees. Security training is not just for those individuals actively involved in designing, implementing, and monitoring the security program—it is for all employees. A large number of security breaches are linked to employees' actions. Security threats cannot be totally addressed through security software and hardware—the human factor has to be addressed. Employees need to modify their standard operating behavior to reduce overall exposure to attacks—new security policies and procedures must be followed. As a result, security training programs need to be comprehensive and applied throughout the workforce. A good source of free online video training is at https://www.csiac.org/series/information-awareness-videos/. </p> |
<p>Security training programs need to instruct even low-level workers about their security responsibilities and teach them about information security processes and procedures that are appropriate for their job function. These programs are often referred to as ''security awareness programs''. Among other topics, security awareness programs cover how to avoid threats and attacks associated with:</p> | <p>Security training programs need to instruct even low-level workers about their security responsibilities and teach them about information security processes and procedures that are appropriate for their job function. These programs are often referred to as ''security awareness programs''. Among other topics, security awareness programs cover how to avoid threats and attacks associated with:</p> | ||
<ul> | <ul> | ||
| Line 150: | Line 156: | ||
<li>Lack of encryption</li> | <li>Lack of encryption</li> | ||
</ul> | </ul> | ||
| − | <p>Not only do employees need to be taught about the vulnerabilities associated with different tasks, such as reading email, but they also need to be given the tools to minimize the threats. A program should exist to keep the training and the tools up to date | + | <p>Not only do employees need to be taught about the vulnerabilities associated with different tasks, such as reading email, but they also need to be given the tools to minimize the threats. A program should exist to keep the training and the tools up to date as part of the ongoing organizational processes. In addition, non-technical employees need to be motivated to follow the enterprise's security procedures; otherwise, they will not do so.</p> |
<p>Training for more technical individuals needs to address the technical aspects of preventing security breaches. For example, security training for the programming staff should include information about how to conduct a code review to identify vulnerabilities in the code.</p> | <p>Training for more technical individuals needs to address the technical aspects of preventing security breaches. For example, security training for the programming staff should include information about how to conduct a code review to identify vulnerabilities in the code.</p> | ||
<p>The training for the security team needs to be the most comprehensive, and it also needs to be continuous. As attacks become more sophisticated, the training level of the security staff needs to keep up. The constant change in every area of security is what drives specialization. The advanced training classes often focus on only one area, such as data security or defense against denial of service attacks.</p> | <p>The training for the security team needs to be the most comprehensive, and it also needs to be continuous. As attacks become more sophisticated, the training level of the security staff needs to keep up. The constant change in every area of security is what drives specialization. The advanced training classes often focus on only one area, such as data security or defense against denial of service attacks.</p> | ||
| − | <p>The training function needs to be accountable and reviews need to be conducted regularly. Measure | + | <p>The training function needs to be accountable and reviews need to be conducted regularly. Measure the effectiveness of the training from both a programmatic and individual perspective. When the effectiveness is found to be lacking, updates need to be made immediately.</p> |
<h2>Assets, Risks, and Threat Protection</h2> | <h2>Assets, Risks, and Threat Protection</h2> | ||
<p>When goals are defined, it is time to take inventory. There are large numbers of EIT assets that need to be categorized and evaluated for potential risk. Often the EIT security arena is divided into facilities, computer hardware, telecommunications, networking, software, and information (data), better enabling the organization to identify each asset and evaluate the potential of the asset as a security risk. Individuals with security risk identification skills specific to each area need to be involved in the activity.</p> | <p>When goals are defined, it is time to take inventory. There are large numbers of EIT assets that need to be categorized and evaluated for potential risk. Often the EIT security arena is divided into facilities, computer hardware, telecommunications, networking, software, and information (data), better enabling the organization to identify each asset and evaluate the potential of the asset as a security risk. Individuals with security risk identification skills specific to each area need to be involved in the activity.</p> | ||
<p>When each asset is identified, the team needs to enumerate the risks associated with the asset. Some assets may only have a couple of risks or potential threats associated with them, while others may have hundreds of potential risks. For each risk, the team needs to evaluate the cost of a security breach for that asset in concert with the asset owner and stakeholders.</p> | <p>When each asset is identified, the team needs to enumerate the risks associated with the asset. Some assets may only have a couple of risks or potential threats associated with them, while others may have hundreds of potential risks. For each risk, the team needs to evaluate the cost of a security breach for that asset in concert with the asset owner and stakeholders.</p> | ||
<h3>Facility Security Evaluation</h3> | <h3>Facility Security Evaluation</h3> | ||
| − | <p>Facility security is part of most | + | <p>Facility security is part of most companies' plans and this has been the case for years. These plans are usually ''perimeter based''. Using this mindset, the organization can consider everything in a defined area as one large asset. You might think that a standard facilities security plan would be good enough, but an alarming number of cyberattacks occur inside the defined security perimeter of a standard physical security plan. </p> |
| − | <p>To counter these attacks, facility security plans | + | <p>To counter these attacks, facility security plans need to be changed from being perimeter based to being ''area based''. All assets within an area, even the non-tangible information assets, need to be protected. Therefore, the physical security planning process needs to be fully integrated with those steps that protect the information assets themselves. The facility security plan needs to:</p> |
<ul> | <ul> | ||
<li>Clearly identify and define protected areas; define a layered defense.</li> | <li>Clearly identify and define protected areas; define a layered defense.</li> | ||
| Line 168: | Line 174: | ||
<li>Clearly define appropriate responses to any identified security breaches.</li> | <li>Clearly define appropriate responses to any identified security breaches.</li> | ||
</ul> | </ul> | ||
| − | <p>Asset identification processes and the security plan need to take into account not only threats associated with unauthorized entry of an individual, but also damage caused by man-made or natural disasters. All of these threats need to be identified and safeguards/techniques need to be identified to protect against them (see the [http://eitbokwiki.org/Disaster_Preparedness Disaster Preparedness | + | <p>Asset identification processes and the security plan need to take into account not only threats associated with unauthorized entry of an individual, but also damage caused by man-made or natural disasters. All of these threats need to be identified and safeguards/techniques need to be identified to protect against them (see the [http://eitbokwiki.org/Disaster_Preparedness Disaster Preparedness] chapter). </p> |
<h3>Telecommunications </h3> | <h3>Telecommunications </h3> | ||
<p>Telecommunications networks and other pieces of infrastructure are rapidly being assimilated into the Internet. Today, systems such as electrical grids and traffic systems are now accessible to users, regardless of their location, with a few clicks of a mouse. These tremendous capabilities are not without consequences. For example, a hacker can launch attacks capable of denying voice service to cellular telecommunications networks in major cities, or use telecommunications for turning off utilities in the smart grid. In times of emergency, when such networks are essential in saving lives, such attacks can be extremely dangerous.</p> | <p>Telecommunications networks and other pieces of infrastructure are rapidly being assimilated into the Internet. Today, systems such as electrical grids and traffic systems are now accessible to users, regardless of their location, with a few clicks of a mouse. These tremendous capabilities are not without consequences. For example, a hacker can launch attacks capable of denying voice service to cellular telecommunications networks in major cities, or use telecommunications for turning off utilities in the smart grid. In times of emergency, when such networks are essential in saving lives, such attacks can be extremely dangerous.</p> | ||
<p>When evaluating assets, and looking for risks and mitigation techniques, the telecommunications team needs to consider the following security techniques:</p> | <p>When evaluating assets, and looking for risks and mitigation techniques, the telecommunications team needs to consider the following security techniques:</p> | ||
<ul> | <ul> | ||
| − | <li>'''Authorization''' | + | <li>'''Authorization'''—Requiring authorization to help prevent unauthorized interceptors from accessing telecommunications in an intelligible form while still delivering content to the intended recipient</li> |
| − | <li>'''Cryptosecurity''' | + | <li>'''Cryptosecurity'''—Communications security that results from the use of cryptosystems to ensure message confidentiality and authenticity</li> |
| − | <li>'''Emission security''' | + | <li>'''Emission security'''—The protection to deny unauthorized personnel information due to interception and analysis of emanations from cryptographic equipment, information systems, and telecommunication systems</li> |
| − | <li>'''Transmission security''' | + | <li>'''Transmission security'''—The security that protects transmission from interception and exploitation by means other than cryptanalysis, such as frequency hopping and spread spectrum</li> |
| − | <li>'''Physical security''' | + | <li>'''Physical security'''—All physical measures necessary to safeguard classified equipment, material, and documents from access</li> |
</ul> | </ul> | ||
<h3>Network and Internet Security</h3> | <h3>Network and Internet Security</h3> | ||
<p>Although similar to telecommunications security, network and Internet security present additional assets and risks. The open nature of the Internet puts all users at risk of attack. It also puts all servers, computers, and other devices that interact with the Internet at risk. As a result, carefully documenting all network settings, proxies, licenses, VPNs, and the assets on each LAN or network segment is critical. Each must be examined for vulnerability.</p> | <p>Although similar to telecommunications security, network and Internet security present additional assets and risks. The open nature of the Internet puts all users at risk of attack. It also puts all servers, computers, and other devices that interact with the Internet at risk. As a result, carefully documenting all network settings, proxies, licenses, VPNs, and the assets on each LAN or network segment is critical. Each must be examined for vulnerability.</p> | ||
<p>Understanding where all the assets are and how open they are to network traffic is difficult, but necessary to assess the true threat risk for the asset. The team needs to be able to understand the potential risks of denial of service or phishing from any given device on not only that device, but the rest of the assets on that part of the network.</p> | <p>Understanding where all the assets are and how open they are to network traffic is difficult, but necessary to assess the true threat risk for the asset. The team needs to be able to understand the potential risks of denial of service or phishing from any given device on not only that device, but the rest of the assets on that part of the network.</p> | ||
| − | <p>In addition, it is important to understand the needs | + | <p>In addition, it is important to understand the needs of users for network and Internet use. If users don't need to have access to the Internet, many issues become irrelevant. Some enterprises set up separate network access routes for employees to use so that access from a secure intranet is impossible.</p> |
<h3>Computers and Mobile Devices</h3> | <h3>Computers and Mobile Devices</h3> | ||
<p>Each computational device needs to be evaluated. Although we most often think of threats associated with software, hackers can attack the devices themselves either via theft, electronic intrusion, and physical damage. The security plan needs to protect hardware and other devices from all these kinds of threats. </p> | <p>Each computational device needs to be evaluated. Although we most often think of threats associated with software, hackers can attack the devices themselves either via theft, electronic intrusion, and physical damage. The security plan needs to protect hardware and other devices from all these kinds of threats. </p> | ||
| Line 200: | Line 206: | ||
<p>Application security includes those measures taken within the code to prevent security gaps whether due to flaws in the design, implementation, deployment, or maintenance processes associated with the application.</p> | <p>Application security includes those measures taken within the code to prevent security gaps whether due to flaws in the design, implementation, deployment, or maintenance processes associated with the application.</p> | ||
<p>As with all the other areas, it is important to take inventory of your software assets so that you know the potential threats due to the functionality of the systems. As organizations field software, the security of the software asset is not complete without consideration of the software itself, the host, connected devices, and the network.</p> | <p>As with all the other areas, it is important to take inventory of your software assets so that you know the potential threats due to the functionality of the systems. As organizations field software, the security of the software asset is not complete without consideration of the software itself, the host, connected devices, and the network.</p> | ||
| − | <p>Through the years, many techniques and development | + | <p>Through the years, many techniques and development lifecycles (e.g., Microsoft SDL, OWAP CLASP, Cigital touchpoints) have been developed (see ''Improving Web Application Security'' [[#Four|[4]]]) that include patterns and techniques to help identify the types of attacks to which an application is vulnerable. There are many categories of attacks on apps that have been identified, including:</p> |
<ul> | <ul> | ||
<li>Software tampering (changing, substituting, or extending code)</li> | <li>Software tampering (changing, substituting, or extending code)</li> | ||
| Line 213: | Line 219: | ||
<p>There are several strategies that programmers can use that can enhance mobile app security, such as using stronger authentication and authorization, tying processes to user IDs, and ensuring transport-layer security. There are many sources available that discuss how to build security into applications. [[#Eight|[8]]]</p> | <p>There are several strategies that programmers can use that can enhance mobile app security, such as using stronger authentication and authorization, tying processes to user IDs, and ensuring transport-layer security. There are many sources available that discuss how to build security into applications. [[#Eight|[8]]]</p> | ||
<h3>Data Security</h3> | <h3>Data Security</h3> | ||
| − | <p>Although related to all the other levels of assets, a security plan needs to consider some individual data items as assets themselves. It | + | <p>Although related to all the other levels of assets, a security plan needs to consider some individual data items as assets themselves. It doesn't matter how the hacker gets into the database (hardware, software, network, or physical access), the fact that sensitive information, such as social security, telephone, and credit card numbers are accessed is extremely damaging to the enterprise.</p> |
<p>The data security team needs to understand which elements in the database are particularly sensitive or critical for operations. There are a whole host of means by which data systems can be compromised and each of these potential threats needs to be analyzed and mitigated.</p> | <p>The data security team needs to understand which elements in the database are particularly sensitive or critical for operations. There are a whole host of means by which data systems can be compromised and each of these potential threats needs to be analyzed and mitigated.</p> | ||
<ul> | <ul> | ||
| Line 231: | Line 237: | ||
<p>Effective security policies that are followed throughout the enterprise are another essential component of the security program. These policies need to be carefully designed, well-communicated and monitored, and must cover a number of areas:</p> | <p>Effective security policies that are followed throughout the enterprise are another essential component of the security program. These policies need to be carefully designed, well-communicated and monitored, and must cover a number of areas:</p> | ||
<ul> | <ul> | ||
| − | <li>'''Access and overreaching policies''' | + | <li>'''Access and overreaching policies'''—These policies regulate email, password setting, acceptable use of resources, encryption key usage, and even security response and disaster-recovery processes.</li> |
| − | <li>'''Computer and server security policies''' | + | <li>'''Computer and server security policies'''—This area of policies covers issues such as server security, workstation security, software installation, facilities security, information logging, database access and credentials, and technology disposal.</li> |
| − | <li>'''Network security policies''' | + | <li>'''Network security policies'''—These policies cover just about any risk associated with the networks that can be regulated by a policy, such as remote access, router and switch security, and wireless communication. </li> |
| − | <li>'''Application security policies''' | + | <li>'''Application security policies'''—These policies cover topics such as access and control, the delineation of responsibilities for access to files and data, web application security, mobile device app security, and security tools. These policies might also regulate the use of open-source software and third-party code, and require that such code be contained in a secure software repository. In some organizations, these policies require cryptoroutines and scans that test for vulnerabilities with in the code.</li> |
</ul> | </ul> | ||
<p>The area of security policies is a difficult one for most CIOs. A lot of help is available for forming security policies that protect the organization; however, getting a policy to be followed throughout the enterprise can be extremely difficult. Compliance with security policies can be distressingly low in certain areas, such as policies associated with mobile device use and personal browsing on corporate workstations. This trend makes training of and frequent communication to all employees an essential part of policy enforcement, as is motivating the average employee to follow the rules.</p> | <p>The area of security policies is a difficult one for most CIOs. A lot of help is available for forming security policies that protect the organization; however, getting a policy to be followed throughout the enterprise can be extremely difficult. Compliance with security policies can be distressingly low in certain areas, such as policies associated with mobile device use and personal browsing on corporate workstations. This trend makes training of and frequent communication to all employees an essential part of policy enforcement, as is motivating the average employee to follow the rules.</p> | ||
<h3>Security Architecture and Models </h3> | <h3>Security Architecture and Models </h3> | ||
| − | <p>A ''security model'' is a representation of the | + | <p>A ''security model'' is a representation of the enterprise's rules or policies about security, especially data access. The models don't tell an organization specifically how to design their security system. Instead, models provide a perspective on how to look at security for a system. A particular architecture might use several security models. There are many different security models and we cover a few here.</p> |
<ul> | <ul> | ||
| − | <li>'''State | + | <li>'''State machine model'''—To verify the security of a system, the state of the system is used. Therefore, all current permissions and accesses to information systems are captured. Systems that employ this model are in a secure state all the time.</li> |
| − | <li>'''Bell-LaPadula model''' | + | <li>'''Bell-LaPadula model'''—This model was developed to address the leakage of classified information. It was the first rigorous model of a multilevel security policy used to define a ''secure state'' machine, and modes of access to information. In this model, users with different "clearances" have access to different levels of information.</li> |
| − | <li>'''Biba model''' | + | <li>'''Biba model'''—This model is similar to the Bell-LaPadula model. It addresses the integrity of data that is threatened when users at lower security levels are able to write to objects at higher security levels.</li> |
| − | <li>'''Clark-Wilson model''' | + | <li>'''Clark-Wilson model'''—This model focuses on preventing authorized users from making unauthorized modifications to data, or committing fraud and errors within commercial applications. Rather than confidentiality, this model protects the integrity of the data.</li> |
| − | <li>'''Information | + | <li>'''Information flow model'''—This type of model looks for insecure information flow. Insecure information flow can occur at the same level or between different levels until a restricted operation is attempted. </li> |
| − | <li>''' | + | <li>'''Non-interference model'''—This model ensures that any actions that take place at a higher security level do not affect or interfere with actions at a lower level. This model doesn't care about the flow of information, but what the user knows about the state of the system, especially about actions taken at a higher level.</li> |
| − | <li>'''Brewer and Nash model''' | + | <li>'''Brewer and Nash model'''—This model is designed to provide access controls that can change dynamically depending on the user's previous actions. It prevents access to data that might be considered a conflict of interest. This model is used often in financial institutions.</li> |
| − | <li>'''Graham-Denning model''' | + | <li>'''Graham-Denning model'''—This model creates rights for users that are associated with operations that can be executed on objects. In essence, it defines the "rights" that a user has to perform actions.</li> |
| − | <li>'''Harrison-Ruzzo-Ullman model''' | + | <li>'''Harrison-Ruzzo-Ullman model'''—This model specifies how access rights can be changed. It also specifies how objects can be created and deleted.</li> |
</ul> | </ul> | ||
<h3>Classification for Levels of Access</h3> | <h3>Classification for Levels of Access</h3> | ||
| − | <p>The area of access management is complex and can generate debates on specific details during the implementation of who can see what data and when. The ''how'' is often dictated by identity management systems already in place within the enterprise | + | <p>The area of access management is complex and can generate debates on specific details during the implementation of who can see what data and when. The ''how'' is often dictated by identity management systems already in place within the enterprise. However, these identity management systems often have the flexibility to design multiple discretionary frameworks, such as role-based and user-based security models. Access control policies need to take all forms of access control into consideration.</p> |
| − | <p>One of the first functions of developing a security model is to determine the categories of users needed to ensure data | + | <p>One of the first functions of developing a security model is to determine the categories of users needed to ensure data is accessed on an as-needed basis. Role-based access control is a common method used for access control. Here are some of the most common roles:</p> |
<ul> | <ul> | ||
| − | <li>'''Administrators''' | + | <li>'''Administrators'''—Administrators' capabilities can range from database administrators to file or storage administrators. However, software developers and network administrators may often have cross-domain responsibilities that require a high level of access. This level includes access to create, modify, and delete data, files, and configuration settings. </li> |
| − | <li>'''Power/super users''' | + | <li>'''Power/super users'''—Power/super users is an optional level of security access that provides highly knowledgeable functional users with the authorization to access more service functions that their job function requires. This level adds mentoring or coaching to the duties of this role. Generally this type of user has access to all areas of a service if they are responsible for assisting or training others in that service. Another term for this type of user is ''functional lead''. </li> |
| − | <li>'''Primary functional users''' | + | <li>'''Primary functional users'''—Primary functional users have application and service authentication and access rights allowing them to perform the business functions needed to complete their daily tasks. These are end users that add and update records with the highest frequency of any user group. </li> |
| − | <li>'''Secondary (casual) user types''' | + | <li>'''Secondary (casual) user types'''—Secondary or casual users are roles such as auditors and managers, or those given user IDs for one-time or temporary access, such as contractors or consultants. These roles usually have read-only access or may have access to very limited functions, such a reporting or expense submission.</li> |
| − | <li>'''Anonymous/read-only users''' | + | <li>'''Anonymous/read-only users'''—A final category is anonymous access to public information or read-only employee information, for users who need access to data, such as benefit or corporate reporting information. </li> |
</ul> | </ul> | ||
<h2>Implementing and Maintaining Selected Security Controls</h2> | <h2>Implementing and Maintaining Selected Security Controls</h2> | ||
| − | <p>After the security controls are designed, they need to be put into operation. Implementing security controls is just like constructing and implementing any other EIT solution. The implementation has to be carefully planned and integrated into already existing hardware, software, processes, polices, and procedures. Luckily, it is usually the case that you can implement just one mitigation technique at a time, which means an organization can roll out a security plan in pieces, according to the priorities it has established. For example, one month an organization can implement new password policies and procedures. The next month, it | + | <p>After the security controls are designed, they need to be put into operation. Implementing security controls is just like constructing and implementing any other EIT solution. The implementation has to be carefully planned and integrated into already existing hardware, software, processes, polices, and procedures. Luckily, it is usually the case that you can implement just one mitigation technique at a time, which means an organization can roll out a security plan in pieces, according to the priorities it has established. For example, one month an organization can implement new password policies and procedures. The next month, it upgrades all servers to a new version of the OS that contains new security features. And, one would expect that the security testing function is continuously improving over time.</p> |
<p>Each EIT department plays a role in integrating, monitoring, and maintaining the security plan.</p> | <p>Each EIT department plays a role in integrating, monitoring, and maintaining the security plan.</p> | ||
<ul> | <ul> | ||
| − | <li>'''System administration''' | + | <li>'''System administration'''—This department usually rolls out new versions of the operating systems and software, and ensures that the operational environments are configured in accordance with approved baselines and that all security updates are installed on devices in a timely manner.</li> |
| − | <li>'''Network services''' | + | <li>'''Network services'''—It is their role to ensure that the network set up follows the security plan. Network services also need to monitor the network for any illegal traffic.</li> |
| − | <li>'''Customer service and technical support''' | + | <li>'''Customer service and technical support'''—This group's role is to help individuals follow the security policies and procedures. Often this includes teaching both in classroom base sessions as well as individual handholding.</li> |
| − | <li>'''Data administration and knowledge management''' | + | <li>'''Data administration and knowledge management'''—Data and knowledge administrators need to make sure that all data security controls are implemented on all databases and knowledge bases. In addition, they need to monitor databases constantly for any form of breach.</li> |
| − | <li>'''Systems security analysis''' | + | <li>'''Systems security analysis'''—Systems security analysis is an ongoing concern. This group is in charge of detecting security breaches. </li> |
</ul> | </ul> | ||
<h2>Security Monitoring, Accountability, and Testing </h2> | <h2>Security Monitoring, Accountability, and Testing </h2> | ||
| − | <p>Testing security measures is an essential part of a security plan. You cannot verify that the plan is working unless you test whether the security measures (software, policies, and procedures) are working as the plan specifies. Unfortunately, even if the security system tests run without finding flaws, there is no guarantee that vulnerabilities | + | <p>Testing security measures is an essential part of a security plan. You cannot verify that the plan is working unless you test whether the security measures (software, policies, and procedures) are working as the plan specifies. Unfortunately, even if the security system tests run without finding flaws, there is no guarantee that it is free of vulnerabilities. It is nearly impossible to test for all possible vulnerabilities; hackers seem to find new ones every day.</p> |
<p>To test a security system, you have to design the tests to cover the [http://eitbokwiki.org/Glossary#ciatriad CIA triad (confidentiality, integrity, availability)]. In addition, the tests specifically need to cover authentication, authorization, and non-repudiation. Tests must cover the different areas of vulnerabilities, such as network security, system software security, client-side application security, and server-side security. </p> | <p>To test a security system, you have to design the tests to cover the [http://eitbokwiki.org/Glossary#ciatriad CIA triad (confidentiality, integrity, availability)]. In addition, the tests specifically need to cover authentication, authorization, and non-repudiation. Tests must cover the different areas of vulnerabilities, such as network security, system software security, client-side application security, and server-side security. </p> | ||
| − | <p>Testing and then forgetting | + | <p>Testing and then forgetting doesn't work in security. The plan should provide required frequencies for conducting different tests on the system and for reporting the results. The security team needs to monitor the system to make sure that security measures (such as network settings) have not been changed and that vulnerabilities have not appeared. This is an ongoing maintenance issue, not a one-time verification of a system.</p> |
<h3>Security Accountability</h3> | <h3>Security Accountability</h3> | ||
| − | <p>A major component of every security system is accountability. In this arena, ''accountability'' is the ability to trace all | + | <p>A major component of every security system is accountability. In this arena, ''accountability'' is the ability to trace all the actions performed on a device, within a process, or by a user. Techniques such as unique user identification (UUID) and authentication strongly support accountability. </p> |
<p>Accountability is necessary to ensure that any attempted or committed security violation can be traced to the device on which it occurred and to the individual that committed the breach. Accountability enables the EIT organization to find those individuals that need to be held responsible for the damage. Without accountability, security monitoring has little purpose.</p> | <p>Accountability is necessary to ensure that any attempted or committed security violation can be traced to the device on which it occurred and to the individual that committed the breach. Accountability enables the EIT organization to find those individuals that need to be held responsible for the damage. Without accountability, security monitoring has little purpose.</p> | ||
<h3>Vulnerability Testing Categories and Levels</h3> | <h3>Vulnerability Testing Categories and Levels</h3> | ||
| − | <p>As with all testing, the | + | <p>As with all testing, the three standard categories of testing also apply to security: white box, gray box, and black box. ''White box testing'' is done with full knowledge of the system being tested—you know what you are looking for. ''Gray box testing'' is done with partial knowledge of the system. ''Black box testing'' is done with no knowledge of the system being tested, and testing for penetration is primarily black box testing. There are a number of testing phases or levels that mature security tests have. Some of them are automated and some are done by hand. Here are some of the most common levels:</p> |
<ul> | <ul> | ||
| − | <li>'''Discovery''' | + | <li>'''Discovery'''—This phase identifies information systems and determines the technologies that are in use. It also determines, hosts, ports, and application entry points. A discovery process might find deprecated versions of software or firmware that are prone to attack, or it might find newly opened ports or entry points.</li> |
| − | <li>'''Vulnerability scan''' | + | <li>'''Vulnerability scan'''—This scan identifies known security issues with automated tools that look for specific conditions or situations that are known to indicate vulnerabilities. These scans can be run with or without credentials (which helps determine what parts of the enterprise can be accessed without an authorized login). </li> |
| − | <li>'''Vulnerability scans''' | + | <li>'''Vulnerability scans'''—These scans can be manual or automated, and typically test for secure transmissions protocols, authentication vulnerabilities, session management vulnerabilities such as cookie scope and session termination timeouts, authorization vulnerabilities, data or file input vulnerabilities, and error-handling defects, among others. </li> |
| − | <li>'''Penetration tests''' | + | <li>'''Penetration tests'''—These tests simulate an attack by a malicious hacker. Typically, these tests are performed by individuals who use complicated methodologies and problem-solving skills to penetrate an organization's security measures. These tests go beyond what automated tools are capable of doing.</li> |
| − | <li>'''Security review''' | + | <li>'''Security review'''—This review verifies that the enterprise's policies and procedures are in place and are being used systematically throughout the organization. In addition, the reviewers need to verify that any required industry and governmental standards are being applied to each information system component.</li> |
</ul> | </ul> | ||
<p>When the series of tests is done, the team typically performs a series of risk assessments and audits. The team considers each finding and determines the seriousness of the vulnerability. The team might determine that in this context, an identified vulnerability is actually a false positive. At times, the team might even manually reproduce a vulnerability that was found with an automated system to verify the exposure. The resulting assessment report often lists the vulnerabilities by their seriousness and potential cost to the enterprise.</p> | <p>When the series of tests is done, the team typically performs a series of risk assessments and audits. The team considers each finding and determines the seriousness of the vulnerability. The team might determine that in this context, an identified vulnerability is actually a false positive. At times, the team might even manually reproduce a vulnerability that was found with an automated system to verify the exposure. The resulting assessment report often lists the vulnerabilities by their seriousness and potential cost to the enterprise.</p> | ||
<div id="SecurityIncident"></div><h2>Security Incident Response and Management</h2> | <div id="SecurityIncident"></div><h2>Security Incident Response and Management</h2> | ||
<p>Managing security incidents or events is just a special case of computer system or network management. The goal is to have a well-understood and predictable response to potentially damaging intrusions or events. There are a number of recommended incident management procedures that one can find with a simple search, but most are minor variations on a particular theme. In the discussion below, we have included the activities that are generally recommended and commonly included in an incident response plan. [[#Fifteen|[15]]]</p> | <p>Managing security incidents or events is just a special case of computer system or network management. The goal is to have a well-understood and predictable response to potentially damaging intrusions or events. There are a number of recommended incident management procedures that one can find with a simple search, but most are minor variations on a particular theme. In the discussion below, we have included the activities that are generally recommended and commonly included in an incident response plan. [[#Fifteen|[15]]]</p> | ||
| − | [[File:DetectEvent.jpg|700px]] | + | <p>[[File:DetectEvent.jpg|700px]]<br />'''Figure 3. Incident Response Plan'''</p> |
| − | < | + | |
<h3>Detecting the Event</h3> | <h3>Detecting the Event</h3> | ||
| − | <p>Detecting a security breach is often harder than it seems. Most companies | + | <p>Detecting a security breach is often harder than it seems. Most companies don't know that they have been breached. The ones that do often find out days, weeks, or even months after the attack—just read about Target and their experience. They found out about the attack about a month after it occurred, despite their high-end antihacking operation. Event detection is difficult for two reasons. First, detection has become a far more complex task due to the increased size of attack surface, as systems have gotten more highly integrated and complex. Second, many companies are not using state-of-the-art detection software and programs.</p> |
| − | <p>As a result, detection is very difficult and detection technology is usually lagging behind the level of the most advanced hackers. In addition, most enterprises use detection methods that are only partially effective, at best. They | + | <p>As a result, detection is very difficult and detection technology is usually lagging behind the level of the most advanced hackers. In addition, most enterprises use detection methods that are only partially effective, at best. They don't keep up with the state-of-the-art detection software. Also, most enterprises do not perform a thorough analysis of the potential avenues of attack. If you don't understand where the attacks can occur, you can't put monitors in to detect them.</p> |
| − | <p>There are two great examples of this. First, in the case of the attacks on Target, there were point-of-sale terminals that were not being monitored as a point of attack. Second, in gas station skimmer attacks, credit card numbers are stolen by inserting a hardware device into the gas pump. The device actually powers itself with the | + | <p>There are two great examples of this. First, in the case of the attacks on Target, there were point-of-sale terminals that were not being monitored as a point of attack. Second, in gas station skimmer attacks, credit card numbers are stolen by inserting a hardware device into the gas pump. The device actually powers itself with the pump's own electricity. The designer of the pump never considered this point of entry for an attack.</p> |
| − | <p>Over the last several years, detection methods have gone from signature or rule based to being behavior and analytics based. Most of the damage is done after the initial breach of the perimeter security, such as the corporate firewalls. So, it is now critical for organizations to have technology that can detect breaches (foreign activity) that occur behind the firewall. And these breaches often last for hours. There is significant evidence that one of | + | <p>Over the last several years, detection methods have gone from signature or rule based to being behavior and analytics based. Most of the damage is done after the initial breach of the perimeter security, such as the corporate firewalls. So, it is now critical for organizations to have technology that can detect breaches (foreign activity) that occur behind the firewall. And these breaches often last for hours. There is significant evidence that one of China's cyberespionage units attacked 141 victim companies and stole multiple terabytes of data in attacks that lasted at least a year! </p> |
| − | <h3>Assessing/Analyzing the Event</h3> | + | <h3>Assessing/Analyzing the Event</h3> |
<p>When the event has been detected, the security team needs to assess the event quickly to keep the damage from spreading. The team needs to determine whether the event is malicious or not and what type of event is it. It might be a denial of service, an access attack, or a reconnaissance attack, for example.</p> | <p>When the event has been detected, the security team needs to assess the event quickly to keep the damage from spreading. The team needs to determine whether the event is malicious or not and what type of event is it. It might be a denial of service, an access attack, or a reconnaissance attack, for example.</p> | ||
| − | <p>The team needs to determine as best as possible how the breach occurred. The attack could have come from outside the organization or from within. It could have been a piece of malware or | + | <p>The team needs to determine as best as possible how the breach occurred. The attack could have come from outside the organization or from within. It could have been a piece of malware or an Internet worm running on one of the internal systems. They need to determine the particular system that was breached.</p> |
<p>A quick assessment of what has been affected needs to be made to determine what data, software, or hardware has been breached or damaged. The initial assessment also needs to determine the severity of the attack. It could be just a nuisance, or it could be a serious threat to the business, staff, vendors, or customers. </p> | <p>A quick assessment of what has been affected needs to be made to determine what data, software, or hardware has been breached or damaged. The initial assessment also needs to determine the severity of the attack. It could be just a nuisance, or it could be a serious threat to the business, staff, vendors, or customers. </p> | ||
<h3>Containing the Damage</h3> | <h3>Containing the Damage</h3> | ||
| − | <p>After a basic assessment has been made, | + | <p>After a basic assessment has been made, you need to take steps to contain the damage. What systems need to be brought down? Do workstations need to be confiscated? Does the organization's connection to the Internet need to be broken? Can you just limit third-party activity? Do you need to shut down wireless networks? Do you need to change passwords throughout the enterprise as fast as possible?</p> |
<h3>Collecting and Protecting Evidence</h3> | <h3>Collecting and Protecting Evidence</h3> | ||
| − | <p>If the event is malicious, especially if it causes significant damage, it is critical to save the evidence. Obviously, the team needs to identify the type and severity of the compromise, and where the attack came from. The team also needs to save critical data to be used for | + | <p>If the event is malicious, especially if it causes significant damage, it is critical to save the evidence. Obviously, the team needs to identify the type and severity of the compromise, and where the attack came from. The team also needs to save critical data to be used for forensic purposes.</p> |
| − | <p>The | + | <p>The organization's team might not have the capability to collect and protect the evidence; however, there are a number of companies that specialize in helping organizations with this process.</p> |
<p>It is important to note that collecting and protecting the evidence usually slows down the recovery process; however, for a significant security breach, there is no question that it is the right thing to do.</p> | <p>It is important to note that collecting and protecting the evidence usually slows down the recovery process; however, for a significant security breach, there is no question that it is the right thing to do.</p> | ||
<h3>Communicating to Those Affected</h3> | <h3>Communicating to Those Affected</h3> | ||
<p>It is critically important to communicate to those individuals who are affected by the event. This might mean sending an email to an employee because there is malware on their workstation. It might mean sending out email or letters to thousands of customers, because their credit card data has been stolen. And in most cases, it is critical to notify management. Incident response plans should include a table that indicates who should be notified given the type and complexity of the security incident. </p> | <p>It is critically important to communicate to those individuals who are affected by the event. This might mean sending an email to an employee because there is malware on their workstation. It might mean sending out email or letters to thousands of customers, because their credit card data has been stolen. And in most cases, it is critical to notify management. Incident response plans should include a table that indicates who should be notified given the type and complexity of the security incident. </p> | ||
<h3>Notifying Appropriate Agencies</h3> | <h3>Notifying Appropriate Agencies</h3> | ||
| − | <p>If the event is serious, the appropriate agencies need to be informed of the event. Contacting the | + | <p>If the event is serious, the appropriate agencies need to be informed of the event. Contacting the organization's lawyer is likely the best first step. Determining the correct law enforcement agency to call is not always straightforward. In the USA, the FBI and Homeland Security are obvious choices for a foreign attack. For each country, the agencies are different, and it is important to determine which agencies the security team should call under particular conditions. All appropriate contact information needs to be part of the security plan. </p> |
<p>Many organizations now have insurance coverage for cyberattacks. The corporate lawyer should know about that coverage. </p> | <p>Many organizations now have insurance coverage for cyberattacks. The corporate lawyer should know about that coverage. </p> | ||
<h3>Recovering Systems and Installing Permanent Fixes</h3> | <h3>Recovering Systems and Installing Permanent Fixes</h3> | ||
| − | <p>At some point, when the emergency is over and the incident is reported, it is time to figure out how to get all of the | + | <p>At some point, when the emergency is over and the incident is reported, it is time to figure out how to get all of the enterprise's systems back in running order, as described in the [http://eitbokwiki.org/Disaster_Preparedness Disaster Preparedness chapter]. This might require changing software or hardware. It might require running malware-removal software throughout the organization. It might also require having everyone change passwords throughout the enterprise.</p> |
<p>Part of this system-recovery process should also involve putting in a permanent fix for the breach that was identified. This could mean installing patches to existing software or hardware, installing new intrusion-detection software, changing VPN protocols and procedures, or changing how sensitive data is stored. Often companies increase the level of encryption of the sensitive data. In any case, this is a time to plug the hole that was breached, and possibly plug a few others at the same time.</p> | <p>Part of this system-recovery process should also involve putting in a permanent fix for the breach that was identified. This could mean installing patches to existing software or hardware, installing new intrusion-detection software, changing VPN protocols and procedures, or changing how sensitive data is stored. Often companies increase the level of encryption of the sensitive data. In any case, this is a time to plug the hole that was breached, and possibly plug a few others at the same time.</p> | ||
<h3>Compiling Incident Documentation with Damage Assessment</h3> | <h3>Compiling Incident Documentation with Damage Assessment</h3> | ||
<p>As with most catastrophic events, it is important to document the event thoroughly, so that you can treat it as a lesson learned. Every step of the event, the analysis, and the fixes should be documented and kept with the security plan. Along with that, the damage caused and the cost of repairing the damage should be calculated and documented.</p> | <p>As with most catastrophic events, it is important to document the event thoroughly, so that you can treat it as a lesson learned. Every step of the event, the analysis, and the fixes should be documented and kept with the security plan. Along with that, the damage caused and the cost of repairing the damage should be calculated and documented.</p> | ||
| − | <p>According to the New York Times [[#Seven|[7]]], the attack on Target cost the company a reported $148 million in direct costs, and cost financial institutions $200 million. In addition, | + | <p>According to the New York Times [[#Seven|[7]]], the attack on Target cost the company a reported $148 million in direct costs, and cost financial institutions $200 million. In addition, Target's move to the chip-and-pin system, which is a more secure method for dealing with credit card data cost Target an additional $100 million, although the move to chip-and-pin was not a direct result of the breach. The company also spent $61 million in antibreach technology shortly following the attack. Even beyond those direct costs, profits fell 46 percent in the quarter following the announcement of the attack.</p> |
<h3>Review Incidents, and Updating Policies and Procedures</h3> | <h3>Review Incidents, and Updating Policies and Procedures</h3> | ||
<p>Simply identifying the things that could have been done better with respect to the incident is not enough. It is critical for the enterprise to review current policies and procedures, and make changes that decrease security risks. These changes can be as simple as how often employees are required to change their passwords. It could be changes in VPN access rules, or it could be inserting a file encryption mechanism into many data transfer processes.</p> | <p>Simply identifying the things that could have been done better with respect to the incident is not enough. It is critical for the enterprise to review current policies and procedures, and make changes that decrease security risks. These changes can be as simple as how often employees are required to change their passwords. It could be changes in VPN access rules, or it could be inserting a file encryption mechanism into many data transfer processes.</p> | ||
<h2>Summary</h2> | <h2>Summary</h2> | ||
<p>EIT security is a major area of concern for CIOs. The area is changing on a daily basis. The attacks are becoming more frequent and more sophisticated. Often the security breaches are from within, whether intentional or not.</p> | <p>EIT security is a major area of concern for CIOs. The area is changing on a daily basis. The attacks are becoming more frequent and more sophisticated. Often the security breaches are from within, whether intentional or not.</p> | ||
| − | <p>There is no way that a large enterprise can protect against all threats. Instead, an organization has to use its security resources in the most efficient way possible. To do that, the organization needs to inventory its computing assets, assess the risks and the related costs/damages of a security breach, and then make hard decisions about | + | <p>There is no way that a large enterprise can protect against all threats. Instead, an organization has to use its security resources in the most efficient way possible. To do that, the organization needs to inventory its computing assets, assess the risks and the related costs/damages of a security breach, and then make hard decisions about which risks to focus on and which to handle with less-rigorous methods, such as policies and procedures.</p> |
| − | <p>It | + | <p>It has become more and more important for organizations to understand their risk appetites, and truly weigh the potential security risks with providing new services and functionality to customers, vendors, and employees.</p> |
| − | <h2> | + | <h2> Key Maturity Frameworks</h2> |
| − | <p> | + | <p>Capability maturity for EIT refers to its ability to reliably perform. Maturity is measured by an organization's readiness and capability expressed through its people, processes, data, and technologies and the consistent measurement practices that are in place. See [http://eitbokwiki.org/Enterprise_IT_Maturity_Assessments Appendix F] for additional information about maturity frameworks.</p> |
| + | <p>Many specialized frameworks have been developed since the original Capability Maturity Model (CMM) that was developed by the Software Engineering Institute in the late 1980s. This section describes how some of those apply to the activities described in this chapter. </p> | ||
| + | <h3>IT-Capability Maturity Framework (IT-CMF) </h3> | ||
| + | <p>The IT-CMF was developed by the Innovation Value Institute in Ireland. This framework helps organizations to measure, develop, and monitor their EIT capability maturity progression. It consists of 35 EIT management capabilities that are organized into four macro capabilities: </p> | ||
| + | <ul> | ||
| + | <li>Managing EIT like a business</li> | ||
| + | <li>Managing the EIT budget</li> | ||
| + | <li>Managing the EIT capability</li> | ||
| + | <li>Managing EIT for business value</li> | ||
| + | </ul> | ||
| + | <p>Each has five different levels of maturity starting from ''initial'' to ''optimizing''. The three most relevant critical capabilities are information security management (ISM), risk management (RM), and personal data protection (PDP). </p> | ||
| + | <h4>Information Security Management Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the information security management (ISM) capability at successive levels of maturity.</p> | ||
| + | <table> | ||
| + | <tr valign="top"><td width="10%">Level 1</td><td>The approach to information security tends to be localized. Incidents are typically not responded to in a timely manner. </td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>Defined security approaches, policies, and controls are emerging, primarily focused on complying with regulations. </td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>Standardized security approaches, policies, and controls are in place across the EIT function, dealing with access rights, business continuity, budgets, toolsets, incident response management, audits, non-compliance, and so on. </td></tr> | ||
| + | <tr valign="top"><td>Level 4</td><td>Comprehensive security approaches, policies, and controls are in place and are fully integrated across the organization. </td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>Security approaches, policies, and controls are regularly reviewed to maintain a proactive approach to preventing security breaches. </td></tr> | ||
| + | </table> | ||
| + | <h4>Risk Management Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the risk management (RM) capability at successive levels of maturity.</p> | ||
| + | <table> <tr valign="top"><td width="10%">Level 1</td><td>The risk management program and framework are considered in an ad hoc manner, if at all. No risk-related roles are defined, or they are defined in an ad hoc manner. Risks are not actively or systematically managed. </td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>The risk management program sits within the EIT function, and a basic framework is established. Responsibility and accountability for risk management are assigned to persons/roles in the EIT function. Some basic risk management approaches are established but these may not be consistently adhered to.</td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>The risk management program and supporting framework are established and consistently referenced in the EIT function and some other business units. Responsibility and accountability for risk management are assigned to dedicated persons/roles in the EIT function and other business units. Most risk management activities adhere to defined and documented approaches.</td></tr> | ||
| + | <tr valign="top"><td>Level 4</td><td>The risk management program and framework are established through the cooperation of, and in consultation with, the EIT function and the rest of the business. The risk management of EIT is integrated into wider ERM practices. Explicit risk management responsibility and accountability are assigned to employees across the organization. Compliance with the approaches, principles, and guidance for all risk management activities is mandated and enforced organization-wide.</td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>The risk management program and framework are continually refined and updated, and involve regular cooperation with business ecosystem partners. Responsibility and accountability for risk management are dynamically assigned to the appropriate organization level, and regularly reviewed. Risk management approaches, principles, and guidance are continually reviewed and improved based on changes in the risk landscape, and learning from previous risk incidents. </td></tr> | ||
| + | </table> | ||
| + | <h4>Personal Data Protection Maturity</h4> | ||
| + | <p>The following statements provide a high-level overview of the personal data protection (PDP) capability at successive levels of maturity.</p> | ||
| + | <table> | ||
| + | <tr valign="top"><td width="10%">Level 1</td><td>There is limited to no understanding of personal data protection obligations, and enforcement is ad hoc.</td></tr> | ||
| + | <tr valign="top"><td>Level 2</td><td>The EIT function has started rolling out personal data protection policies and procedures to meet high-priority legislative, regulatory, EIT and business needs. The risks associated with holding personal data have begun to reduce. </td></tr> | ||
| + | <tr valign="top"><td>Level 3</td><td>The management of personal data protection follows standardized policies and procedures across the EIT function and some other business units for most priority legislative, regulatory, EIT and business needs. The organization's reputation for managing personal data is growing. </td></tr> | ||
| + | <tr valign="top"><td>Level 4</td><td>The management of personal data protection follows comprehensive policies and procedures across the entire organization for all necessary legislative, regulatory, EIT, and business needs. The organization has a good reputation for managing personal data. </td></tr> | ||
| + | <tr valign="top"><td>Level 5</td><td>There is a culture of proactive personal data protection across key business ecosystem partners. This is continually reviewed to ensure that the likelihood of personal data privacy violation remains low. </td></tr> | ||
| + | </table> | ||
| + | <h2>Key Competence Frameworks</h2> | ||
| + | <p>While many large companies have defined their own sets of skills for purposes of talent management (to recruit, retain, and further develop the highest quality staff members that they can find, afford and hire), the advancement of EIT professionalism will require common definitions of EIT skills that can be used not just across enterprises, but also across countries. We have selected three major sources of skill definitions. While none of them is used universally, they provide a good cross-section of options. </p> | ||
| + | <p>Creating mappings between these frameworks and our chapters is challenging, because they come from different perspectives and have different goals. There is rarely a 100 percent correspondence between the frameworks and our chapters, and, despite careful consideration some subjectivity was used to create the mappings. Please take that in consideration as you review them.</p> | ||
| + | <h3>Skills Framework for the Information Age</h3> | ||
| + | <p>The Skills Framework for the Information Age (SFIA) has defined nearly 100 skills. SFIA describes seven levels of competency that can be applied to each skill. However, not all skills cover all seven levels. Some reach only partially up the seven-step ladder. Others are based on mastering foundational skills, and start at the fourth or fifth level of competency. SFIA is used in nearly 200 countries, from Britain to South Africa, South America, to the Pacific Rim, to the United States. (http://www.sfia-online.org)</p> | ||
| + | <p>SFIA skills have not yet been defined for this chapter.</p> | ||
| + | <table cellpadding="5" border="1"> | ||
| + | <tr><th width="15%" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Skill</font></th><th style="background-color: #58ACFA;" font-size="14pt"><font color="white">Skill Description</font></th><th width="10%" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Competency Levels</font></th></tr> | ||
| + | <tr valign="top"><td>Information assurance</td><td>The protection of integrity, availability, authenticity, non-repudiation, and confidentiality of information and data in storage and in transit. The management of risk in a pragmatic and cost-effective manner to ensure stakeholder confidence.</td><td valign="top">5-7</td></tr> | ||
| + | <tr valign="top"><td>Information security</td><td>The selection, design, justification, implementation, and operation of controls and management strategies to maintain the security, confidentiality, integrity, availability, accountability, and relevant compliance of information systems with legislation, regulation, and relevant standards.</td><td valign="top">3-7</td></tr> | ||
| + | <tr valign="top"><td>Penetration testing</td><td>The assessment of organizational vulnerabilities through the design and execution of penetration tests that demonstrate how an adversary can either subvert the organization's security goals (e.g., the protection of specific intellectual property) or achieve specific adversarial objectives (e.g., establishment of a covert command and control infrastructure). Pen test results provide deeper insight into the business risks of various vulnerabilities.</td><td valign="top">4-6</td></tr> | ||
| + | <tr valign="top"><td>Digital forensics</td><td>The collection, processing, preserving, analyzing, and presenting of computer-related evidence in support of security vulnerability mitigation and criminal, fraud, counterintelligence, or law enforcement investigations.</td><td valign="top">4-6</td></tr> | ||
| + | <tr valign="top"><td>Security administration</td><td>The provision of operational security management and administrative services. This typically includes the authorization and monitoring of access to EIT facilities or infrastructure, the investigation of unauthorized access, and compliance with relevant legislation.</td><td valign="top">1-6</td></tr> | ||
| + | </table> | ||
| + | <h3>European Competency Framework</h3> | ||
| + | <p>The European Union's European e-Competence Framework (e-CF) has 40 competences and is used by a large number of companies, qualification providers, and others in public and private sectors across the EU. It uses five levels of competence proficiency (e-1 to e-5). No competence is subject to all five levels.</p> | ||
| + | <p>The e-CF is published and legally owned by CEN, the European Committee for Standardization, and its National Member Bodies (www.cen.eu). Its creation and maintenance has been co-financed and politically supported by the European Commission, in particular, DG (Directorate General) Enterprise and Industry, with contributions from the EU ICT multi-stakeholder community, to support competitiveness, innovation, and job creation in European industry. The Commission works on a number of initiatives to boost ICT skills in the workforce. Version 1.0 to 3.0 were published as CEN Workshop Agreements (CWA). The e-CF 3.0 CWA 16234-1 was published as an official European Norm (EN), EN 16234-1. For complete information, see http://www.ecompetences.eu. </p> | ||
| + | <table cellpadding="5" border="1"> | ||
| + | <tr><th width="85%" style="background-color: #58ACFA;" font-size="14pt"><font color="white">e-CF Dimension 2</font></th><th style="background-color: #58ACFA;" font-size="14pt"><font color="white">e-CF Dimension 3</font></th></tr> | ||
| + | <tr valign="top"><td><strong>D.1. Information Security Strategy Development (ENABLE)</strong><br />Defines and makes applicable a formal organizational strategy, scope, and culture to maintain the safety and security of information from external and internal threats, i.e., digital forensic for corporate investigations or intrusion investigation. Provides the foundation for information security management, including role identification and accountability. Uses defined standards to create objectives for information integrity, availability, and data privacy.</td><td valign="top">Level 4-5</td></tr> | ||
| + | <tr valign="top"><td><strong>E.8. Information Security Management (MANAGE)</strong><br />Implements information security policy. Monitors and takes action against intrusion, fraud, and security breaches or leaks. Ensures that security risks are analyzed and managed with respect to enterprise data and information. Reviews security incidents, and makes recommendations for security policy and strategy to ensure continuous improvement of security provision.</td><td valign="top">Level 2-4</td></tr> | ||
| + | </table> | ||
| + | <h3>i Competency Dictionary </h3> | ||
| + | <p>The Information Technology Promotion Agency (IPA) of Japan has developed the i Competency Dictionary (iCD) and translated it into English, and describes it at https://www.ipa.go.jp/english/humandev/icd.html. The iCD is an extensive skills and tasks database, used in Japan and southeast Asian countries. It establishes a taxonomy of tasks and the skills required to perform the tasks. The IPA is also responsible for the Information Technology Engineers Examination (ITEE), which has grown into one of the largest scale national examinations in Japan, with approximately 600,000 applicants each year.</p> | ||
| + | <p>The iCD consists of a Task Dictionary and a Skill Dictionary. Skills for a specific task are identified via a "Task x Skill" table. (See [http://eitbokwiki.org/Glossary Appendix A] for the task layer and skill layer structures.) EITBOK activities in each chapter require several tasks in the Task Dictionary. </p> | ||
| + | <p>The table below shows a sample task from iCD Task Dictionary Layer 2 (with Layer 1 in parentheses) that corresponds to activities in this chapter. It also shows the Layer 2 (Skill Classification), Layer 3 (Skill Item), and Layer 4 (knowledge item from the IPA Body of Knowledge) prerequisite skills associated with the sample task, as identified by the Task x Skill Table of the iCD Skill Dictionary. The complete iCD Task Dictionary (Layer 1-4) and Skill Dictionary (Layer 1-4) can be obtained by returning the request form provided at http://www.ipa.go.jp/english/humandev/icd.html. </p> | ||
| + | <table cellpadding="5" border="1"> | ||
| + | <tr><th width="15%" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Task Dictionary</font></th><th colspan="3" style="background-color: #58ACFA;" font-size="14pt"><font color="white">Skill Dictionary</font></th></tr> | ||
| + | <tr><th width="30%" style="background-color: #58ACFA;"><font color="white">Task Layer 1 (Task Layer 2)</font></th><th width="15%" style="background-color: #58ACFA;"><font color="white">Skill Classification</font></th><th width="15%" style="background-color: #58ACFA;"><font color="white">Skill Item</font></th><th width="40%" style="background-color: #58ACFA;"><font color="white">Associated Knowledge Items</font></th></tr> | ||
| + | <tr valign="top"><td><em><strong>Information security operation management <br />(EIT operation control)</strong></em></td> | ||
| + | <td valign="top">Basic security technology</td> | ||
| + | <td valign="top">Information security</td> | ||
| + | <td> <ul> | ||
| + | <li>Understanding and utilization of PKI technology trends</li> | ||
| + | <li>Access control (authentication, log monitoring, etc.)</li> | ||
| + | <li>Rules on installing applications (rules on the installation and use of applications on machines connected to the network)</li> | ||
| + | <li>Application security</li> | ||
| + | <li>Installation and administrative rules for public Internet servers (rules on installation standards and operational management of servers to be connected to the Internet)</li> | ||
| + | <li>Rules on Internet use (rules on the use of email and Internet access from the company)</li> | ||
| + | <li>Operational rules for measures against computer viruses (rules relating to measures against computer viruses for machines that exchange data externally)</li> | ||
| + | <li>Standards for measures against computer viruses</li> | ||
| + | <li>Standards for measures against unauthorized access to computers</li> | ||
| + | <li>Understanding and utilization of single sign-on technology trends</li> | ||
| + | <li>Understanding and utilization of technology trends in security administration</li> | ||
| + | <li>Security tools (free, commercial)</li> | ||
| + | <li>Security test items</li> | ||
| + | <li>Data protection (encryption, transmission, etc.)</li> | ||
| + | <li>Network protection (firewalls, intrusion detection, etc.)</li> | ||
| + | <li>Understanding and utilization of firewall technology</li> | ||
| + | <li>Malware (viruses, spyware, worms, adware)</li> | ||
| + | <li>Encryption (DES)</li> | ||
| + | <li>Encryption (RSA)</li> | ||
| + | <li>Cryptography (common key, public key, private key, RSA, AES, hybrid encryption, hash functions, etc.)</li> | ||
| + | <li>Understanding and utilization of cryptography</li> | ||
| + | <li>Threat</li> | ||
| + | <li>Public key infrastructure (PKI, certificate authorities, digital certificates, etc.)</li> | ||
| + | <li>Attack methods (SQL injection, cross site scripting, DoS attack, phishing, targeted attacks, etc.)</li> | ||
| + | <li>Confidentiality, integrity, and availability</li> | ||
| + | <li>Understanding and utilization of technology trends in intrusion prevention</li> | ||
| + | <li>Government public key infrastructure (GPKI, bridge certification authority, etc.)</li> | ||
| + | <li>Biometric authentication technology</li> | ||
| + | <li>Vulnerability</li> | ||
| + | <li>Copyright protection (CPRM)</li> | ||
| + | <li>Copyright protection (CSS)</li> | ||
| + | <li>Understanding and utilization of electronic signature technology</li> | ||
| + | <li>Authentication technology (digital signatures, message authentication, time stamps, etc.)</li> | ||
| + | <li>User authentication (ID, password, etc.)</li> | ||
| + | </ul> | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
<h2>Key Roles</h2> | <h2>Key Roles</h2> | ||
| − | <p> | + | <p>These roles are common to ITSM.</p> |
| + | <ul> | ||
| + | <li>Compliance Manager</li> | ||
| + | <li>Enterprise Architect</li> | ||
| + | <li>Information Security Manager</li> | ||
| + | <li>Risk Manager</li> | ||
| + | <li>Service Design Manager</li> | ||
| + | <li>Technical Analyst</li> | ||
| + | </ul> | ||
| + | <p>Other key roles include:</p> | ||
| + | <ul> | ||
| + | <li>Chief Information Security Officer</li> | ||
| + | <li>Data architect </li> | ||
| + | <li>Data owner</li> | ||
| + | <li>Operations Manager</li> | ||
| + | </ul> | ||
<h2>Standards</h2> | <h2>Standards</h2> | ||
<ul> | <ul> | ||
| − | <li>ISO/IEC 27001: | + | <li>ISO/IEC 27013, Information technology—Security techniques—Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000–1</li> |
| − | <li>ISO/IEC 27002:2013, Information | + | <li>ISO/IEC 27000:2016, Information technology—Security techniques—Information security management systems—Overview and vocabulary (this is the general overview to the ISO/IEC 27000 series of over 30 standards on information security management systems, and terms and definitions commonly used in the ISMS family of standards).</li> |
| − | <li>ISO/IEC 15408:2009, information | + | <li>ISO/IEC 27001:2013, Information technology—Security techniques—Information security management systems—Requirements</li> |
| − | <li>Federal Information Processing Standards (FIPS) 140 | + | <li>ISO/IEC 27002:2013, Information technology—Security techniques—Information security management systems—Code of practice for information security controls</li> |
| + | <li>ISO/IEC 15408:2009, information technology—The common criteria for Information Technology Security Evaluation as an international standard for computer security certification. Establishes the general concepts and principles of EIT security evaluation and specifies the general model of evaluation given by various parts of ISO/IEC 15408, which is its entirety is meant to be used as the basis for evaluation of security properties of EIT products.</li> | ||
| + | <li>ISO/IEC/IEEE 15026, System and software engineering—Systems and software assurance (4 parts)</li> | ||
| + | <li>Federal Information Processing Standards (FIPS) 140 series—These publications are computer security standards created by the US government specifically concerning cryptographic modules. FIPS 140-2 defines four levels of security and sets requirements in 11 different cryptographic areas including roles, services and authentication, physical security, design assurance, and cryptographic module ports and interfaces. [[#Fourteen|[14]]]</li> | ||
</ul> | </ul> | ||
<h2>References</h2> | <h2>References</h2> | ||
| − | <div id="One"></div | + | <div id="One"></div>[1] ISO/IEC 27000:2014 definition of "information security." |
| − | + | <div id="Two"></div>[2] ISO/IEC 27001:2013, Information technology—Security techniques—Information security management systems—Requirements. | |
| − | <div id="Two"></div | + | <div id="Three"></div>[3] ISO/IEC 27002:2013, Information technology—Security techniques—Information security management systems—Code of practice for information security controls. |
| − | <div id="Three"></div | + | <div id="Four"></div>[4] J.D. Meier, A. Mackman, S. Vasireddy, et al. ''Improving Web Application Security: Threats and Countermeasures'', http://www.cgisecurity.com/lib/Threats_Countermeasures.pdf, June 2003. |
| − | <div id="Four"></div | + | <div id="Five"></div>[5] IAPP Information Privacy Certification Glossary of Common Privacy Terminology https://iapp.org/media/pdf/certification/CIPP_Glossary_0211updated.pdf, 2011. |
| − | <div id="Five"></div | + | <div id="Six"></div>[6] Information Technology—Security techniques—Privacy framework, ISO/IEC 29100:2011; http://a-infosec.com/2014/01/25/public-available-of-isoiec-291002011-privacy-framework/ |
| − | <div id="Six"></div | + | <div id="Seven"></div>[7] Rachel Abrahms, ''Target Puts Data Breach Costs at $148 Million, and Forecasts Profit Drop'', New York Times, http://www.nytimes.com/2014/08/06/business/target-puts-data-breach-costs-at-148-million.html?_r=0, August 2014. |
| − | <div id="Seven"></div | + | <div id="Eight"></div>[8] ''What is Build Security In?'' https://buildsecurityin.us-cert.gov/ |
| − | <div id="Eight"></div | + | <div id="Nine"></div>[9] Dimensional Research, ''The Impact of Mobile Devices on Information Security: A Survey of IT Professionals'', https://www.checkpoint.com/downloads/products/check-point-mobile-security-survey-report2013.pdf, June 2013. |
| − | <div id="Nine"></div | + | <div id="Ten"></div>[10] Phil Brit, ''10 Trickiest Mobil Security Threats'', eSecurity Planet, April 2015. |
| − | <div id="Ten"></div | + | <div id="Eleven"></div>[11] OWASP, Top 10 2013, https://www.owasp.org/index.php/Top_10_2013-Top_10 |
| − | <div id="Eleven"></div | + | <div id="Twelve"></div>[12] CWE/SANS, ''CWE/SANS Top 25 Most Dangerous Software Errors'', https://www.sans.org/top25-software-errors/, June 2011. |
| − | <div id="Twelve"></div | + | <div id="Thirteen"></div>[13] ITU-T, ''Common vulnerabilities and exposures'', http://www.itu.int/ITU-T/recommendations/rec.aspx?rec=11061, April 2011. |
| − | <div id="Thirteen"></div | + | <div id="Fourteen"></div>[14] NIST Federal Information Processing Standards (FIPS) Publications, Feb 2013; http://csrc.nist.gov/publications/PubsFIPS.html. |
| − | <div id="Fourteen"></div | + | <div id="Fifteen"></div>[15] M. West-Brown, D. Stikvoort, KP Kossakowski, et. al., ''Handbook for Computer Security Incident Response Teams (CSIRTs)'', MU/SEI-2003-HB-002, Carnegie Mellon University, http://resources.sei.cmu.edu/asset_files/Handbook/2003_002_001_14102.pdf, April 2003. |
| − | <div id="Fifteen"></div | + | <div id="Sixteen"></div>[16] CSO Staff, ''The security laws, regulations, and guidelines directory'', December 2012, http://www.csoonline.com/article/2126072/compliance/the-security-laws—regulations-and-guidelines-directory.html. |
| − | <div id="Sixteen"></div | + | |
<h2>Related and Informing Disciplines</h2> | <h2>Related and Informing Disciplines</h2> | ||
| − | < | + | <ul> |
| − | <p>DHS: IT Security Essential BoK</p> | + | <li>Physical and facilities security</li> |
| + | <li>Personnel security</li> | ||
| + | <li>Transportation security</li> | ||
| + | <li>Retail security</li> | ||
| + | <li>Manufacturing security</li> | ||
| + | <li>Insurance and financial services security</li> | ||
| + | <li>Healthcare security</li> | ||
| + | <li>Utilities security</li> | ||
| + | <li>Cryptography</li> | ||
| + | <li>Code analysis tools</li> | ||
| + | <li>Logging and tracing</li> | ||
| + | <li>Biometric authentication</li> | ||
| + | <li>Copyright and intellectual property protection</li> | ||
| + | </ul> | ||
| + | <h2>Additional Reading</h2> | ||
| + | <p>DHS: "IT Security Essential BoK, A Competency and Functional framework for IT Security Workforce Development," http://csrc.nist.gov/groups/SMA/ispab/documents/minutes/2007-12/ISPAB_Dec7-BOldfield.pdf</p> | ||
| + | <p>NIST, Special Publication 800-37 (Revision 1), "Guide for Applying the Risk Management Framework to Federal Information Systems," February 2010.</p> | ||
Latest revision as of 01:02, 23 December 2017
|
Contents
- 1 Introduction
- 2 Goals and Principles
- 3 Context Diagram
- 4 Information Security Management
- 5 Establishing Enterprise-Wide Security
- 6 Security Education and Training
- 7 Assets, Risks, and Threat Protection
- 8 Designing Controls
- 9 Implementing and Maintaining Selected Security Controls
- 10 Security Monitoring, Accountability, and Testing
- 11 Security Incident Response and Management
- 11.1 Detecting the Event
- 11.2 Assessing/Analyzing the Event
- 11.3 Containing the Damage
- 11.4 Collecting and Protecting Evidence
- 11.5 Communicating to Those Affected
- 11.6 Notifying Appropriate Agencies
- 11.7 Recovering Systems and Installing Permanent Fixes
- 11.8 Compiling Incident Documentation with Damage Assessment
- 11.9 Review Incidents, and Updating Policies and Procedures
- 12 Summary
- 13 Key Maturity Frameworks
- 14 Key Competence Frameworks
- 15 Key Roles
- 16 Standards
- 17 References
- 18 Related and Informing Disciplines
- 19 Additional Reading
1 Introduction
"There are only two types of companies: those that have been hacked, and those that will be."
~ FBI Director Robert Mueller, October 2012
"There are two kinds of big companies in the United States. There are those who've been hacked by the Chinese and those who don't know that they've been hacked by the Chinese."
~ FBI Director James Comey, October 2014
Whether you call it computer security, cybersecurity, or EIT security, one thing is true, technological security is a rapidly changing area. The change is so rapid that it is nearly impossible for organizations (whether commercial, educational, or governmental) to keep up with the perpetrators of cyberattacks. Attacks that used to be carried out by lone individuals trying to see if they could get access to "secure" servers are now being organized and financed by governments. The way that an organization approached security in 2005 isn't sufficient in 2017, and we are pretty sure that it will be a totally different world in 2025. Flexibility and adaptability in this area is essential.
Organizations (both small and large) depend on information technology and the information systems that are developed to successfully carry out their missions and business functions. Information systems can include a vast range of diverse computing platforms from high-end supercomputers and highly virtualized platforms to tablets and mobile devices. Information systems also include specialized systems and devices, such as telecommunication systems, industrial/process control systems, testing and calibration devices, weapons systems, command and control systems, and environmental control systems. All of these systems are subject to serious threats that can have adverse impacts on organizational operations, assets, individuals, associated organizations, and even countries by compromising the confidentiality, integrity, or availability of information being processed, stored, or transmitted by those systems.
Threats to information and information systems include environmental disruptions, human and machine errors, and purposeful attacks. Cyberattacks on information systems today are often aggressive, disciplined, well-organized, long-term, well-funded, and in a growing number of documented cases, extremely sophisticated. Successful attacks on public and private sector information systems (especially toward critical infrastructure) can result in serious damage not only to the organization that was attacked, but also to the national and economic security interests of an entire country.
We make an attempt in this chapter to describe EIT security as we know it today. We highlight the current challenges and indicate some of the most successful processes that enterprises use in this ongoing battle.
2 Goals and Principles
While there are many definitions for security, most include the three dimensions of confidentiality, integrity, and availability (sometimes referred to as the CIA triad). As such, the primary goal of EIT security is to preserve the confidentiality, integrity, and availability of information and information systems. [1]
The principles behind an organization's information security management system (ISMS) should be to design, implement, and maintain a coherent set of policies, processes, and systems that keep the risks associated with its information assets at a tolerable level, and yet, manage the cost and inconvenience of said risk management. As such, the goals of EIT security are to:
- Always understand the current risk tolerance of the enterprise with respect to information and device security.
- Understand the security threats and potential damages to information, devices, and individuals.
- Create and follow policies and procedures that keep cyberattack risk and damages at or below a tolerable level.
- Effectively and efficiently detect and deal with cyberattack incidents.
3 Context Diagram
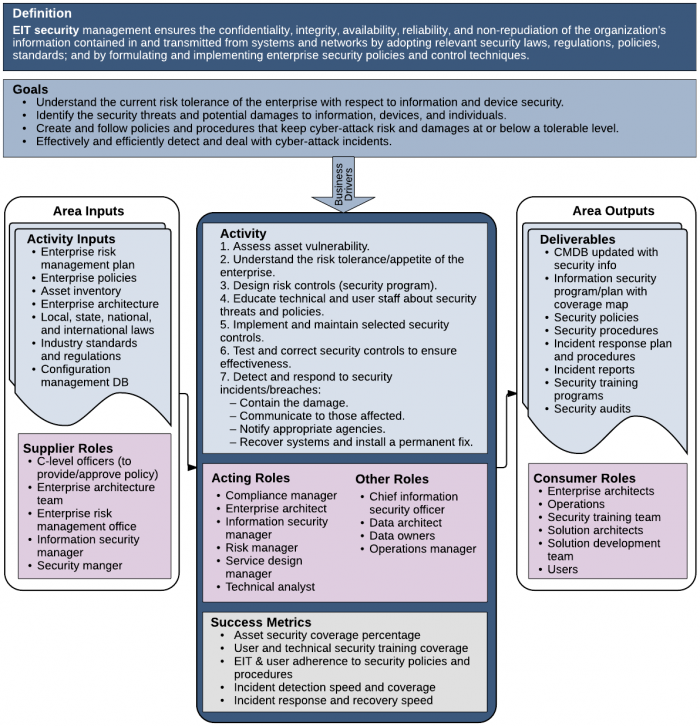
Figure 1. Context Diagram for Security
4 Information Security Management
"An information security management system (ISMS) includes policies, processes, procedures, organizational structures, software, and hardware to protect the identified information assets. These controls need to be specified, implemented, monitored, reviewed, and improved where necessary, to ensure that the specific information security and business objectives of the organization are met. Relevant information security controls are expected to be seamlessly integrated with an organization's business processes." ~ ISO/IEC 27002:2013, Clause 3.2.3 Information security, Pg. 26 [3]
An ISMS must remain in place and be effective for a long period of time; however, it must also be able to adapt to changes in the EIT organization and the solutions that it supports, as well as evolving security threats. As a result, the ISMS must be carefully designed, implemented with care, strongly managed, and continuously reevaluated and updated.
4.1 Security Management Practices and Frameworks
A mature ISMS uses an information security framework to achieve the enterprise's objectives. Such a framework is a series of documented processes that are used to define policies and procedures that support the implementation and ongoing management of information security controls. A framework is basically a blueprint for building an information security program to manage risk and reduce vulnerabilities, and to define and prioritize the tasks required to build security into an organization.
There are several mature information security frameworks, including the following more widely used frameworks:
- ISO/IEC 27000 Series—The International Organization for Standardization (IOS) and the International Electrotechnical Commission (IEC) provide recommended practices on information security management and program elements. ISO defines the broadest structure of an effective overall program, supporting information security as a systems issue that includes technology, practice, and people. It also describes the need for a formal security program.
- NIST SP 800 Series—The National Institute of Standards and Technology (U.S. Department of Commerce) has produced a number of special publications (the 800 series) that are specifically focused on computer security. This series discusses the Information Technology Laboratory's research, guidelines, and outreach efforts concerning computer security, along with its collaborative activities with industry, government, and educational institutions. Some examples of these collaborations include catalogs of security controls for information systems (800-53).
- COBIT—The Control Objectives for Information and Related Technology (COBIT) is a set of mythologies and practices for EIT management that focuses on defining program and management control functions. Use of these standard practices can help ensure that EIT programs are implemented and managed effectively. COBIT states that the security publication "provides guidance to help EIT and security professionals understand, utilize, implement, and direct important information-security-related activities, and make more informed decisions while maintaining awareness about emerging technologies and the accompanying threats."
- Information Security Forum's Standard of Good Practice'—This document is a comprehensive, business-focused guide to managing information security risks. It is aligned with the requirements for an ISMS as described in the ISO/IEC 2700X standards. It provides deeper coverage for most of the control topics.
- ISACA RISK IT—The Information Systems Audit and Control Association (ISACA) has produced a Risk IT framework that aims to fill the gap between generic risk management frameworks and more specific EIT risk management frameworks. It provides a wide view of all risks related to EIT and a similarly thorough treatment of risk management. It builds upon the other risk-related components within the current ISACA frameworks, such as COBIT and Val IT.
- OCTAVE—The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) method is used to assess an organization's information security needs. OCTAVE methods are self-directed and flexible. Small teams across business units and EIT can work together to address the security needs of the enterprise. OCTAVE can be customized to match the organization's unique risk environment, security and resilience objectives, and skill level. OCTAVE moves an organization toward an operational risk-based view of security and puts it in a business context.
- COSO—The Committee of Sponsoring Organizations (COSO) of the Treadway Commission has created a list of control objectives for enterprise governance and risk management. COSO defines a set of business, management, and security-relevant controls that can be used to demonstrate good business practices, and can be used to show compliance with Sarbanes-Oxley.
- HITRUST CSF—This is a certifiable framework that provides healthcare-relevant security regulations and standards. It describes a flexible approach to risk management and compliance for the HIPAA and HITECH regulations (described later). At the present time, it is the most widely adopted security framework by the US healthcare industry.
4.2 Cybersecurity Laws and Regulations Factor
An ISMS cannot be constructed without considering the laws and regulations that affect the enterprise. The issue here is that those laws and regulations are under constant flux. When investigating cybersecurity laws and regulations, we have to look at local, state, national, and international regulations. We also have to consider regulations specific to the enterprise's industry, such as health care. For larger organizations that have significant risk, security lawyers may be required to identify relevant regulations and to keep track of new legislation. Here is a brief overview. [16]
Each country has its own laws, and those laws differ a great deal. Over the last several years, the UN has taken up the issue of cybersecurity. In 2013, the United Nations Group of Governmental Experts (GGE) published a report that listed a set of "high-level cyber norms" that all countries should follow. They include:
- Abide by international law when operating in cyberspace.
- Honor the "norm of state responsibility" for cyberattacks emanating from their territory.
- Work to develop confidence-building measures to reduce risk of conflict.
- Engage in capacity-building efforts to assist developing countries build skills to protect their networks and citizens.
The GGE meets fairly regularly to build on their work and have recently taken on defining limits on the use of national cyberpower aimed at the critical infrastructure of other states.
4.2.1 Laws and Regulations Outside the United States
As mentioned above, cybersecurity is a fast-changing area globally. Although the US, China, and Russia have been considered in the lead, most countries have basic cybersecurity laws and policies. Many of those are associated with the country's national security and defense strategies. It would take too long to go through every country, so we have picked a few to discuss. For information about specific countries and their policies and security strategies, visit https://ccdcoe.org/cyber-security-strategy-documents.html.
- China—China has a set of the world's tightest Internet restrictions and this is part of their cybersecurity strategy. They have numerous laws that authorize the control of flow of online information in the country and many foreign sites are blocked. Laws also require companies to censor and restrict online anonymity, to store user data in China, and to monitor and report all network security incidents. China is serious about security and jails more people for computer "misuse" than any other country; however, most of the people are arrested as part of their censorship laws, not cybercrimes. Blogs and social-site posts critical of the government usually result in an arrest.
- Russia—Like China, for many years Russia was worried about cybercontent (the information) more than cybersecurity. However, they have not overtly censored social media or blogs, like the Chinese. In addition, they have maintained a strict "non-interference" policy concerning their cyberspace, which has pushed them to create numerous international non-interference pacts. Russia has well-developed tools for incident detection and is also considered a leader in developing software and techniques for cybercrime. Interestingly enough, it has only been since 2012 or so that Russia started to take cybercrimes committed by Russians seriously.
- The European Union—In 2013, the European Commission and High Representative's Cyber Security Strategy document was the first comprehensive EU document concerning cyberspace. It set the tone of the EU's strategy as "open, safe, and secure," and it specified how the EU would approach building their cybersecurity capacity. In August 2015, the EU proposed a strict law to impose security requirements on Internet service providers and web companies. The new law also requires reporting data breaches to EU governments. One of the critical points brought up in the deliberations of the law is that if a cloud computing company or ISP does business with a "critical sector" company, the web company needs to follow the same security rules as the critical sector company.
4.2.2 Laws and Regulations in the United States
4.2.2.1 National Laws and Regulations
Over the last 15 year, the US federal government has lead the way in developing laws and regulations regarding cyberhacking and cybersecurity. The laws treat different organization types differently, so some enterprises are strongly affected by cybersecurity laws and regulations while other are not affected at all. Despite the fact that most people believe that cybersecurity regulations are necessary, there is a lot of disagreement about who these laws should regulate. Some people believe that laws should cover only acts of breaching security (hacking). Others think that there should be laws to regulate businesses and how they protect data.
In the US, cybersecurity regulation consists of directives (both administrative directives and legislation) that safeguard information technology and computer systems. The purpose of these directives is to force companies and organizations to protect their systems and information from cyberattacks, such as viruses, worms, Trojan horses, phishing, denial-of-service (DOS) attacks, unauthorized access (stealing intellectual property or confidential information), and control system attacks.
Most regulations encourage the use of measures that are designed to prevent cyberattacks, including firewalls, antivirus software, intrusion detection and prevention systems, encryption, and login passwords. [2] For most industries, these measures are currently voluntary. There are three regulations that mandate healthcare organizations, financial institutions, and federal agencies protect their systems and information: the 1996 Health Insurance Portability and Accountability Act (HIPAA), the 1999 Gramm-Leach-Bliley Act, and the 2002 Homeland Security Act.
Although the mandates only cover a few industries right now, many industry regulators are planning to include cybersecurity measures as a part of their standard regulatory examinations in the near future.
4.2.2.2 State and Local Regulations
State governments have attempted to improve cybersecurity by increasing public visibility of firms with weak security. In 2003, California passed the Notice of Security Breach Act and California Assembly Bill 1958, which requires that any company maintaining personal information (name, social security number, driver's license number, credit card number, or financial information) of California citizens that has a security breach must disclose the details of the event. In 2004, California passed California Assembly Bill 1950, which also applies to businesses that own or maintain personal information for California residents. This regulation dictates that businesses maintain a reasonable level of security and that these required security practices also extend to business partners. These security breach notification regulations punish firms for their cybersecurity failures while giving them the freedom to choose how to secure their systems. Many other states have passed similar laws. The problem with many of these laws is that they use the phrase "reasonable level of security." This phrase gives businesses too much room for interpretation. In addition, it is unclear whether organizations can actually be held accountable in court.
4.2.2.3 Privacy Laws and Regulations
As mentioned above, the number of laws and regulations concerning data security are increasing over time. Privacy of customer transactions, whether a purchase or some other action, is considered the ethical responsibility of EIT by most governing bodies these days. This is a huge area of vulnerability for many enterprises, and many cybersecurity experts believe that litigation associated with privacy and data protection breaches are going to increase significantly in the near future.
The International Association of Privacy Professionals (IAPP) glossary [5] defines privacy as: The appropriate use of personal information under the circumstances. What is appropriate will depend on context, law, and the individual's expectations; also, the right of an individual to control the collection, use and disclosure of information. Data protection is defined as the management of personal information.
In the United States, privacy is the term that is used in policies, laws, and regulation. However, in the European Union and other countries, the term data protection often identifies privacy-related laws and regulations. Because of the different levels of regulation, international agreements have come into existence to manage compliance between countries and regions. The best known example being the US-EU Safe Harbor Principles, which streamline compliance for US companies attempting to meet the EU directive (95/46/EC) on protection of personal data.
The regulations associated with privacy are changing frequently, but the most common US laws are listed below.
- Healthcare providers, payers, clearinghouses, and similar organizations must comply with a set of government regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health Act (HITECH). Over the years, enforcement for violations of both of these acts has been strengthened, and incentives have been put in place for the adoption of a secure electronic health records act to protect personal health information.
- The Gramm-Leach-Bliley Act requires financial institutions that offer consumers financial products or services to safeguard sensitive client data.
- The Payment Card Industry Data Security Standard (PCI-DSS) is a common set of security controls for protecting credit card information maintained by the PCI Security Standards Council.
- Consent management is the newest level of privacy legislation coming into effect, which has steep fines for non-compliance distribution of content.
Data and privacy protection is important to most other countries and regulations have been uniformly increased around the world in the last few years:
- The EU Data Protection Directive has been in place since 2011, and will be updated by the end of 2015 to Directive 95/46/EC. It will likely be one of the strongest sets of regulations to protect personal data in the world. Its primary goal is to bring all EU nations into alignment with respect to data protection and to raise every member country's standards, but it will also lay the groundwork for fining companies that do not comply with the new regulations.
- In 2014, Australia amended its Privacy Act to cover cloud and communications service providers and any other organizations that collect, process, or store personal information. As with many of the policies of other countries, not only does this amendment increase coverage of the law to global service providers, it enables the Australian Information Commissioner to monitor how companies comply with the policy, train their staff, and handle incidents and complaints.
4.2.3 More about Privacy and Data Protection
ISO/IEC 29100 [6] identifies a number of what they call privacy principles that should be followed by all organizations that handle personal information:
- The owner of the data must have consent and choice.
- The user of the data must specify their use and demonstrate legitimacy of purpose.
- The collection of data must be limited to the specified purpose.
- The data kept should be minimized to just what is needed.
- The data use and retention should be limited and disclosed.
- The organization should be able to ensure the accuracy and quality of the data.
- The organization should demonstrate openness, transparency, and notice.
- The organization must be accountable.
- The organization needs to provide a reasonable amount of information security.
- The organization must be compliant with all privacy laws and regulations.
5 Establishing Enterprise-Wide Security
Establishing an effective enterprise-wide security program is a critical and difficult task. It requires both careful assessment of the enterprise's current situation, and an understanding of the organization's tolerance for risk. When those things are understood, a plan needs to be developed that covers all departments of the enterprise, as well as staff, vendors, and clients.
5.1 Enterprise-Level Vulnerability Assessment and Risk Tolerance
"Risk management is the process for identifying, analyzing, and communicating risk and accepting, avoiding, transferring, or controlling it to an acceptable level considering associated costs and benefits of any actions taken." ~ DHS Risk Lexicon, 2010 Edition
The area of vulnerability assessment and risk management is a key security competency for all enterprises. Risk management is more than just looking for vulnerabilities and then planning how to protect against them. There are two factors to consider. First, an organization could just shut down access to systems to control threats, but that likely does not meet the business's objectives and purpose for existence. For example, an online store has to provide access to its customers, and therefore has significant vulnerabilities by definition. Second, no institution can afford to be completely secure—if that is even possible. So, the risk management area is a balancing act; one that requires careful technical and cost/benefit analysis.
As such, listing an organization's vulnerabilities isn't good enough. Instead, it is critical to understand three other factors:
- The potential cost in damages of each identified risk/threat (monetary, disruption of business, and loss of trust by customers, vendors, and other associates)
- The probability of the each identified risk to occur (which changes over time)
- The means and costs of protection (or mitigation) from the threat
When you have thoroughly analyzed each threat, you can prioritize the organization's efforts in protecting against or mitigating the threats.
Maybe just as important as performing a risk analysis is understanding the organization's risk appetite (or risk aversion). The organization needs to understand how much risk it is willing to take, along with what types of damage are tolerable and intolerable. And, it is also critical to understand how much the organization can afford to protect against the threats. The organization's lawyers need to be engaged to identify and evaluate potential litigation risks.
Internal risk comes from three sources: the technology, the organization's standard procedures, and the staff. All of these change constantly, so security planning and policy development is a non-stop process. The technology (software and hardware) is in a constant state of flux. Although often overlooked, the lack of carefully designed policies and operating procedures open up the enterprise to a number of threats and losses. Finally, an organization's own employees, consultants, and vendors are sources of exposure to breaches of security. According to analysts, insiders are responsible for more security violations and breaches than all the other sources of harm combined.
5.2 Developing a Security Plan and Program
An effective security program requires a comprehensive security plan. The security plan should cover all security functions, areas, processes, policies, and procedures. It needs to be specific, clear, and well organized. The activities associated with developing a security plan and program are discussed below.

Figure 2. Security Plan Development
- Define specific security goals—The goal of this activity is to define or frame measurable EIT security goals. These goals must be in complete alignment with the enterprise's security objectives and with the risk tolerance of the organization. They also need to be specific, detailed, and measurable. Security goals should typically cover the following areas:
- Identifying, prioritizing, and addressing security gaps
- Tool purchase and development
- Law and regulation compliance
- Threat detection and response
- Ongoing training and certification for security personnel
- Ongoing training of non-security personnel
- Continuous communication of program goals and potentials for exposures
- Categorize and assess information assets—This activity involves creating a comprehensive catalog of the organization's information assets. Each asset must be evaluated with respect to the value of its information to the organization and the cost of potential damage, whether that damage is due to a leak of information, actual damage to the systems or information, or a lack of availability for a short or extended period of time. In addition, the report should list the acceptable level of exposure to risk for the asset (loss, damage, unauthorized access) and the acceptable constraints that can be placed on the asset by the technology and policies designed to keep it secure.
- Design alternative risk controls—There are a number of alternatives available for protecting information assets. Each alternative has its strengths and weakness with respect to the enterprise's strategic and security goals. Each alternative also has its associated implementation and maintenance costs. By setting priorities and managing costs, the team can build an effective security architecture that contains routine electronic and process-based actions.
- Implement and communicate selected controls—Implementing the controls is often more than just installing security software and establishing security-related policies and procedures. Often general controls must be customized for the specific threat and information asset that they are meant to address. In addition, the controls need to be an integral part of the processes or assets that they support. Simply adding them on and expecting them to be used or followed is wishful thinking.
- Test controls—The organization needs to create an assessment method to evaluate the effectiveness of the implemented controls. These come in the form of prearranged tests and reviews that ensure that the controls are protecting the assets as designed. The testing process should also assess whether policies and procedures are being followed by employees. If an organization doesn't test its controls, it can't certify to any governing body that its controls are effective. In some industries, being able to demonstrate that you are in compliance is critical. For other industries, it's just good business.
- Detect and address security incidents—Finally, an organization needs to detect when security breaches occur and deal with those breaches in an effective and efficient manner. We discuss this subject at length in the Security Incident Response and Management section.
5.3 Ongoing Security Planning Cycle
"The risk management process is a continuous process for systematically addressing risk throughout the lifecycle of a system, product, or service."
~ ISO/IEC 16085:2006 Systems and software engineering—Lifecycle processes—Risk management, 3.12
Because security is now an aspect in the lifecycle of all systems and services provided by an organization, the planning cycle is never over. Each time an organization fields a new capability, security must be considered. Even when maintaining an old system, security planning is involved. In addition, new threats and vulnerabilities are regularly identified, which requires an organization to constantly update their security capabilities.
The result is that organizations need to continuously take inventory, analyze, design, implement, and test their security system—and update the security plan accordingly. This ongoing process makes it essential to implement some kind of continuous improvement program that allows the organization to adapt to change quickly. This activity needs to be part of the overall security program.
Here are some of the most often used processes.
- Deming cycle (plan, do, check, act)—The PDCA process was incorporated into ISO/IEC 27001:2005 as the preferred risk management processes. This cycle contains four steps:
- Plan phase—Design the ISMS by assessing information security risks and then selecting the appropriate controls for the risks.
- Do phase—Implement and use the security controls.
- Check phase—Review and evaluate the effectiveness and efficiency of the ISMS.
- Act phase—Modify the ISMS as necessary to improve effectiveness or efficiency.
- Six Sigmas DMAIC (define, measure, analyze, improve, control)—This process refines the Deming cycle and is a data-driven quality strategy for improving a process that is often customized for use by security departments.
- Information Security Forum's SOGP (Standard of Good Practice)—This document is a comprehensive, business-focused guide to managing information security risks. One of its sections discusses good practices with respect to security risk management. It also discusses the details of policies, standards, and procedures.
6 Security Education and Training
An essential part of any ISMS is the organization's security training program. These training programs often come in several different levels that match the sophistication and job function of employees. Security training is not just for those individuals actively involved in designing, implementing, and monitoring the security program—it is for all employees. A large number of security breaches are linked to employees' actions. Security threats cannot be totally addressed through security software and hardware—the human factor has to be addressed. Employees need to modify their standard operating behavior to reduce overall exposure to attacks—new security policies and procedures must be followed. As a result, security training programs need to be comprehensive and applied throughout the workforce. A good source of free online video training is at https://www.csiac.org/series/information-awareness-videos/.
Security training programs need to instruct even low-level workers about their security responsibilities and teach them about information security processes and procedures that are appropriate for their job function. These programs are often referred to as security awareness programs. Among other topics, security awareness programs cover how to avoid threats and attacks associated with:
- Email and IM
- Browsers
- Inadequate passwords
- Mobile devices
- Lack of encryption
Not only do employees need to be taught about the vulnerabilities associated with different tasks, such as reading email, but they also need to be given the tools to minimize the threats. A program should exist to keep the training and the tools up to date as part of the ongoing organizational processes. In addition, non-technical employees need to be motivated to follow the enterprise's security procedures; otherwise, they will not do so.
Training for more technical individuals needs to address the technical aspects of preventing security breaches. For example, security training for the programming staff should include information about how to conduct a code review to identify vulnerabilities in the code.
The training for the security team needs to be the most comprehensive, and it also needs to be continuous. As attacks become more sophisticated, the training level of the security staff needs to keep up. The constant change in every area of security is what drives specialization. The advanced training classes often focus on only one area, such as data security or defense against denial of service attacks.
The training function needs to be accountable and reviews need to be conducted regularly. Measure the effectiveness of the training from both a programmatic and individual perspective. When the effectiveness is found to be lacking, updates need to be made immediately.
7 Assets, Risks, and Threat Protection
When goals are defined, it is time to take inventory. There are large numbers of EIT assets that need to be categorized and evaluated for potential risk. Often the EIT security arena is divided into facilities, computer hardware, telecommunications, networking, software, and information (data), better enabling the organization to identify each asset and evaluate the potential of the asset as a security risk. Individuals with security risk identification skills specific to each area need to be involved in the activity.
When each asset is identified, the team needs to enumerate the risks associated with the asset. Some assets may only have a couple of risks or potential threats associated with them, while others may have hundreds of potential risks. For each risk, the team needs to evaluate the cost of a security breach for that asset in concert with the asset owner and stakeholders.
7.1 Facility Security Evaluation
Facility security is part of most companies' plans and this has been the case for years. These plans are usually perimeter based. Using this mindset, the organization can consider everything in a defined area as one large asset. You might think that a standard facilities security plan would be good enough, but an alarming number of cyberattacks occur inside the defined security perimeter of a standard physical security plan.
To counter these attacks, facility security plans need to be changed from being perimeter based to being area based. All assets within an area, even the non-tangible information assets, need to be protected. Therefore, the physical security planning process needs to be fully integrated with those steps that protect the information assets themselves. The facility security plan needs to:
- Clearly identify and define protected areas; define a layered defense.
- Regulate access to protected spaces 24 x 7.
- Protect against physical intrusion into any protected space.
- Protect sensitive equipment as well as equipment that contains sensitive information, including portable devices.
- Protect sensitive materials on desks, walls, and so on, ensuring that they are always located in a safe place.
- Clearly define appropriate responses to any identified security breaches.
Asset identification processes and the security plan need to take into account not only threats associated with unauthorized entry of an individual, but also damage caused by man-made or natural disasters. All of these threats need to be identified and safeguards/techniques need to be identified to protect against them (see the Disaster Preparedness chapter).
7.2 Telecommunications
Telecommunications networks and other pieces of infrastructure are rapidly being assimilated into the Internet. Today, systems such as electrical grids and traffic systems are now accessible to users, regardless of their location, with a few clicks of a mouse. These tremendous capabilities are not without consequences. For example, a hacker can launch attacks capable of denying voice service to cellular telecommunications networks in major cities, or use telecommunications for turning off utilities in the smart grid. In times of emergency, when such networks are essential in saving lives, such attacks can be extremely dangerous.
When evaluating assets, and looking for risks and mitigation techniques, the telecommunications team needs to consider the following security techniques:
- Authorization—Requiring authorization to help prevent unauthorized interceptors from accessing telecommunications in an intelligible form while still delivering content to the intended recipient
- Cryptosecurity—Communications security that results from the use of cryptosystems to ensure message confidentiality and authenticity
- Emission security—The protection to deny unauthorized personnel information due to interception and analysis of emanations from cryptographic equipment, information systems, and telecommunication systems
- Transmission security—The security that protects transmission from interception and exploitation by means other than cryptanalysis, such as frequency hopping and spread spectrum
- Physical security—All physical measures necessary to safeguard classified equipment, material, and documents from access
7.3 Network and Internet Security
Although similar to telecommunications security, network and Internet security present additional assets and risks. The open nature of the Internet puts all users at risk of attack. It also puts all servers, computers, and other devices that interact with the Internet at risk. As a result, carefully documenting all network settings, proxies, licenses, VPNs, and the assets on each LAN or network segment is critical. Each must be examined for vulnerability.
Understanding where all the assets are and how open they are to network traffic is difficult, but necessary to assess the true threat risk for the asset. The team needs to be able to understand the potential risks of denial of service or phishing from any given device on not only that device, but the rest of the assets on that part of the network.
In addition, it is important to understand the needs of users for network and Internet use. If users don't need to have access to the Internet, many issues become irrelevant. Some enterprises set up separate network access routes for employees to use so that access from a secure intranet is impossible.
7.4 Computers and Mobile Devices
Each computational device needs to be evaluated. Although we most often think of threats associated with software, hackers can attack the devices themselves either via theft, electronic intrusion, and physical damage. The security plan needs to protect hardware and other devices from all these kinds of threats.
To understand what threats apply, collect detailed information about each piece of hardware, such as:
- Operating system version
- Internet browser version
- Asset usage and users of the asset
- Applications running on the asset
- Peripherals used
This information helps determine what threats need to be considered.
7.4.1 Mobile Device Security
Mobile devices have become so powerful and well integrated into business operations that they must be treated like any other information system. The data on them often is as sensitive as that on data servers and workstations. In addition, the mobility of the devices allows the device to access the Internet nearly anywhere, and also makes them both easy and desirable to steal.
The EIT security staff needs to understand what devices are being used, where they are going, and what applications and data they contain. Staff also need to have controls in place so that unauthorized mobile devices cannot access data stores. Understanding the risks allows the security team to determine what type of security software needs to be installed, and what measures need to be taken to protect sensitive information. Because of the ubiquitous nature of mobile devices, various mobile device management (MDM) suites have been created to centralize controls. MDM can provide risk mitigation (such as the remote wipe of a mobile device) or policy enforcement (such as device encryption) without requiring security staff to individually configure each device.
7.5 Application and App Development Security
Application security includes those measures taken within the code to prevent security gaps whether due to flaws in the design, implementation, deployment, or maintenance processes associated with the application.
As with all the other areas, it is important to take inventory of your software assets so that you know the potential threats due to the functionality of the systems. As organizations field software, the security of the software asset is not complete without consideration of the software itself, the host, connected devices, and the network.
Through the years, many techniques and development lifecycles (e.g., Microsoft SDL, OWAP CLASP, Cigital touchpoints) have been developed (see Improving Web Application Security [4]) that include patterns and techniques to help identify the types of attacks to which an application is vulnerable. There are many categories of attacks on apps that have been identified, including:
- Software tampering (changing, substituting, or extending code)
- Authentication attacks (credential theft, brute force attack, cookie replay)
- Authorization attacks (data tampering, elevation of privileges)
- Cryptographic attack (encryption breaking due to poor key management or weak encryption)
- Session takeovers (session hijacking, session replay)
- Sensitive information attacks (eavesdropping, data tampering, accessing sensitive data)
Lists of vulnerabilities can be found in a number of sources, including OWASP Tops 10 [11], SANS Tops 25 [12], and CVE [13].
Mobile applications are even harder to protect than workstation-based applications. Weakness in mobile application security can come from many sources, but the largest endemic risk is from the mobile platform itself. A vulnerability in the mobile platform can impact the confidentiality, integrity, and availability of all applications on a device or a fleet of devices. In addition, mobile application stores provide a supply-chain risk. A user could potentially download an application for which the user does not have the correct level of access, putting their device at risk. [9] [10]
There are several strategies that programmers can use that can enhance mobile app security, such as using stronger authentication and authorization, tying processes to user IDs, and ensuring transport-layer security. There are many sources available that discuss how to build security into applications. [8]
7.6 Data Security
Although related to all the other levels of assets, a security plan needs to consider some individual data items as assets themselves. It doesn't matter how the hacker gets into the database (hardware, software, network, or physical access), the fact that sensitive information, such as social security, telephone, and credit card numbers are accessed is extremely damaging to the enterprise.
The data security team needs to understand which elements in the database are particularly sensitive or critical for operations. There are a whole host of means by which data systems can be compromised and each of these potential threats needs to be analyzed and mitigated.
- Theft of storage element or media
- Loss of a storage element or media
- Loss of data
- Tampering of data
- Unauthorized privileged access of data
- Media configuration changes (intentional, malicious, or not)
- Denial of service/access
- Traffic/communications monitoring
8 Designing Controls
There are a host of known designs, techniques, tools, and consultants that can help design security controls. Many books are written about the topic. And, yet, this is a very difficult process. There needs to be balance between providing the best security against potential threats, while still providing the functionality required by the business requirements of the enterprise. Some risks can be tolerated if they are required to run the business; for example, the risks associated with running an online store. The cost of implementing a mitigation technique also needs to be carefully evaluated, because the cost of the solution could be higher than the potential cost of the risk. Often, a security policy or manual procedure is the most cost-effective solution available.
Knowing different security models and techniques can guide the security team in designing and selecting the best mitigation technique to use. We cover some of those design models and considerations here.
8.1 Security Policy and Procedure Development
Effective security policies that are followed throughout the enterprise are another essential component of the security program. These policies need to be carefully designed, well-communicated and monitored, and must cover a number of areas:
- Access and overreaching policies—These policies regulate email, password setting, acceptable use of resources, encryption key usage, and even security response and disaster-recovery processes.
- Computer and server security policies—This area of policies covers issues such as server security, workstation security, software installation, facilities security, information logging, database access and credentials, and technology disposal.
- Network security policies—These policies cover just about any risk associated with the networks that can be regulated by a policy, such as remote access, router and switch security, and wireless communication.
- Application security policies—These policies cover topics such as access and control, the delineation of responsibilities for access to files and data, web application security, mobile device app security, and security tools. These policies might also regulate the use of open-source software and third-party code, and require that such code be contained in a secure software repository. In some organizations, these policies require cryptoroutines and scans that test for vulnerabilities with in the code.
The area of security policies is a difficult one for most CIOs. A lot of help is available for forming security policies that protect the organization; however, getting a policy to be followed throughout the enterprise can be extremely difficult. Compliance with security policies can be distressingly low in certain areas, such as policies associated with mobile device use and personal browsing on corporate workstations. This trend makes training of and frequent communication to all employees an essential part of policy enforcement, as is motivating the average employee to follow the rules.
8.2 Security Architecture and Models
A security model is a representation of the enterprise's rules or policies about security, especially data access. The models don't tell an organization specifically how to design their security system. Instead, models provide a perspective on how to look at security for a system. A particular architecture might use several security models. There are many different security models and we cover a few here.
- State machine model—To verify the security of a system, the state of the system is used. Therefore, all current permissions and accesses to information systems are captured. Systems that employ this model are in a secure state all the time.
- Bell-LaPadula model—This model was developed to address the leakage of classified information. It was the first rigorous model of a multilevel security policy used to define a secure state machine, and modes of access to information. In this model, users with different "clearances" have access to different levels of information.
- Biba model—This model is similar to the Bell-LaPadula model. It addresses the integrity of data that is threatened when users at lower security levels are able to write to objects at higher security levels.
- Clark-Wilson model—This model focuses on preventing authorized users from making unauthorized modifications to data, or committing fraud and errors within commercial applications. Rather than confidentiality, this model protects the integrity of the data.
- Information flow model—This type of model looks for insecure information flow. Insecure information flow can occur at the same level or between different levels until a restricted operation is attempted.
- Non-interference model—This model ensures that any actions that take place at a higher security level do not affect or interfere with actions at a lower level. This model doesn't care about the flow of information, but what the user knows about the state of the system, especially about actions taken at a higher level.
- Brewer and Nash model—This model is designed to provide access controls that can change dynamically depending on the user's previous actions. It prevents access to data that might be considered a conflict of interest. This model is used often in financial institutions.
- Graham-Denning model—This model creates rights for users that are associated with operations that can be executed on objects. In essence, it defines the "rights" that a user has to perform actions.
- Harrison-Ruzzo-Ullman model—This model specifies how access rights can be changed. It also specifies how objects can be created and deleted.
8.3 Classification for Levels of Access
The area of access management is complex and can generate debates on specific details during the implementation of who can see what data and when. The how is often dictated by identity management systems already in place within the enterprise. However, these identity management systems often have the flexibility to design multiple discretionary frameworks, such as role-based and user-based security models. Access control policies need to take all forms of access control into consideration.
One of the first functions of developing a security model is to determine the categories of users needed to ensure data is accessed on an as-needed basis. Role-based access control is a common method used for access control. Here are some of the most common roles:
- Administrators—Administrators' capabilities can range from database administrators to file or storage administrators. However, software developers and network administrators may often have cross-domain responsibilities that require a high level of access. This level includes access to create, modify, and delete data, files, and configuration settings.
- Power/super users—Power/super users is an optional level of security access that provides highly knowledgeable functional users with the authorization to access more service functions that their job function requires. This level adds mentoring or coaching to the duties of this role. Generally this type of user has access to all areas of a service if they are responsible for assisting or training others in that service. Another term for this type of user is functional lead.
- Primary functional users—Primary functional users have application and service authentication and access rights allowing them to perform the business functions needed to complete their daily tasks. These are end users that add and update records with the highest frequency of any user group.
- Secondary (casual) user types—Secondary or casual users are roles such as auditors and managers, or those given user IDs for one-time or temporary access, such as contractors or consultants. These roles usually have read-only access or may have access to very limited functions, such a reporting or expense submission.
- Anonymous/read-only users—A final category is anonymous access to public information or read-only employee information, for users who need access to data, such as benefit or corporate reporting information.
9 Implementing and Maintaining Selected Security Controls
After the security controls are designed, they need to be put into operation. Implementing security controls is just like constructing and implementing any other EIT solution. The implementation has to be carefully planned and integrated into already existing hardware, software, processes, polices, and procedures. Luckily, it is usually the case that you can implement just one mitigation technique at a time, which means an organization can roll out a security plan in pieces, according to the priorities it has established. For example, one month an organization can implement new password policies and procedures. The next month, it upgrades all servers to a new version of the OS that contains new security features. And, one would expect that the security testing function is continuously improving over time.
Each EIT department plays a role in integrating, monitoring, and maintaining the security plan.
- System administration—This department usually rolls out new versions of the operating systems and software, and ensures that the operational environments are configured in accordance with approved baselines and that all security updates are installed on devices in a timely manner.
- Network services—It is their role to ensure that the network set up follows the security plan. Network services also need to monitor the network for any illegal traffic.
- Customer service and technical support—This group's role is to help individuals follow the security policies and procedures. Often this includes teaching both in classroom base sessions as well as individual handholding.
- Data administration and knowledge management—Data and knowledge administrators need to make sure that all data security controls are implemented on all databases and knowledge bases. In addition, they need to monitor databases constantly for any form of breach.
- Systems security analysis—Systems security analysis is an ongoing concern. This group is in charge of detecting security breaches.
10 Security Monitoring, Accountability, and Testing
Testing security measures is an essential part of a security plan. You cannot verify that the plan is working unless you test whether the security measures (software, policies, and procedures) are working as the plan specifies. Unfortunately, even if the security system tests run without finding flaws, there is no guarantee that it is free of vulnerabilities. It is nearly impossible to test for all possible vulnerabilities; hackers seem to find new ones every day.
To test a security system, you have to design the tests to cover the CIA triad (confidentiality, integrity, availability). In addition, the tests specifically need to cover authentication, authorization, and non-repudiation. Tests must cover the different areas of vulnerabilities, such as network security, system software security, client-side application security, and server-side security.
Testing and then forgetting doesn't work in security. The plan should provide required frequencies for conducting different tests on the system and for reporting the results. The security team needs to monitor the system to make sure that security measures (such as network settings) have not been changed and that vulnerabilities have not appeared. This is an ongoing maintenance issue, not a one-time verification of a system.
10.1 Security Accountability
A major component of every security system is accountability. In this arena, accountability is the ability to trace all the actions performed on a device, within a process, or by a user. Techniques such as unique user identification (UUID) and authentication strongly support accountability.
Accountability is necessary to ensure that any attempted or committed security violation can be traced to the device on which it occurred and to the individual that committed the breach. Accountability enables the EIT organization to find those individuals that need to be held responsible for the damage. Without accountability, security monitoring has little purpose.
10.2 Vulnerability Testing Categories and Levels
As with all testing, the three standard categories of testing also apply to security: white box, gray box, and black box. White box testing is done with full knowledge of the system being tested—you know what you are looking for. Gray box testing is done with partial knowledge of the system. Black box testing is done with no knowledge of the system being tested, and testing for penetration is primarily black box testing. There are a number of testing phases or levels that mature security tests have. Some of them are automated and some are done by hand. Here are some of the most common levels:
- Discovery—This phase identifies information systems and determines the technologies that are in use. It also determines, hosts, ports, and application entry points. A discovery process might find deprecated versions of software or firmware that are prone to attack, or it might find newly opened ports or entry points.
- Vulnerability scan—This scan identifies known security issues with automated tools that look for specific conditions or situations that are known to indicate vulnerabilities. These scans can be run with or without credentials (which helps determine what parts of the enterprise can be accessed without an authorized login).
- Vulnerability scans—These scans can be manual or automated, and typically test for secure transmissions protocols, authentication vulnerabilities, session management vulnerabilities such as cookie scope and session termination timeouts, authorization vulnerabilities, data or file input vulnerabilities, and error-handling defects, among others.
- Penetration tests—These tests simulate an attack by a malicious hacker. Typically, these tests are performed by individuals who use complicated methodologies and problem-solving skills to penetrate an organization's security measures. These tests go beyond what automated tools are capable of doing.
- Security review—This review verifies that the enterprise's policies and procedures are in place and are being used systematically throughout the organization. In addition, the reviewers need to verify that any required industry and governmental standards are being applied to each information system component.
When the series of tests is done, the team typically performs a series of risk assessments and audits. The team considers each finding and determines the seriousness of the vulnerability. The team might determine that in this context, an identified vulnerability is actually a false positive. At times, the team might even manually reproduce a vulnerability that was found with an automated system to verify the exposure. The resulting assessment report often lists the vulnerabilities by their seriousness and potential cost to the enterprise.
11 Security Incident Response and Management
Managing security incidents or events is just a special case of computer system or network management. The goal is to have a well-understood and predictable response to potentially damaging intrusions or events. There are a number of recommended incident management procedures that one can find with a simple search, but most are minor variations on a particular theme. In the discussion below, we have included the activities that are generally recommended and commonly included in an incident response plan. [15]
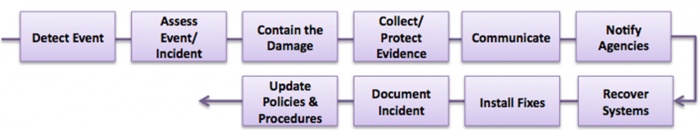
Figure 3. Incident Response Plan
11.1 Detecting the Event
Detecting a security breach is often harder than it seems. Most companies don't know that they have been breached. The ones that do often find out days, weeks, or even months after the attack—just read about Target and their experience. They found out about the attack about a month after it occurred, despite their high-end antihacking operation. Event detection is difficult for two reasons. First, detection has become a far more complex task due to the increased size of attack surface, as systems have gotten more highly integrated and complex. Second, many companies are not using state-of-the-art detection software and programs.
As a result, detection is very difficult and detection technology is usually lagging behind the level of the most advanced hackers. In addition, most enterprises use detection methods that are only partially effective, at best. They don't keep up with the state-of-the-art detection software. Also, most enterprises do not perform a thorough analysis of the potential avenues of attack. If you don't understand where the attacks can occur, you can't put monitors in to detect them.
There are two great examples of this. First, in the case of the attacks on Target, there were point-of-sale terminals that were not being monitored as a point of attack. Second, in gas station skimmer attacks, credit card numbers are stolen by inserting a hardware device into the gas pump. The device actually powers itself with the pump's own electricity. The designer of the pump never considered this point of entry for an attack.
Over the last several years, detection methods have gone from signature or rule based to being behavior and analytics based. Most of the damage is done after the initial breach of the perimeter security, such as the corporate firewalls. So, it is now critical for organizations to have technology that can detect breaches (foreign activity) that occur behind the firewall. And these breaches often last for hours. There is significant evidence that one of China's cyberespionage units attacked 141 victim companies and stole multiple terabytes of data in attacks that lasted at least a year!
11.2 Assessing/Analyzing the Event
When the event has been detected, the security team needs to assess the event quickly to keep the damage from spreading. The team needs to determine whether the event is malicious or not and what type of event is it. It might be a denial of service, an access attack, or a reconnaissance attack, for example.
The team needs to determine as best as possible how the breach occurred. The attack could have come from outside the organization or from within. It could have been a piece of malware or an Internet worm running on one of the internal systems. They need to determine the particular system that was breached.
A quick assessment of what has been affected needs to be made to determine what data, software, or hardware has been breached or damaged. The initial assessment also needs to determine the severity of the attack. It could be just a nuisance, or it could be a serious threat to the business, staff, vendors, or customers.
11.3 Containing the Damage
After a basic assessment has been made, you need to take steps to contain the damage. What systems need to be brought down? Do workstations need to be confiscated? Does the organization's connection to the Internet need to be broken? Can you just limit third-party activity? Do you need to shut down wireless networks? Do you need to change passwords throughout the enterprise as fast as possible?
11.4 Collecting and Protecting Evidence
If the event is malicious, especially if it causes significant damage, it is critical to save the evidence. Obviously, the team needs to identify the type and severity of the compromise, and where the attack came from. The team also needs to save critical data to be used for forensic purposes.
The organization's team might not have the capability to collect and protect the evidence; however, there are a number of companies that specialize in helping organizations with this process.
It is important to note that collecting and protecting the evidence usually slows down the recovery process; however, for a significant security breach, there is no question that it is the right thing to do.
11.5 Communicating to Those Affected
It is critically important to communicate to those individuals who are affected by the event. This might mean sending an email to an employee because there is malware on their workstation. It might mean sending out email or letters to thousands of customers, because their credit card data has been stolen. And in most cases, it is critical to notify management. Incident response plans should include a table that indicates who should be notified given the type and complexity of the security incident.
11.6 Notifying Appropriate Agencies
If the event is serious, the appropriate agencies need to be informed of the event. Contacting the organization's lawyer is likely the best first step. Determining the correct law enforcement agency to call is not always straightforward. In the USA, the FBI and Homeland Security are obvious choices for a foreign attack. For each country, the agencies are different, and it is important to determine which agencies the security team should call under particular conditions. All appropriate contact information needs to be part of the security plan.
Many organizations now have insurance coverage for cyberattacks. The corporate lawyer should know about that coverage.
11.7 Recovering Systems and Installing Permanent Fixes
At some point, when the emergency is over and the incident is reported, it is time to figure out how to get all of the enterprise's systems back in running order, as described in the Disaster Preparedness chapter. This might require changing software or hardware. It might require running malware-removal software throughout the organization. It might also require having everyone change passwords throughout the enterprise.
Part of this system-recovery process should also involve putting in a permanent fix for the breach that was identified. This could mean installing patches to existing software or hardware, installing new intrusion-detection software, changing VPN protocols and procedures, or changing how sensitive data is stored. Often companies increase the level of encryption of the sensitive data. In any case, this is a time to plug the hole that was breached, and possibly plug a few others at the same time.
11.8 Compiling Incident Documentation with Damage Assessment
As with most catastrophic events, it is important to document the event thoroughly, so that you can treat it as a lesson learned. Every step of the event, the analysis, and the fixes should be documented and kept with the security plan. Along with that, the damage caused and the cost of repairing the damage should be calculated and documented.
According to the New York Times [7], the attack on Target cost the company a reported $148 million in direct costs, and cost financial institutions $200 million. In addition, Target's move to the chip-and-pin system, which is a more secure method for dealing with credit card data cost Target an additional $100 million, although the move to chip-and-pin was not a direct result of the breach. The company also spent $61 million in antibreach technology shortly following the attack. Even beyond those direct costs, profits fell 46 percent in the quarter following the announcement of the attack.
11.9 Review Incidents, and Updating Policies and Procedures
Simply identifying the things that could have been done better with respect to the incident is not enough. It is critical for the enterprise to review current policies and procedures, and make changes that decrease security risks. These changes can be as simple as how often employees are required to change their passwords. It could be changes in VPN access rules, or it could be inserting a file encryption mechanism into many data transfer processes.
12 Summary
EIT security is a major area of concern for CIOs. The area is changing on a daily basis. The attacks are becoming more frequent and more sophisticated. Often the security breaches are from within, whether intentional or not.
There is no way that a large enterprise can protect against all threats. Instead, an organization has to use its security resources in the most efficient way possible. To do that, the organization needs to inventory its computing assets, assess the risks and the related costs/damages of a security breach, and then make hard decisions about which risks to focus on and which to handle with less-rigorous methods, such as policies and procedures.
It has become more and more important for organizations to understand their risk appetites, and truly weigh the potential security risks with providing new services and functionality to customers, vendors, and employees.
13 Key Maturity Frameworks
Capability maturity for EIT refers to its ability to reliably perform. Maturity is measured by an organization's readiness and capability expressed through its people, processes, data, and technologies and the consistent measurement practices that are in place. See Appendix F for additional information about maturity frameworks.
Many specialized frameworks have been developed since the original Capability Maturity Model (CMM) that was developed by the Software Engineering Institute in the late 1980s. This section describes how some of those apply to the activities described in this chapter.
13.1 IT-Capability Maturity Framework (IT-CMF)
The IT-CMF was developed by the Innovation Value Institute in Ireland. This framework helps organizations to measure, develop, and monitor their EIT capability maturity progression. It consists of 35 EIT management capabilities that are organized into four macro capabilities:
- Managing EIT like a business
- Managing the EIT budget
- Managing the EIT capability
- Managing EIT for business value
Each has five different levels of maturity starting from initial to optimizing. The three most relevant critical capabilities are information security management (ISM), risk management (RM), and personal data protection (PDP).
13.1.1 Information Security Management Maturity
The following statements provide a high-level overview of the information security management (ISM) capability at successive levels of maturity.
| Level 1 | The approach to information security tends to be localized. Incidents are typically not responded to in a timely manner. |
| Level 2 | Defined security approaches, policies, and controls are emerging, primarily focused on complying with regulations. |
| Level 3 | Standardized security approaches, policies, and controls are in place across the EIT function, dealing with access rights, business continuity, budgets, toolsets, incident response management, audits, non-compliance, and so on. |
| Level 4 | Comprehensive security approaches, policies, and controls are in place and are fully integrated across the organization. |
| Level 5 | Security approaches, policies, and controls are regularly reviewed to maintain a proactive approach to preventing security breaches. |
13.1.2 Risk Management Maturity
The following statements provide a high-level overview of the risk management (RM) capability at successive levels of maturity.
| Level 1 | The risk management program and framework are considered in an ad hoc manner, if at all. No risk-related roles are defined, or they are defined in an ad hoc manner. Risks are not actively or systematically managed. |
| Level 2 | The risk management program sits within the EIT function, and a basic framework is established. Responsibility and accountability for risk management are assigned to persons/roles in the EIT function. Some basic risk management approaches are established but these may not be consistently adhered to. |
| Level 3 | The risk management program and supporting framework are established and consistently referenced in the EIT function and some other business units. Responsibility and accountability for risk management are assigned to dedicated persons/roles in the EIT function and other business units. Most risk management activities adhere to defined and documented approaches. |
| Level 4 | The risk management program and framework are established through the cooperation of, and in consultation with, the EIT function and the rest of the business. The risk management of EIT is integrated into wider ERM practices. Explicit risk management responsibility and accountability are assigned to employees across the organization. Compliance with the approaches, principles, and guidance for all risk management activities is mandated and enforced organization-wide. |
| Level 5 | The risk management program and framework are continually refined and updated, and involve regular cooperation with business ecosystem partners. Responsibility and accountability for risk management are dynamically assigned to the appropriate organization level, and regularly reviewed. Risk management approaches, principles, and guidance are continually reviewed and improved based on changes in the risk landscape, and learning from previous risk incidents. |
13.1.3 Personal Data Protection Maturity
The following statements provide a high-level overview of the personal data protection (PDP) capability at successive levels of maturity.
| Level 1 | There is limited to no understanding of personal data protection obligations, and enforcement is ad hoc. |
| Level 2 | The EIT function has started rolling out personal data protection policies and procedures to meet high-priority legislative, regulatory, EIT and business needs. The risks associated with holding personal data have begun to reduce. |
| Level 3 | The management of personal data protection follows standardized policies and procedures across the EIT function and some other business units for most priority legislative, regulatory, EIT and business needs. The organization's reputation for managing personal data is growing. |
| Level 4 | The management of personal data protection follows comprehensive policies and procedures across the entire organization for all necessary legislative, regulatory, EIT, and business needs. The organization has a good reputation for managing personal data. |
| Level 5 | There is a culture of proactive personal data protection across key business ecosystem partners. This is continually reviewed to ensure that the likelihood of personal data privacy violation remains low. |
14 Key Competence Frameworks
While many large companies have defined their own sets of skills for purposes of talent management (to recruit, retain, and further develop the highest quality staff members that they can find, afford and hire), the advancement of EIT professionalism will require common definitions of EIT skills that can be used not just across enterprises, but also across countries. We have selected three major sources of skill definitions. While none of them is used universally, they provide a good cross-section of options.
Creating mappings between these frameworks and our chapters is challenging, because they come from different perspectives and have different goals. There is rarely a 100 percent correspondence between the frameworks and our chapters, and, despite careful consideration some subjectivity was used to create the mappings. Please take that in consideration as you review them.
14.1 Skills Framework for the Information Age
The Skills Framework for the Information Age (SFIA) has defined nearly 100 skills. SFIA describes seven levels of competency that can be applied to each skill. However, not all skills cover all seven levels. Some reach only partially up the seven-step ladder. Others are based on mastering foundational skills, and start at the fourth or fifth level of competency. SFIA is used in nearly 200 countries, from Britain to South Africa, South America, to the Pacific Rim, to the United States. (http://www.sfia-online.org)
SFIA skills have not yet been defined for this chapter.
| Skill | Skill Description | Competency Levels |
|---|---|---|
| Information assurance | The protection of integrity, availability, authenticity, non-repudiation, and confidentiality of information and data in storage and in transit. The management of risk in a pragmatic and cost-effective manner to ensure stakeholder confidence. | 5-7 |
| Information security | The selection, design, justification, implementation, and operation of controls and management strategies to maintain the security, confidentiality, integrity, availability, accountability, and relevant compliance of information systems with legislation, regulation, and relevant standards. | 3-7 |
| Penetration testing | The assessment of organizational vulnerabilities through the design and execution of penetration tests that demonstrate how an adversary can either subvert the organization's security goals (e.g., the protection of specific intellectual property) or achieve specific adversarial objectives (e.g., establishment of a covert command and control infrastructure). Pen test results provide deeper insight into the business risks of various vulnerabilities. | 4-6 |
| Digital forensics | The collection, processing, preserving, analyzing, and presenting of computer-related evidence in support of security vulnerability mitigation and criminal, fraud, counterintelligence, or law enforcement investigations. | 4-6 |
| Security administration | The provision of operational security management and administrative services. This typically includes the authorization and monitoring of access to EIT facilities or infrastructure, the investigation of unauthorized access, and compliance with relevant legislation. | 1-6 |
14.2 European Competency Framework
The European Union's European e-Competence Framework (e-CF) has 40 competences and is used by a large number of companies, qualification providers, and others in public and private sectors across the EU. It uses five levels of competence proficiency (e-1 to e-5). No competence is subject to all five levels.
The e-CF is published and legally owned by CEN, the European Committee for Standardization, and its National Member Bodies (www.cen.eu). Its creation and maintenance has been co-financed and politically supported by the European Commission, in particular, DG (Directorate General) Enterprise and Industry, with contributions from the EU ICT multi-stakeholder community, to support competitiveness, innovation, and job creation in European industry. The Commission works on a number of initiatives to boost ICT skills in the workforce. Version 1.0 to 3.0 were published as CEN Workshop Agreements (CWA). The e-CF 3.0 CWA 16234-1 was published as an official European Norm (EN), EN 16234-1. For complete information, see http://www.ecompetences.eu.
| e-CF Dimension 2 | e-CF Dimension 3 |
|---|---|
| D.1. Information Security Strategy Development (ENABLE) Defines and makes applicable a formal organizational strategy, scope, and culture to maintain the safety and security of information from external and internal threats, i.e., digital forensic for corporate investigations or intrusion investigation. Provides the foundation for information security management, including role identification and accountability. Uses defined standards to create objectives for information integrity, availability, and data privacy. | Level 4-5 |
| E.8. Information Security Management (MANAGE) Implements information security policy. Monitors and takes action against intrusion, fraud, and security breaches or leaks. Ensures that security risks are analyzed and managed with respect to enterprise data and information. Reviews security incidents, and makes recommendations for security policy and strategy to ensure continuous improvement of security provision. | Level 2-4 |
14.3 i Competency Dictionary
The Information Technology Promotion Agency (IPA) of Japan has developed the i Competency Dictionary (iCD) and translated it into English, and describes it at https://www.ipa.go.jp/english/humandev/icd.html. The iCD is an extensive skills and tasks database, used in Japan and southeast Asian countries. It establishes a taxonomy of tasks and the skills required to perform the tasks. The IPA is also responsible for the Information Technology Engineers Examination (ITEE), which has grown into one of the largest scale national examinations in Japan, with approximately 600,000 applicants each year.
The iCD consists of a Task Dictionary and a Skill Dictionary. Skills for a specific task are identified via a "Task x Skill" table. (See Appendix A for the task layer and skill layer structures.) EITBOK activities in each chapter require several tasks in the Task Dictionary.
The table below shows a sample task from iCD Task Dictionary Layer 2 (with Layer 1 in parentheses) that corresponds to activities in this chapter. It also shows the Layer 2 (Skill Classification), Layer 3 (Skill Item), and Layer 4 (knowledge item from the IPA Body of Knowledge) prerequisite skills associated with the sample task, as identified by the Task x Skill Table of the iCD Skill Dictionary. The complete iCD Task Dictionary (Layer 1-4) and Skill Dictionary (Layer 1-4) can be obtained by returning the request form provided at http://www.ipa.go.jp/english/humandev/icd.html.
| Task Dictionary | Skill Dictionary | ||
|---|---|---|---|
| Task Layer 1 (Task Layer 2) | Skill Classification | Skill Item | Associated Knowledge Items |
| Information security operation management (EIT operation control) |
Basic security technology | Information security |
|
15 Key Roles
These roles are common to ITSM.
- Compliance Manager
- Enterprise Architect
- Information Security Manager
- Risk Manager
- Service Design Manager
- Technical Analyst
Other key roles include:
- Chief Information Security Officer
- Data architect
- Data owner
- Operations Manager
16 Standards
- ISO/IEC 27013, Information technology—Security techniques—Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000–1
- ISO/IEC 27000:2016, Information technology—Security techniques—Information security management systems—Overview and vocabulary (this is the general overview to the ISO/IEC 27000 series of over 30 standards on information security management systems, and terms and definitions commonly used in the ISMS family of standards).
- ISO/IEC 27001:2013, Information technology—Security techniques—Information security management systems—Requirements
- ISO/IEC 27002:2013, Information technology—Security techniques—Information security management systems—Code of practice for information security controls
- ISO/IEC 15408:2009, information technology—The common criteria for Information Technology Security Evaluation as an international standard for computer security certification. Establishes the general concepts and principles of EIT security evaluation and specifies the general model of evaluation given by various parts of ISO/IEC 15408, which is its entirety is meant to be used as the basis for evaluation of security properties of EIT products.
- ISO/IEC/IEEE 15026, System and software engineering—Systems and software assurance (4 parts)
- Federal Information Processing Standards (FIPS) 140 series—These publications are computer security standards created by the US government specifically concerning cryptographic modules. FIPS 140-2 defines four levels of security and sets requirements in 11 different cryptographic areas including roles, services and authentication, physical security, design assurance, and cryptographic module ports and interfaces. [14]
17 References
[1] ISO/IEC 27000:2014 definition of "information security." [2] ISO/IEC 27001:2013, Information technology—Security techniques—Information security management systems—Requirements. [3] ISO/IEC 27002:2013, Information technology—Security techniques—Information security management systems—Code of practice for information security controls. [4] J.D. Meier, A. Mackman, S. Vasireddy, et al. Improving Web Application Security: Threats and Countermeasures, http://www.cgisecurity.com/lib/Threats_Countermeasures.pdf, June 2003. [5] IAPP Information Privacy Certification Glossary of Common Privacy Terminology https://iapp.org/media/pdf/certification/CIPP_Glossary_0211updated.pdf, 2011. [6] Information Technology—Security techniques—Privacy framework, ISO/IEC 29100:2011; http://a-infosec.com/2014/01/25/public-available-of-isoiec-291002011-privacy-framework/ [7] Rachel Abrahms, Target Puts Data Breach Costs at $148 Million, and Forecasts Profit Drop, New York Times, http://www.nytimes.com/2014/08/06/business/target-puts-data-breach-costs-at-148-million.html?_r=0, August 2014. [8] What is Build Security In? https://buildsecurityin.us-cert.gov/ [9] Dimensional Research, The Impact of Mobile Devices on Information Security: A Survey of IT Professionals, https://www.checkpoint.com/downloads/products/check-point-mobile-security-survey-report2013.pdf, June 2013. [10] Phil Brit, 10 Trickiest Mobil Security Threats, eSecurity Planet, April 2015. [11] OWASP, Top 10 2013, https://www.owasp.org/index.php/Top_10_2013-Top_10 [12] CWE/SANS, CWE/SANS Top 25 Most Dangerous Software Errors, https://www.sans.org/top25-software-errors/, June 2011. [13] ITU-T, Common vulnerabilities and exposures, http://www.itu.int/ITU-T/recommendations/rec.aspx?rec=11061, April 2011. [14] NIST Federal Information Processing Standards (FIPS) Publications, Feb 2013; http://csrc.nist.gov/publications/PubsFIPS.html. [15] M. West-Brown, D. Stikvoort, KP Kossakowski, et. al., Handbook for Computer Security Incident Response Teams (CSIRTs), MU/SEI-2003-HB-002, Carnegie Mellon University, http://resources.sei.cmu.edu/asset_files/Handbook/2003_002_001_14102.pdf, April 2003. [16] CSO Staff, The security laws, regulations, and guidelines directory, December 2012, http://www.csoonline.com/article/2126072/compliance/the-security-laws—regulations-and-guidelines-directory.html.18 Related and Informing Disciplines
- Physical and facilities security
- Personnel security
- Transportation security
- Retail security
- Manufacturing security
- Insurance and financial services security
- Healthcare security
- Utilities security
- Cryptography
- Code analysis tools
- Logging and tracing
- Biometric authentication
- Copyright and intellectual property protection
19 Additional Reading
DHS: "IT Security Essential BoK, A Competency and Functional framework for IT Security Workforce Development," http://csrc.nist.gov/groups/SMA/ispab/documents/minutes/2007-12/ISPAB_Dec7-BOldfield.pdf
NIST, Special Publication 800-37 (Revision 1), "Guide for Applying the Risk Management Framework to Federal Information Systems," February 2010.

