Strategy and Governance
Contents
1 Introduction
ICT strategic planning defines and communicates goals, assesses their impact on the organization, drives change to achieve those goals, and provides a basis for governing and assessing success. Taking various perspectives (financial, historical, environmental, future projections), a strategic plan is a framework for action and change both vertically and horizontally across the ICT organization. ICT governance is established through the ICT and enterprise strategic plans as a control framework to achieve and sustain strategic goals and objectives. ICT governance is completely interdependent with the ICT strategy.
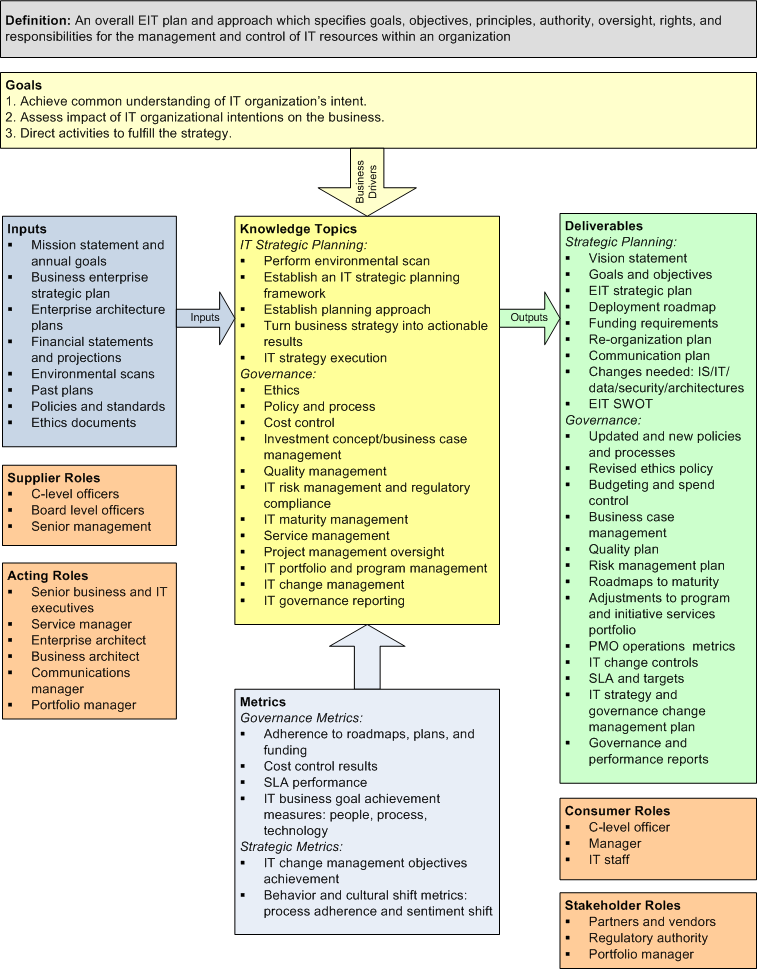
This chapter provides an overview of ICT strategic planning and governance including the approaches to create an ICT strategic plan based on enterprise strategy, and the role of the ICT enterprise architecture. The strategic planning and governance context diagram is shown in Figure 2.1.
2 Goals and Principles
- ICT strategy — To achieve a common understanding of ICT and enterprise intent:
- Enterprise strategy drives ICT strategy.
- Understand your purpose for creating an ICT strategy.
- Understand current ICT operations.
- Plan for working on the things that matter to enterprise.
- Take a multi-year perspective, and revisit the plan on a periodic basis for confirmation or changes.
- Enable reliable, nimble, and efficient response to strategic objectives.
- Sustain ICT capability.
- ICT governance — The goal of governance is to direct activities in a way that fulfills the ICT strategy. These are critical activities required to achieve this goal:
- Plan for flexibility and change in governance structure, accountability, and priorities.
- Measure progress and performance against the strategic roadmap as well as on a project and operations basis.
- Enable change, even to the plan itself, as required.
- Advise and align other ICT discipline strategic plans into an overall framework for delivery.
- Foster communications and understanding between ICT and enterprise.
- Set expectations within a code of ethics framework.
- Foster a continuous learning organization.
- Look ahead for continuity planning as part of risk management planning.
Figure 2.1: Strategy and Governance Knowledge Area
3 Description
Strategic planning occurs at different organization levels and on a lateral scope. Enterprise ICT strategy is developed by senior management supported by ICT standards, frameworks, and guides setting direction and mandating many ICT management activities. Goals and objectives depend on the type, status, and size of the enterprise. For example, the main goal of ICT development for a trading company may be to support the rate of turnover of the warehouse, but for a consulting company the important goal may be the efficient use of personnel.
The inputs to strategy and governance include various enterprise planning and strategy inputs, financials (budgets and plans and performance), and enterprise architecture and enterprise governance artifacts including policies.
The roles involved in supplying input to and drafting ICT strategy and governance include C-level executives, senior management, and certain specialists such as communications personnel and architects.
Deliverables from the strategic planning process include the strategic plan, the communication plan, and the socialization plan. They inform a governance framework necessary to deploy those plans in ICT. These deliverables are consumed by C-level executives and business and ICT management.
3.1 ICT Strategic Planning
3.1.1 Introduction: ICT Strategy is a Business Strategy
ICT is a business unit within the enterprise. The business strategy document is the most significant single input to the ICT strategy document. The business strategy frames the scope and expectations for the ICT strategy.
Any supply chain, outsourcing, onboarding, or other scenario that is practiced by ICT and the business should be driven out of strategy. For example, if the business chooses to streamline vendor relationships, the focus would be on a value stream called an onboard supplier, and capabilities that would include partner management, asset management, agreement management, and related capabilities that are supported by associated ICT capabilities in these areas.
The enterprise as a whole should have a shared strategy for addressing how to improve operations and ICT should participate in and leverage the results of strategic objectives and action items tied to these abstractions.
The resulting activities could involve consolidating and improving automation around this value stream and capabilities as well as numerous other non-technical activities that do not involve systems and technology. Specific topics may include best practices on:
- Outsourcing of systems, process, maintenance, technical risk management and transition approaches, cloud contracting advice, mobile strategies, data and information management and integration strategies, SLA framework strategies, logistical and business cultural constraints, and resource optimization options.
- ICT strategy is a component of an enterprise strategy when considering activities that include designing, building, and managing information and information technology for business change. [1]
3.1.2 Perform Environmental Scan
There are multiple ways to leverage the concepts portrayed in Figure 2.1. However, the process begins with strategy mapping.
Strategy mapping articulates a strategy in such a way that it can be readily interpreted and acted upon. Strategy maps vary but are essentially a graphical depiction of goals, objectives, and related courses of action, often aligned against an organizational and broader environmental backdrop.
Shifts in technology in the marketplace, regulatory change for transparency, corporate marketing channels, and competitor’s enterprise models are a few environmental considerations when building an ICT strategy.
A current assessment of ICT systems, capabilities, and resources is necessary to complete the full 360 degree scan.
ICT maturity assessment results are input to strategy mapping and desired outcomes (see Section 2.4.3 Maturity Management for overview of the assessment process).
Strategy mapping has existed in one form or another for some time. Sample strategy mapping approaches that apply to enterprise and ICT strategies are listed below:
- Strength/weakness/opportunity/threat (SWOT) analysis
- SWOT surfaces internal and external perspectives that should be capitalized upon or otherwise addressed. SWOT findings are one input to strategy formulation providing possible focal points in strategy development.
- The Norton Kaplan Strategy Map [2] links actions to value creation along four dimensions: financial, customer, internal (employees), and learning and growth. The strategy map offers a complete, in-context perspective on the strategy.
- Hoshin Kanri [3] provides similar cross-mapping concepts include tying mission, goals and objectives with action items, and key performance indicators (KPIs).
- The business motivation model (BMM) [4] provides a mapping between the ends to be achieved (i.e., goals and objectives) and the means (i.e., strategies and tactics) needed to achieve those ends.
Generally only one approach is selected for a strategy map. Regardless of approach taken, the end result of any strategic ICT planning process is a clear set of measurable objectives, priorities, and action items that management can then act upon to deliver change leading to improved ICT performance.
3.1.3 Establish an ICT Strategic Planning Framework
The strategic planning context diagram shown in Figure 2.1 provides a good focal point for strategic planning from a business, process, and ICT perspective. In practice, ICT strategy formulation incorporates business strategy as a fundamental driver.
ICT strategy is deployed by leveraging best architecture, design practices, and technologies. The tension between delivering systems that meet business objectives, particularly from a tactical perspective, must deliver solutions in a delicate balance between forward-looking tools and techniques, current practices, and pressures to implement quickly.
3.1.4 ICT Strategy Formulation
Drafting an ICT strategy requires alignment to enterprise and business strategies, measured adherence and compliance to ICT best practices, and governance. While enterprise and business strategies come from business, adherence to best practices falls within the ICT domain. Of course, best practices continue to evolve and differ from organization to organization and even project to project. Therefore, ICT faces the challenge of satisfying strategic business objectives through the application of evolving and situational best practices.
Best practice conformance can be difficult when ICT owns numerous systems that were designed and developed in a prior era. Sometimes we call these legacy or heritage systems, and, in most cases, these older systems suffer from challenges. These systems were typically developed using older technologies and their architecture often does not conform to modern design principles (e.g., SOA) or to the current business needs. Further, changing business architecture and rules overtime can lead to data and information quality issues. Lack of business alignment and data-quality issues are some of the more difficult and time-consuming issues to address.
ICT organizations typically address technical debt through legacy modernization (upgrade or replacement), but often do not tie these projects to strategic business objectives. Additionally, the costs are often high and the business benefits for continuing to deliver the same functionality as before upon completion of the project can be a hard sell to the business.
The following six-stage framework for ICT strategic planning ensures that business strategy is integrated into the planning process and that ICT strategy is not driven solely by technological upgrades:
- Craft the ICT strategy and plan to support well-articulated enterprise and business objectives.
- Leverage EA to feed the strategy. Vet various perspectives.
- Highlight ICT focal points for each objective.
- Establish KPIs for each strategic enterprise objective and related action item.
- Establish a plan timeline roadmap including a review plan.
- Establish or leverage ICT governance to ensure that business strategy is realized.
Each of the above ICT strategy development activities presents a unique challenge and occasionally can be in conflict. For example, adherence to best ICT architecture practices is difficult when older legacy systems that are architecturally inelegant must be updated to accommodate alignment to business strategy, or when time-to-implement constraints override preferred plans. When this occurs, the organization begins to build technical debt. Technical debt is defined as “the negative effects of applying ill-advised or problematic changes or additions to software systems and their data, negatively impacting the delivery of future business value.” [5]
The steps in the planning process, as depicted in the context diagram in Figure 2.1 should work for most organizations as they embark upon their business and ICT planning efforts, keeping in mind that the framework provides a guide into what should specifically be addressed at each stage of the planning process. Finally, much of what is considered as strategic planning within ICT is just a portion of the broader context for business planning. Therefore, planning for ICT and business scenarios that are essentially the same scenario, such as outsourcing a capability or managing suppliers, should take an integrated, holistic, and enterprise view of the planning process.
3.1.5 Establish Planning Approach
A defined ICT strategy provides the roadmap needed for getting from where the enterprise is at present to where it needs to be. It identifies how the enterprise needs to change. ICT must determine effective ways to take the enterprise strategy and transform it into ICT strategic change.
Strategic change employs a wide array of disciplines and techniques to enable change on a large scale and on an incremental basis. These techniques are often discussed in the context of types of focuses, such as: [6]
- Governance
- Information/data
- Solution
- Technology
- Security
Each focus has constraints that must be understood and reflected explicitly in the strategy. These typically include time, quality, and cost. The focus may also include organizational scope such as Western Hemisphere operations only, or a time horizon such as a 2-year horizon, as well as constraints from the environmental scan such as regulatory requirements for the industry. An ICT strategy also acknowledges existing ICT constraints through enterprise architecture (EA) and human resources, legacy systems, staff capability, and capacity to deliver.
The strategic planning team takes risk into account within the plan. They recognize the risk appetite of the organization as a potential constraint in the plan. They also suggest risk responses that require vetting and approval as part of overall strategy adoption.
3.1.6 Role of Architecture in Strategy Planning
Enterprise architecture (EA) informs the ICT strategic plan in a number of ways. EA supplies “a blueprint of the enterprise that provides a common understanding of the organization and is used to align strategic objectives and tactical demands.” [7]
Standard methods include strategy maps, capability maps, information maps, value maps, and organization maps.
Some other artifacts include operating models, product maps, stakeholder maps, process models, dynamic rules based routing maps, data models, network models, systems models, vitality and renewal plans, and a wide range of hybrid blueprints and models that have specialty uses based on the challenge at hand.
Blueprints and models are valuable to have as an input to the ICT strategic plan. Typically, many artifacts do not exist when initiating a strategic planning effort and either they must be developed together with business input. The ICT strategy document then becomes an extrapolation from the enterprise strategy with an ICT lens.
3.1.6.1 Blueprints and Models — Business and ICT
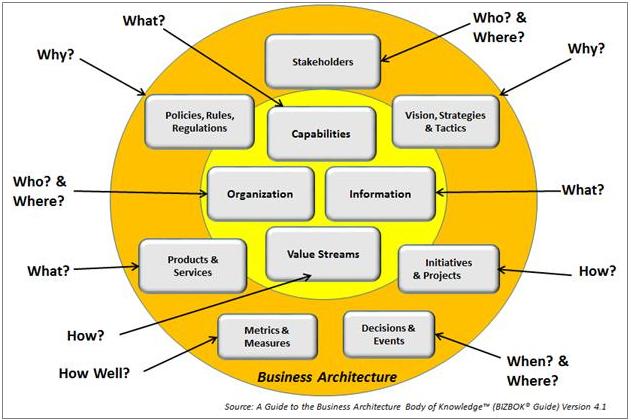
Blueprints and models require consistent, standardized components. These components draw from the abstract representations of the business shown in Figure 2.2. In the figure, the center circle represents concepts and includes capability, value, organization, and information. These concepts are considered core, because they are very stable business and ICT perspectives that remain relatively constant. Changes occur as required to accommodate business and ICT as they evolve. ICT inherits some of these blueprints from the Business and transforms them into aligned ICT focused forms.
The yellow circle in the figure shows influencing perspectives. For example, strategies continue to evolve in real time while new business and ICT products and services are introduced routinely. These examples show how the outer circle of business abstractions are more dynamic than the stable core. Collectively the core and extended views, when mapped and presented appropriately, provide a complete and holistic planning view.
Figure 2.2: Business Architecture Ecosystem [8]
Very sophisticated blueprint mappings can emerge from the collection of components shown in Figure 2.2, which represents the business ecosystem. Even simple concepts, like value stream or capability cross-mapping, serve as a basis for business-driven roadmaps and investment planning. Collectively, all of these perspectives answer important questions such as why take action, what is impacted, or how to accomplish a particular task.
3.1.7 Turn Business Strategy into Actionable Results
3.1.7.1 Using Blueprints and Models
The reason for developing the various blueprints and models is to use them in some way to achieve strategic and tactical needs. Strategy drives changes that can be collectively represented by abstractions depicted in Figure 2.2. When management has the ability to view the impact change using these abstractions, everyone from the executives and planning teams to the deployment teams can have a shared perspective of the context and scope of these changes.
For example, consider the goal to provide more customer and transactional transparency throughout the product sales cycle; where “transparency” across the sales cycle means visibility into transaction history and sales potential. Business architects would determine that this strategy targets the acquire product value stream and account file management, customer management, and account routing capabilities. Other enterprise and solution architects would then look at the goal from their delivery perspectives. These perspectives very likely are implemented today using a cross-section of technologies and processes, some of which are well understood and adaptive, while others are not. The ICT strategy together with EA provides a framework for assessing current state implementations, crafting target-state solutions, and establishing a transition strategy for moving from current-to-target state solutions.
There is a multitude of strategic planning approaches. Regardless of the approach selected, turning strategies into actionable results requires identifying the ICT delivery impacts on the current state and current future state plans.
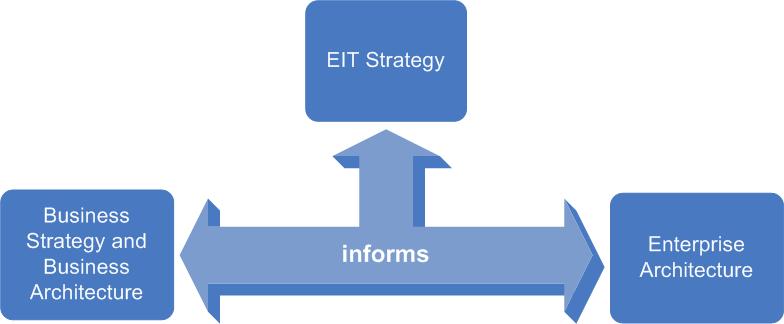
Figure 2.3: Turning Strategy into Actionable Results via Enterprise Architecture
Figure 2.3 represents the ability to leverage perspectives to identify specific areas of ICT that require initiative investment. These investments in turn result in projects that incorporate business and ICT transformations.
- Enterprise business strategy represents all motivational factors including policy, regulation, goals and objectives, product and stakeholder considerations, and the resulting action items required to achieve various goals and objectives.
- Enterprise IT strategy represents the ICT perspective of the enterprise business strategy and includes capability, capacity, ROI, information, organizations, responsibilities, funding plan, stakeholders, initiatives, products and decisions.
- Enterprise architecture identifies actionable items as inputs to design concepts, ICT business priorities, business-driven roadmaps, fundable initiatives, and business-driven ICT architecture transformation.
3.1.7.2 Using Enterprise Architecture to Interpret Business Strategy [9]
EA is both an input to the strategy by supplying methods and “as-is” architectures, and a follow-on activity that interprets, performs gap analysis, and supports execution the strategic plan and adjusts the “to-be” architectures to new or changed direction from the plan.
A brilliant business design can be too costly and take too long to satisfy executive demands, or can be technologically infeasible. This is where enterprise architecture can help ensure that selected business designs and innovation options are not only desirable, but cost effective and implementable.
We stated earlier that EA includes business, solution, information, and technology architectures. Business architecture has a direct relationship to and reciprocal impact on the remaining aspects of EA — particularly solution and information architectures. For example, information architecture leverages the information aspects of business architecture to craft a wide range of technology options for maximizing accessibility and usage to a various information categories. These range from “big data” to more traditional relational database architectures. Information architecture establishes the critical underpinnings for business automation solutions.
The solution architecture is the implementation perspective of the business architecture and includes business design concepts such as case management and process management. Business capabilities drive the evolution of applications and service oriented architecture (SOA) service deployments. Value streams provide the framework for service orchestration, business design options, and stakeholder interface requirements.
The technology architecture plays two important roles. First, it enables delivery of business solutions as articulated through the blueprints and models. Second, it ensures that the required degree of technological innovation is in place to maximize business solutions while ensuring stability, security, and business continuity.
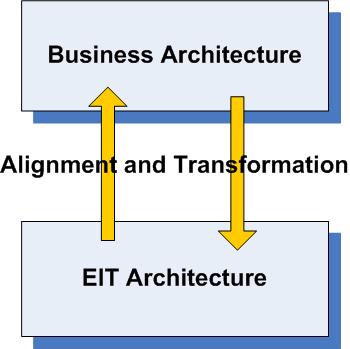
Figure 2.4: Business Architecture and Continuous Business/ICT Alignment
The two-way relationship between business architecture and solution, information, and technology architecture is depicted in Figure 2.4. Continuous business/ICT alignment reflects the value of maintaining these interdependent relationships across business and ICT. A change in any one of these aligned layers should be transparent, duly assessed to determine reciprocal impacts, clearly linked to a specific business objective, and addressed through a funded initiative.
Business needs, mapped appropriately to ICT current and future ICT plans, ensures that business objectives are known, quantified, clearly articulated, and linked to business value. Conversely, any ICT investment must equally demonstrate a link back to business value. For example, an application change may require significant funding. Architects should be able to trace the planned application process changes back to the business capabilities, value streams, and information it implements, and back to business objectives and link the change to value. A network planning team, for example, should be able to trace the usability of that network up the chain, through the solution architecture and directly into the business architecture. In this way, all technology ICT activities can be tied back to business impacts, and business strategy.
Business architecture not only helps identify change impacts and investment focal points derived from a given business strategy, but also provides a basis for business design and innovation analysis.
Consolidated platforms (CP) are emerging as multi-vendor pre-packaged solutions that can be efficient use of resources in operations and release management activities with the providers in an oversight role; however, evaluating the detailed solution for suitability and viable exit planning becomes more complex. CP can be seen as a mid-way solution between complete solution insourcing and complete outsourcing.
3.1.8 ICT Strategy Execution
Poor strategy execution is the most significant management challenge facing public and private organizations in the 21st century according to Gartner (Lapkin & Young, 2011).[10]
Figure 2.5: Change Initiative Flow Chart
All strategies must be grounded with the following rigorous practices:
- Outline the means for achieving desired outcomes:
- Specify timeframes and business scope that reflects needs and priorities.
- Link all ICT strategies to business goals and objectives.
- Create and support a means to generate and capture ideas for innovation and change, and their evaluation.
- Support change management processes with top down and bottom up validation.
- Provide properly scaled strategies for business problems.
- Acknowledge and propose change within known constraints and risks including staffing capability and EA plans.
- Refer to existing funding and planning engagement processes to move the strategy into portfolios and projects.
- Create or refer to control processes an organizations that can give oversight to strategy execution (are we doing the right things and are the right things being done well?)
- Ensure that the strategy is a living document and game plan:
- Give targets for strategy achievement and specify reporting to an oversight body.
- Create and live a culture of collaboration between business and ICT through specification of communications and training plans and change management support.
- Provide adequate and sustained funding.
- Propose active monitoring and adjustment of the strategic plan with renewal cycles.
3.2 Governance
ICT governance establishes a conformance process and authority to make sure the strategic plan is executed. ICT governance accomplishes this by setting into place policies that mandate the instigation of controls in all areas of ICT including cost controls reporting, project oversight, service management, risk assessment and management, ethical behaviors, and change control. All of these controls fit within a framework of overall organization controls and policies, and are aligned to them.
To ensure full engagement across the business/ICT boundary business and ICT executive sponsors provide oversight for ICT governance. ICT governance must set expectations at all levels in ICT for compliance using an enterprise and local interaction model for monitoring, guiding, and reporting. The following guidelines will help in this process:
- Understand and work through the people side and the organizational side of proposed change and existing culture impacts. This is critical to the long-term success of strategy implementation and oversight (governance) efforts.
- Establish business/ICT collaboration and communication governance model.
- Ensure that open communication and collaboration from a business-to-business, business-to-ICT, and across ICT perspectives.
- Establish collaborative principles, measurements, and escalation procedures as required.
- Ensure that external regulations and laws, market perspectives, and external perspectives are included.
Lines-of-ICT business have their own special concerns that align to overall governance objectives, such as:
- Security — for example, local objectives and measures for blocking threats
- Data — for example, prioritizing key financial data for accuracy in transactions
- Application — for example goals for availability
- Enterprise architecture — for example, overall ICT strategy realization
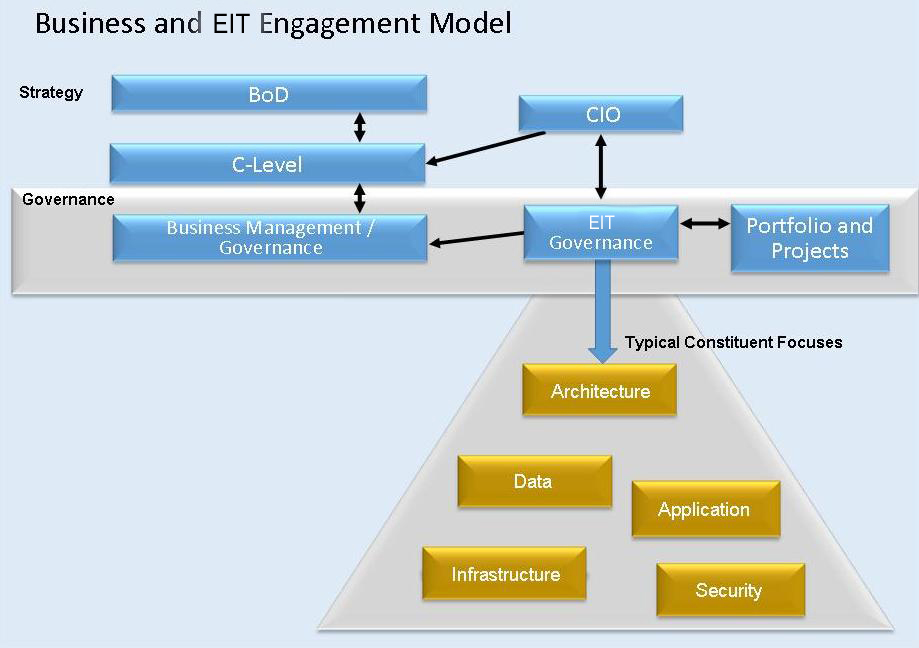
Figure 2.6: Example of a Business and Governance Engagement Model
Business staff participate at all levels as stewards or subject matter experts in areas such as legal, marketing, manufacturing requiring the ICT services, as they set priorities locally that in turn set targets and thresholds for ICT performance.
Enterprise architecture domain experts in application, data/information, infrastructure and business provide coaching to work teams on an as-needed basis and are the front-line representatives for ICT governance.
3.2.1 Governance Benefits Assessment Realization
Businesses with superior ICT governance record 25 percent higher profits than those with poor governance. [11] This type of positive value assessment for ICT governance is well established and clearly maps to ICT governance objectives of reliable, trusted, responsive and evolving ICT synced to business plans and needs.
ICT audits are a specialized type of monitoring that challenges the self-reporting on governance metrics by performing direct assessment. [12] Some topics that an audit may cover include:
- ROI
- Data quality
- Inventory of licenses, hardware in use/owned
- Process performance assurance, rationalization, adherence as required from asserted levels of organization maturity
- Security assurance
- Maturity assessment/reassessment
- Regulatory requirements adherence self-assessment of ICT governance
- Overall assessment of ICT
The resulting reports include gaps found and remediation recommendations.
As a line management and also a virtual organization, the costs to establish and operate ICT governance can be scaled to meet the strategically sensitive areas for the overall organization. Business and ICT share the ICT governance responsibility together. Good governance requires exceptional leaders who can communicate across business and ICT subject domains.
The value of ICT assets may not regularly included on balance sheets, however ICT governance will be asked to participate in a valuation at a time of mergers, acquisitions, and liquidations.
3.2.2 Ethics [13]
Ethical behaviors in an organization are judged relative to their cultural and regulatory framework. In some countries, money paid to gain business advantage is neither unethical nor illegal.
- Ethical assertions should be expressed in ICT, tied to the overall business code of ethics, and signed off by all staff so that violations can be cause for reprimand or dismissal.
- Vendors should be held to similar ethical standards.
- A code of ICT ethics is created, and socialized.
- Lists of employees who have signed-off on the code are maintained by ICT governance.
Some ICT ethical topics include those that may also be illegal, such as:
- Consideration of the social impact of the work at hand — will it cause harm
- Alignment of business and ICT strategies and policies to an ethical standard
- Incorporation of the ideals of professionalism
- Adherence to applicable regulatory intent
- Whistle-blower protection
Call out these things specifically:
- Activities that interfere with or corrupt the proper function of computers, applications and systems
- Activities that interfere with others digital privacy, or intellectual rights
- Respect for confidentiality, privacy, permissions, and access rights
- Inappropriate bias (skewing) of analysis and reporting
- In-action in the face of likely ethics violations
3.2.3 Policy and Process
ICT governance can create numerous policies and processes to establish overall control, or can establish only a few that will drive action in various delivery areas to create and maintain their own local aligned policies and processes. Determination of the right fit for control should be based on risk assessment by ICT governance and resulting level of oversight that should be maintained. For example, security policies and processes should typically be set centrally so all areas of the company are measured on exactly the same basis and changes are uniformly applied. Decentralization and therefore more coordinated information management policies and processes may be acceptable in a business that is more product oriented than service (data) oriented.
Even at the initial phase, an overall ICT governance policy, driven from an enterprise policy, is required to establish its authority.
3.2.4 Cost Control
Cost control is a central activity in ICT Governance. ICT products and services are bundled into operations sustainment, major projects, and small changes Business cases for the work are budgeted, prioritized, and funded. See also Change Initiatives.
The business sets priorities for development and operations. Those priorities must consider the factors in the strategic environmental scan. For example, to ensure rapid expansion of business geography plans, methods and designs may be adopted that diverge from the formal ICT strategies realizing cost savings. The cost control priority can be important overriding priority that guides possible easing of EA visions and plans for of controlling overall ICT system evolution, but at the risk of mounting technical debt.
TCO improvements can be addressed by careful application of strategies, such as:
- Infrastructure allocation/management
- Application rationalization
- Device and data access policies
- Process assessment (identification of wasted effort)
- Application lessons learned
- Feedback loops
- Process improvement/re-engineering
- Licensing re-negotiation
- Various outsourcing initiatives
3.2.5 Investment Concept/Business Case Management
Outside all operations and sustainment work all activities are proposed through a standard funding process as in Figure 2.7.
File:Http://eitbokwiki.org/File:Figure2.5.JPG
Figure 2.7: Steps in Business Case Development
Work is prioritized and moved forward into the realization phase based on the business and ICT strategic plans within Chapter 4, Change Initiatives. The process is monitored for continuing business alignment and need, feasibility factors, stakeholder interest, resourcing opportunities, competitor activity, new ICT tools and approaches, and government requirements on the industry. All of these factors influence the speed at which concepts move through the process or even get dropped entirely from the plan.
Contract management with vendors including outsourcing, licensing, SLA, OLA, cloud computing, project resourcing is also the responsibility of ICT governance (see also Chapter 9, Acquisition).
3.2.6 Quality [14]
Quality is a key control in ICT governance that is manifested across all policies, processes and procedures. Generally there are two ways of approaching quality. The first is to take a passive approach; in effect to adhere to the idea that quality is “baked in” to the organization through the policies, processes, and procedures, and where quality controls are established as an output measurement much like in manufacturing environments. The second approach is more active setting out a separate responsibility for quality that establishes responsibility, checks adherence, and advises and reports on quality risk and failures along many points along work streams.
Best practices adoption are an indication of a more mature organization requiring active quality assurance management as part of overall ICT governance. For example, Quality standard ISO 9001 applies when an organization:
- Needs to demonstrate its ability to consistently provide product that meets customer and applicable statutory and regulatory requirements.
- Aims to enhance customer satisfaction through the effective application of the system, including processes for continual improvement of the system and the assurance of conformity to customer and applicable statutory and regulatory requirements.
Monitoring and performing impact analysis of regulatory and changes in industry standards is also a quality assurance activity shared with legal and enterprise architecture.
An organization can, address information leakage and misinterpretation with accompanying risk for regulatory and customer exposure to reputation and even fines by adopting data quality assurance stemming from a data governance program. [15]
The following ICT functions (Sections 2.2.3-2.2.7) all have quality dimensions to their activities. See also Chapter 6, Quality.
3.2.7 ICT Risk Management and Regulatory Compliance [16]
ICT policies, standards, and processes all deal with risk to some degree. Policies typically include explicit sections on risk approaches that the organization wants to adopt including any of: ICT security policy, ICT governance policy, ICT financial management policy, data privacy and classification policy, disaster preparedness policy, supply chain management, vendor management, employee ethics, and regulation adherence policy. Risk management in ICT involves the following activities:
- Risk identification — Relevant ICT risk profiles on systems are specified. Types of risks are financial, reputational, regulatory (projected and current), security, ICT disaster, market innovation speed, and supplier performance.
- Risk evaluation — All identified risks are evaluated for their severity and likelihood.
- Risk response — Response plans are generated for the most severe and likely risks. Generally, the response is either to accept the risk and do nothing because likelihood or organization concern is low, to accept the risk and plan contingencies for the occurrence, or to transfer the risk to a third party via insurance.
3.2.8 ICT Maturity Management [17]
The maturity of ICT functions directly relates to the ability to execute the ICT strategy therefore there is a need to assess maturity as an input to a realistic plan and as a guide to maturing ICT to desired levels. In other words, unless the ICT organization understands its own needs and abilities, it can’t make plans to do more or to improve. The adoption of lessons learned is a key improvement strategy.
Some principles in mounting and actioning maturity assessments are:
- Business and ICT culture and interaction are key elements to capability and performance and cannot be ignored in an evaluation.
- Outputs of the maturity analysis are direct inputs to planning and the strategy plan execution roadmap.
Maturity assessment involves scoring against criteria and a ranking scheme; generally organized in ascending steps with strategies on how to move up the maturity scale. Scales are often 1-5 and indicate increasing levels of maturity. Some schemes allow for scoring that includes decimal points (e.g., 2.5).
- Performed: Activities are performed in an ad hoc manner
- Managed: Activities are performed with managed processes
- Defined: Activities are defined so the organization can performed them in a uniformed manner
- Measured: Oversight to the performed activities to ensure performance and uniformity
- Optimized: Continuous improvement processes are in place on the defined and measured processes
Periodic reassessments are performed in order to gauge progress against the baseline assessment and prior periods. Adjustments to the efforts to maintain and improve maturity can then be made against possible strategic priority changes, governance initiatives, and roadmap resets.
Maturity assessment on internationally recognized frameworks generally involve external auditors with certification and recertification requirements. Engagement in the maturity assessment and improvement process requires a minimum level of organization self-awareness to the issues and commitment to the improvements necessary. A cultural readiness, resistance, and capability assessment may be built into a maturity assessment.
- Bodies of Knowledge guides exist as capability and light maturity assessment frameworks many of which are referenced EITBOK.
CMMI [18] is standard reference model for process improvement with cross sector applicability with special focuses:
- Product and service development — CMMI for Development (CMMI-DEV)
- Service establishment, management, — CMMI for Services (CMMI-SVC)
- Product and service acquisition — CMMI for Acquisition (CMMI-ACQ)
- Data management — CMM for Data (CMM-DMM)
When reviewed and areas prioritized by management, a maturity assessment is an input to ICT roadmap development for change.
Organizing and communicating for change in order to move up the maturity scale is managed by ICT governance.
ICT governance also provides reality checks on the goals and timing to the desired objectives as materialized through ICT change initiatives. (See also Chapter 3, Change Initiatives).
3.2.9 Service Management [19]
Service management in ICT has its own strategic plan encompassing the full system life cycle support from concept to deployment and retirement. It is the ICT function that designs and implements control structures within the ICT governance framework including:
- Service strategy — demand and financial management for service portfolio management ***xref general ICT strategy***
- Service Design — Enterprise Architecture, Requirements, and Design and Construction chapters
- Service Transition — Transition chapter
- Service Operations — Operations chapter
- Continual Service Improvement — measurement, monitoring, reporting including monitoring for compliance, financial performance, monitoring customer and employee satisfaction
3.2.10 Project Management Oversight [20]
Project management is an integral part of ICT governance, and a requirement for all change initiatives in ICT including new projects, enhancements, upgrades, and significant operations changes. These include traditional ICT activities as well as supporting activities such as communications and human resources.
ICT governance mandates that project-level controls are initiated and sustained at a level appropriate for the scale of the work that satisfies ICT governance reporting requirements. Required project-level controls include quality, cost, risk, schedule, deliverables, process, and authority.
- All ICT activities require a planning horizon and it is ICT governance that assures that the adequate resources (including staff, material and funding) are available to approved activities in a timely manner. In this way, ICT governance at the CIO-level works closely with vendors, project managers, financial management staff, and suppliers to achieve these aims.
- The Project Management Office supports a subset of all projects. This formal oversight body is setup to instantiate best repeatable practices in project management and to assist in reporting status. PMO scope is usually limited to those projects holding significant risk to the organization, and/ or significant cost.
3.2.11 ICT Portfolio and Program Management
Reporting and oversight is also applied to aggregates of projects into portfolios and programs. ICT Portfolios are a set of scoped applications and systems that are closely interrelated; for example, the accounts payable, accounts receivable, and ledger production in an organization. Programs may span portfolios as multi-phase, multi-year initiatives. Project and portfolio grouping allows for more holistic views on change, impact analysis and synergies, business case development, upgrading, operations problem identification, communication and recovery, vendor and business relationship management and multi-project oversight.
Portfolio managers work closely with project managers, architects, operations managers and business users to make sure the relationships and understanding between the business and ICT are strong and transparent.
Programs can affect multiple portfolios and often have their own multi-year separate organization structure and board level interest and oversight. In this way, activities are:
- A new layer of activity, which introduces broader change that impacts large parts of existing ICT through replacement, incremental improvements, and significant new approaches, such as mobile application, CP, and cloud computing.
- Geared tightly to high business priorities and strategies. Every program is directly linked to achieving specific business (and by inheritance ICT strategy) goals and objectives.
3.2.12 ICT Change Management [21]
The change management function exercises authority to introduce change into the ICT environment and is the responsibility of both the business and ICT. Governing change management activities occur at varying levels of detail depending on the nature of the change. Any change, whether a commissioning of a new system, an application enhancement, a sustainment activity to maintain operations or corrective action to repair a defect, is approved through governance processes.
- Changes may be at the strategic re-alignment level as plans and architecture responses move to adjust projects and programs that are prioritized or in-flight, including the possibility of activity shutdown.
- Changes may be at the operational level, where a Change Control Board or Change Advisory Board approves code or systems, or data changes into the production environments and can include planned and unplanned (emergency) changes, projects and releases.
- Incidents occurring from change handling activities are reported to ICT governance for possible response particularly if additional funding is required for corrective action. Other incident handling occurs at a more local response level.
- Change patterns are monitored and advice on adjustments to programs and procedures are generated for ICT governance consideration.
Chapter 11, Transition, discusses both project and release management including the preparation of the environment prior promotions into production operations.
3.2.13 ICT Governance Reporting
Governance reporting keeps an eye on strategic themes, potentials for intervention on processes and projects at-risk and offers opportunities for supported learning and improvement underperforming areas. Appropriate accountability drives change and control authority and can assure that active oversight is in place for handling of possible performance penalties to third parties. See also Chapter 9, Acquisition.
- Build feedback or action model to ensure that issues are addressed quickly. Review and remediation actions are authorized at the appropriate level.
- Typical ICT governance reporting consists of interval reports to C-level officers in a steering committee, oversight committee, or operations committee with measures of performance and issues from the governance management streams described in brief. Reporting at a board of directors level integrates a smaller set of measures from ICT governance.
Metrics [22] standardize the reports and allow tracking of progress over time. Some metrics can be characterized as KPI that are of special significance to ICT and business as they are considered to best support the highest priorities.
- General themes are based on strategic plan, project and operations demands:
- Adherence to action plan and funding
- Goal achievement measures (e.g., balanced scorecard)
- Plan execution achievement
- Organization change
- Financial position trending, demand forecast
- Outstanding work tickets
- Emergency preparedness /disaster drills results
- Quality scorecard
- All metrics should have measurable targets. There are a number of reporting approaches; with scorecard approach being the most common. [23]
- Participant reporting from ICT areas often have more stringent targets set in order to assure higher level aggregate successful target achievement overall. Participant reporting may also combine with other lateral participant reporting metrics in an additive or algorithmic manner to construct higher level metrics and measures.
It is becoming common for senior managers to have compensation in part or in-whole driven by these performance measurement results.
4 Effective Strategy and Governance
ICT governance is effective only if cultural and management buy-in are deeply established and carried on in a continuous manner to the appropriate level of management with a communication plan, however that is not even enough to assure governance success. Reasons for ineffective governance include:
- Compliance activities and reporting without any review, action or consequences
- Poorly designed engagement model
- Uneven authority in governance oversight
- Ineffective delegation of authority
- Untimely actioning of governance issues
- Poorly thought out governance metrics (measuring the wrong thing, or encouraging the wrong activities)
- Inaccurate data collection and spotty reporting
- Drifting from the enterprise and business strategies over time so that governance is mis-focused
5 Relevant SFIA Skills
- Business Architecture Team — Enterprise and business architecture development — Business strategy and planning
- Business Management Team — Business modeling — Business change management
- Data Management Team Data management — Technical strategy and planning
- User Experience Team User experience evaluation — Human factors
- Internal Messaging Team Information management — Information strategy
- Solution Management Team Enterprise and business architecture development — Business strategy and planning
6 Roles
- Board of Directors
- C-Level Officer
- Business Partner
- Architect
- Governance Body
- Regulatory Authority
- Stockholder
- Vendor
7 Standards
The list of IEEE CS standards is at https://computer.centraldesktop.com/itbok/folder/3895640/#folder:4137641
If you have questions about the standards, ask Chuck.
Commonly used risk standards include:
- ISO 31000 2009 — Risk Management Principles and Guidelines
- A Risk Management Standard — IRM/Alarm/AIRMIC 2002 — developed in 2002 by the UK’s 3 main risk organizations
- ISO/IEC 31010:2009 — Risk Management — Risk Assessment Techniques
- COSO 2004 — Enterprise Risk Management — Integrated Framework
- OCEG “Red Book” 2.0: 2009 — a Governance, Risk and Compliance Capability Model
8 References
[1] See also Control Objectives for Information and related Technology (COBIT)
[2] R. S. Kaplan and D. P. Norton, Strategy Maps: Converting Intangible Assets into Tangible Outcomes (Boston: Harvard Business School Press, 2004)
[3] www.hoshinkanripro.com
[4] Business Motivation Model (BMM), www.omg.org/spec/BMM
[5] “A Guide to the Business Architecture Body of Knowledge” (BIZBOK® Guide), Release 4.1, Glossary, Business Architecture Guild, www.businessarchitectureguild.org
[6] Adapted in part from A Common Perspective on Enterprise Architecture, The Federation of Enterprise Architecture Professional Organizations (FEAPO), 2013, www.feapo.org
[7] OMG Business Architecture Special Interest Group, http://bawg.omg.org, and Business Architecture Institute, www.businessarchitectureinstitute.org
[8] “A Guide to the Business Architecture Body of Knowledge” (BIZBOK® Guide), Release 4.1, Section 1, Introduction, Business Architecture Guild, www.businessarchitectureguild.org
[9] Enterprise Architecture as Strategy: Creating a Foundation for Business Execution. Peter Weill and Jeanne Ross, Harvard Business School Press, 2006.
[10] A Common Perspective on Enterprise Architecture, The Federation of Enterprise Architecture Professional Organizations (FEAPO), 2013, www.feapo.org
[11] IT Governance: How Top Performers Manage IT Decision Rights for Superior Results Hardcover. Peter Weill and Jeanne Ross, Harvard Business School Press, 2004.
[12] See also ITGC — IT Global Controls - Global Technology Audit Guide (GTAG), Institute of Internal Auditors
[13] See also IEEE Code of Ethics, ACM Code of Ethics and Professional Conduct as examples
[14] See Also Control Objectives for Information and related Technology (COBIT)
[15] See also DAMA-DMBOK Guide to the Data Management Body of Knowledge (DAMA-DMBOK), Chapter 4 Data Governance
[16] See also IT Risk Management guidance - ISACA
[17] See also Capability Maturity Model (CMM) and Capability Maturity Model Integration (CMMI) for assessing primarily software development processes, but can be applied to other processes.
[18] Capability and Maturity Model Integration
[19] See also Information Technology Infrastructure Library (ITIL)
[20] See also Project Management Institute, Project Management Body of Knowledge guide (PMBOK)
[21] For Change Management guidance — Project Management Body of Knowledge Chapter 4 Version 5 December 31, 2012
[22] Metric is the algorithm or mathematical and logical description of how measurement are to be taken. A measurement or measure is a score given at a point in time on that metric.
[23] R. Kaplan and D. Norton, Using the Balanced Scorecard as a Strategic Management System, July 10, 2015, https://hbr.org/2007/07/using-the-balanced-scorecard-as-a-strategic-management-system